Cybersecurity & Functional Safety: A Deep Dive into IEC 61511 Clause 8
The second edition of IEC 61511 elevates cybersecurity into the heart of the safety lifecycle. This interactive guide explains what Clause 8 requires, why it matters, and how to implement it across design, operation, and maintenance — with practical tools, checklists, and block diagrams.
Executive Summary
Why now? As SIS become networked and programmable, malicious threats can undermine protective functions. IEC 61511:2016/Ed.2 responds by mandating a cybersecurity risk assessment of the SIS within Clause 8.
- Scope: Logic solvers, sensors, final elements, connected HMIs/ES, plus interfaces to control/enterprise networks.
- Lifecycle: Threats must be assessed from design through decommissioning.
- Outcome: Cybersecurity requirements integrated into the Safety Requirements Specification (SRS) and verified via FSA.
The Paradigm Shift: Why Cybersecurity matters for Functional Safety
Functional safety focuses on controlling random hardware failures and systematic design faults so that safety instrumented functions (SIFs) work when demanded. With digital OT/IT convergence, intentional cyber threats can now degrade, inhibit, or spoof those functions. That changes the risk picture: keeping people, environment, and assets safe now also depends on security.
New Vector of Risk
Attackers can target the SIS itself (logic solver, I/O, final elements) or supporting assets (engineering workstations, HMIs, historian, gateways). A single change in logic or configuration can neutralize protection layers.
Clause 8 Adds Cybersecurity
IEC 61511 Ed.2 requires a cybersecurity risk assessment of the SIS during hazard & risk assessment and throughout the lifecycle. Outputs become SRS cybersecurity requirements and design constraints.
Integrated Approach
Security and safety are intertwined: a security weakness can create a safety hazard; a security control can affect availability. Manage both together using defense‑in‑depth and lifecycle governance.
What Clause 8 Requires
- Perform a cybersecurity risk assessment of the SIS to identify vulnerabilities (8.2.4).
- Consider connected devices and interfaces (engineering/HMI/asset management, control networks, remote access).
- Apply the requirement across the entire SIS lifecycle: design, implementation, operation, maintenance, and decommissioning.
Tip: Use ISA/IEC 62443 (zones, conduits, SR/SL) to structure the assessment and derive controls suitable for the SIS context.
Run Safety & Security Risk Activities in Parallel
Integrate cybersecurity analysis with PHA/HAZOP so that threats (e.g., unauthorized change, malware, DoS) are evaluated for their impact on SIF performance (spurious trip, failure to trip, incorrect setpoints).
- Identify threats, vulnerabilities, consequences, and existing protections.
- Estimate likelihood and consequence under credible scenarios; determine residual risk.
- Define additional safeguards and requirements to reduce risk ALARP and support SIL targets.
Put Cybersecurity into the Safety Requirements Specification (SRS)
The SRS must capture cybersecurity constraints and quality attributes for each SIF and the SIS platform. Suggested headings:
- Network zoning & segmentation (SIS network isolation, DMZs, one‑way links).
- Access control (RBAC, MFA, least privilege, engineering lockout, bypass governance).
- Hardening (services, ports, default credentials, media controls, application whitelisting).
- Secure remote access (brokered, authenticated, time‑bound, recorded, approved).
- Monitoring & logging (time sync, tamper‑evident logs, alerting thresholds).
- Resilience (backup/restore, cold standby, manual fallback, hold‑last‑state).
- Patch & change management (offline validation, MoC, rollback plans).
- Secure SDLC (configuration management, code review, threat modeling for logic).
Defense‑in‑Depth for a Safety Instrumented System
Combine prevent, detect, and respond controls across layers — from policies and people to physical, network, host, application, and data.
- Zone/conduit design with dedicated SIS zone, minimized trust, and strictly governed conduits.
- Firewalls & allowlists; no direct path from internet/enterprise to SIS.
- Role‑segregated engineering and operator accounts; session recording for critical changes.
- Application whitelisting on ES/HMI; removable‑media control; signed firmware only.
- Security monitoring aligned to safety alarms; joint triage playbooks.
Secure Operation & Maintenance
- Ongoing monitoring: baselines for logic, configuration, and comms; integrity checks.
- Patch management: vendor bulletins triaged; offline testing on representative hardware; windows coordinated with safety risk.
- Change management: MoC evaluates both safety and security impact; dual approvals; post‑change validation.
- Incident response: integrate with plant emergency procedures; predefined isolation steps for SIS zone; cyber‑forensics only after safe state is assured.
- Periodic reassessment: repeat cybersecurity risk assessment; validate assumptions and threat intel.
FSA & Lifecycle Integration
Functional Safety Assessments (FSA) should verify that cybersecurity requirements are defined, implemented, and maintained, and that they support SIF availability and integrity claims.
- FSA Stage 1–5 evidence includes: risk assessment records, SRS security sections, design verifications, factory/site test records, operations procedures, and audit trails.
- KPIs: unauthorized change attempts, configuration drift, patch SLAs, mean time to detect/respond, proof‑test anomalies linked to security.
Block Diagrams
SVGs are embedded and scale crisply for printing and PDF export.
Diagram 1 — Integrated Functional Safety & Cybersecurity Risk Assessment
Diagram 2 — Defense‑in‑Depth for a SIS
Diagram 3 — Integrated Functional Safety & Cybersecurity Lifecycle
Interactive Tools
Cybersecurity Risk Assessment Checklist (Clause 8.2.4)
Tick items as you complete them. Export your checklist as JSON for records/FSA evidence.
SRS Cybersecurity Insert Generator
Generate a tailored paragraph to insert under the SRS for a SIF or the SIS platform.
Mapping to ISA/IEC 62443 (Zones, Conduits, Requirements)
Use this as a quick reference when you derive SRS security content from Clause 8 outcomes.
| Area | IEC 61511 Focus (Clause 8) | Helpful 62443 References |
|---|---|---|
| Zones & Conduits | Identify SIS as a distinct security zone; minimize conduits; govern all data flows. | 62443‑3‑2 (Risk assessment & zone/conduit design), 62443‑3‑3 (SR/SL requirements) |
| Access Control | RBAC, MFA for engineering, least privilege; authorization for bypass/override. | SR 1.x (IAC), SR 2.x (UC), SR 7.1 (least privilege) |
| System Integrity | Hardening, signed firmware, whitelisting, integrity baselines. | SR 3.x (SI), SR 7.6 (application allowlisting) |
| Data Confidentiality | Encrypt sensitive conduits; protect credentials and keys. | SR 4.x (DC), SR 1.13 (MFA details) |
| Restricted Data Flow | DMZ; one‑way links; no direct enterprise–SIS routing. | SR 5.x (RDF), SR 3.1 (network segmentation) |
| Timely Response | Monitoring & alarms aligned to safety; incident response linked to safe state. | SR 6.x (TRE), SR 7.8 (event logging) |
| Resource Availability | Resilience: backups, hold‑last‑state, manual fallback, controlled patches. | SR 7.x (RAF), SR 7.3 (backup/restore) |
RACI & Governance
Clarify who is Responsible, Accountable, Consulted, and Informed for key activities.
| Activity | Process Safety | I&C Engineering | OT/IT Security | Operations | Vendor |
|---|---|---|---|---|---|
| Cybersecurity risk assessment (SIS) | C | R | A | C | C |
| Define SRS cybersecurity content | C | R | A | C | C |
| Defense‑in‑depth design | C | R | A | C | C |
| Security testing at FAT/SAT | I | R | A | C | R |
| Patch & change management | I | C | A | R | C |
| Monitoring & incident response | I | C | A | R | C |
| FSA security verification | A | C | R | C | I |
Adjust R/A/C/I to your site’s governance; the matrix above is a starting point.
Frequently Asked Questions
Is Clause 8 only about adding firewalls?
No. It is about assessing risk to the SIS, then defining requirements that may include network controls, host controls, process/people controls, and lifecycle governance — all captured in the SRS and verified through FSA.
Do we need a separate cyber assessment team?
Use a cross‑functional team: process safety, I&C, OT/IT security, operations, and vendors. The assessment should run alongside PHA/HAZOP so security insights inform SIF design early.
How do we evidence compliance?
Keep records: risk assessment worksheets, SRS security sections, design reviews, FAT/SAT security tests, MoC/patch logs, monitoring & incident records, and FSA reports.
Will security controls reduce availability?
Not if engineered correctly. Specify resilience requirements (e.g., hold‑last‑state, manual fallback), and test to ensure security controls do not impair the safety function.
Cybersecurity and Functional Safety: A Deep Dive into IEC 61511 Clause 8
The convergence of operational technology (OT) and information technology (IT) has brought unprecedented efficiency and connectivity to the process industry. However, this digital transformation has also opened a new Pandora’s box of threats. Cyberattacks, once the preserve of the IT domain, now pose a significant risk to the safety and integrity of industrial processes. Recognizing this critical challenge, the second edition of the international standard IEC 61511, “Functional safety – Safety instrumented systems for the process industry sector,” introduced a groundbreaking requirement in Clause 8: the mandatory consideration of cybersecurity in the functional safety lifecycle. This blog post will delve into the intricacies of Clause 8, exploring the crucial intersection of cybersecurity and functional safety, and provide practical guidance, complete with block diagrams, on how to address its requirements effectively.
The Paradigm Shift: Why Cybersecurity Now Matters for Functional Safety
For decades, functional safety, as defined by standards like IEC 61511, has been the bedrock of risk reduction in the process industry. Its primary focus has been on ensuring that safety instrumented systems (SIS) reliably perform their intended functions to prevent or mitigate hazardous events. The traditional approach centered on random hardware failures and systematic faults in design and engineering.
However, the increasing reliance on programmable electronic systems and networked components has introduced a new vector of risk: malicious and intentional threats. A cyberattack targeting a safety instrumented system could have catastrophic consequences, potentially leading to the very disasters the SIS was designed to prevent. This realization prompted the International Electrotechnical Commission (IEC) to explicitly integrate cybersecurity into the functional safety framework.
Unpacking IEC 61511 Clause 8: More Than Just a Hazard and Risk Assessment
Clause 8 of IEC 61511, titled “Hazard and risk assessment,” outlines the initial and arguably most critical phase of the safety lifecycle. It mandates a systematic process to identify hazards, analyze their risks, and determine the necessary risk reduction measures. The second edition of the standard brought a pivotal addition within this clause, specifically in sub-clause 8.2.4, which states:
“A cybersecurity risk assessment shall be performed to identify security vulnerabilities of the SIS.”
This single sentence has profound implications. It elevates cybersecurity from a secondary IT concern to a primary process safety consideration. It dictates that a thorough assessment of cybersecurity vulnerabilities is no longer optional but a mandatory prerequisite for achieving functional safety.
This cybersecurity risk assessment must consider:
The SIS itself: This includes the logic solver, sensors, and final elements.
Connected devices: Any device that communicates with the SIS, including operator workstations, engineering stations, and other control systems.
The entire lifecycle: Vulnerabilities must be assessed throughout all phases, from design and implementation to operation and maintenance.
The Symbiotic Relationship: Functional Safety and Cybersecurity
Understanding the interplay between functional safety and cybersecurity is crucial for effective implementation of Clause 8. While they are distinct disciplines, they are fundamentally intertwined in the context of modern industrial control systems.
Shared Goal: Both aim to prevent catastrophic events and protect people, the environment, and assets.
Different Focus: Functional safety primarily addresses random and systematic failures, whereas cybersecurity focuses on intentional and malicious threats.
Interdependence: A compromise in cybersecurity can directly impact functional safety. For instance, a hacker could alter the logic in a safety controller, rendering a safety instrumented function (SIF) inoperable during a critical demand. Conversely, poorly implemented security measures could hinder the performance or availability of the SIS.
This symbiotic relationship necessitates a holistic approach. Siloed assessments are no longer sufficient. A truly robust safety strategy requires the integration of cybersecurity considerations at every stage of the functional safety lifecycle.
A Practical Guide to Implementing IEC 61511 Clause 8
Addressing the cybersecurity requirements of Clause 8 requires a structured and systematic approach. The following steps, aligned with the principles of the IEC 61511 safety lifecycle, provide a practical roadmap.
Step 1: Assembling a Cross-Functional Team
The first step is to bring together a team with diverse expertise. This team should include:
Process Safety Engineers: To provide context on hazards and risk assessment.
Control and Instrumentation Engineers: To offer detailed knowledge of the SIS and its components.
IT/OT Cybersecurity Specialists: To lead the cybersecurity risk assessment and recommend appropriate controls.
Plant Operations Personnel: To provide insights into daily operations and potential vulnerabilities.
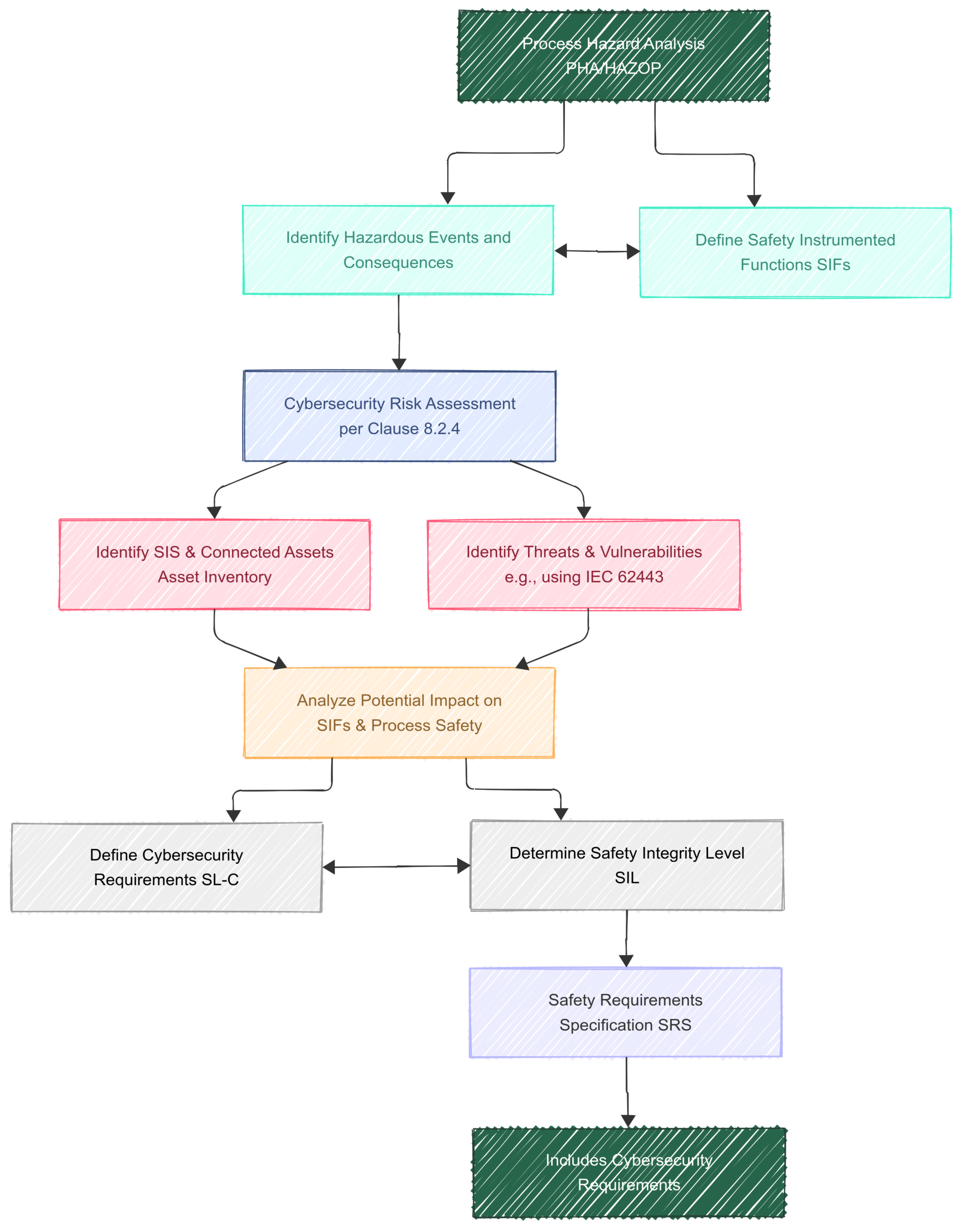
Step 2: The Integrated Risk Assessment Process
The core of Clause 8 compliance lies in a comprehensive and integrated risk assessment. This process should run in parallel with the traditional Process Hazard Analysis (PHA) and Hazard and Operability (HAZOP) studies.
Block Diagram 1: Integrated Functional Safety and Cybersecurity Risk Assessment Workflow
This integrated workflow ensures that cybersecurity is not an afterthought but a fundamental input to the safety requirements. The cybersecurity risk assessment should leverage established standards like the ISA/IEC 62443 series, which provides a comprehensive framework for securing industrial automation and control systems.
The assessment should identify potential threats (e.g., malware, unauthorized access, denial-of-service attacks) and vulnerabilities (e.g., unpatched systems, weak access controls, insecure network architecture). Crucially, it must then analyze how these could impact the functionality of each SIF.
Step 3: Defining Cybersecurity Requirements in the Safety Requirements Specification (SRS)
The outputs of the cybersecurity risk assessment must be translated into specific, actionable requirements within the Safety Requirements Specification (SRS). The SRS is the cornerstone document that details the functional and integrity requirements for each SIF.
For each SIF, the SRS should now also include:
Cybersecurity constraints: This could include network segmentation requirements, access control policies, and data encryption standards.
Resilience requirements: The ability of the SIS to withstand and recover from a cyber incident.
Security monitoring and logging requirements: To detect and respond to potential security breaches.
Secure development lifecycle requirements for SIS software: Ensuring that the software is developed with security in mind.
Step 4: Secure Design and Engineering
The cybersecurity requirements outlined in the SRS must be incorporated into the design and engineering of the SIS. This involves a “defense-in-depth” strategy, layering multiple security controls to protect the system.
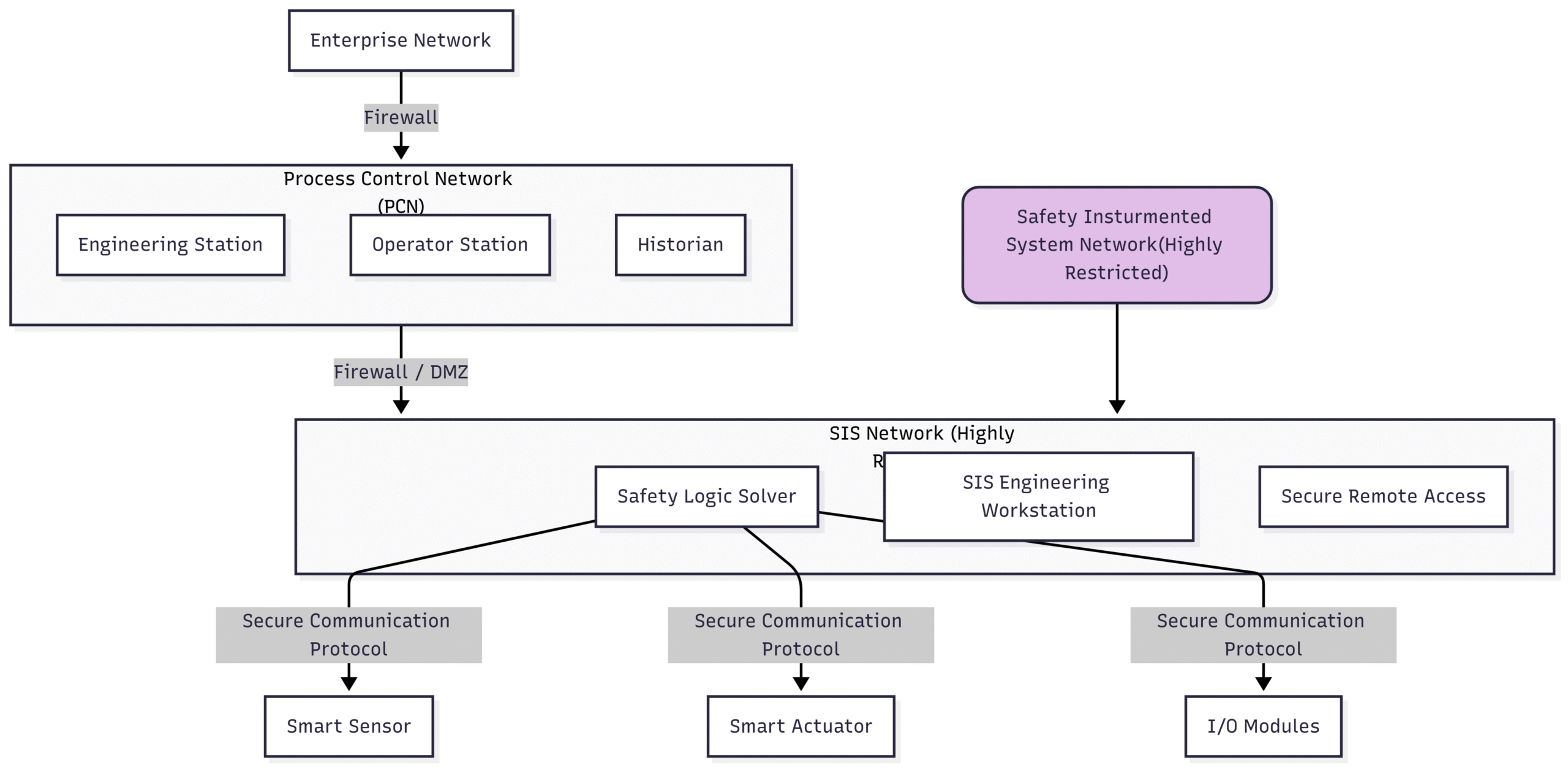
Block Diagram 2: Defense-in-Depth for a Safety Instrumented System
Key elements of a secure SIS design include:
Network Segmentation: Isolating the SIS network from the process control and enterprise networks using firewalls and demilitarized zones (DMZs).
Access Control: Implementing strict user authentication and authorization based on the principle of least privilege.
Hardening of Devices: Disabling unused ports and services, and changing default passwords on all SIS components.
Intrusion Detection and Prevention Systems (IDPS): Monitoring network traffic for suspicious activity.
Secure Remote Access: If remote access is necessary, it must be implemented through secure, authenticated, and logged channels.
Step 5: Secure Operation and Maintenance
The responsibility for cybersecurity does not end after commissioning. A robust operational and maintenance plan is essential to maintain the security posture of the SIS throughout its lifecycle. This includes:
Ongoing Monitoring: Continuously monitoring the SIS for security events and anomalies.
Patch Management: Implementing a rigorous process for testing and applying security patches in a timely manner without compromising the safety function. This requires close collaboration between IT/OT and process safety teams.
Change Management: Any changes to the SIS, including software updates or network modifications, must go through a formal management of change (MoC) process that assesses both safety and security impacts.
Incident Response Plan: Developing and regularly testing a cybersecurity incident response plan that is integrated with the overall plant emergency response procedures.
Periodic Security Assessments: Conducting regular cybersecurity risk assessments to identify new vulnerabilities and adapt to the evolving threat landscape.
Block Diagram 3: Integrated Functional Safety and Cybersecurity Lifecycle Management
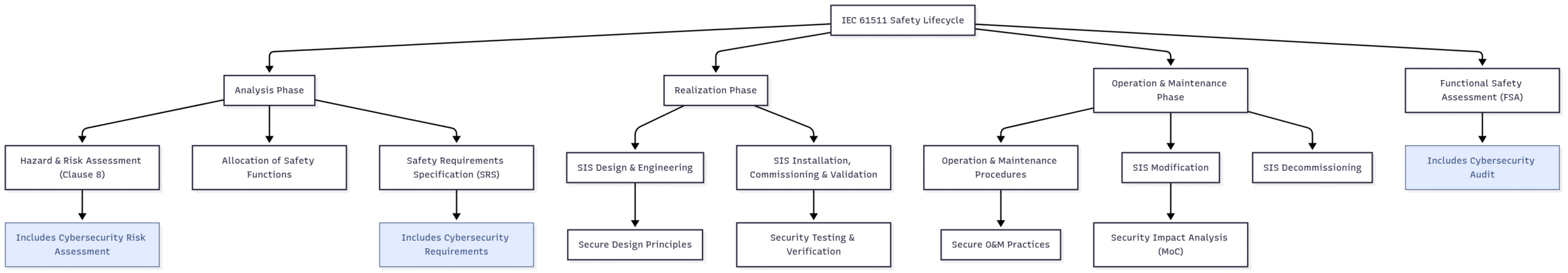
This diagram illustrates how cybersecurity considerations must be embedded throughout the entire safety lifecycle, from the initial risk assessment to decommissioning. The Functional Safety Assessment (FSA), a key verification activity in IEC 61511, must now also include a review of the effectiveness of the implemented cybersecurity measures.
The Road Ahead: A Culture of Secure Safety
The introduction of cybersecurity requirements in IEC 61511 Clause 8 marks a significant evolution in the field of process safety. It acknowledges that in our increasingly connected world, safety and security are no longer separate concerns but two sides of the same coin.
Addressing Clause 8 is not a one-time project but an ongoing commitment. It requires a cultural shift within organizations, fostering collaboration between process safety, engineering, and cybersecurity teams. It demands a proactive, risk-based approach to managing cyber threats to our most critical safety systems.
By embracing the principles outlined in Clause 8 and adopting a holistic, lifecycle-based approach to cybersecurity, the process industry can not only achieve compliance but also build more resilient, secure, and ultimately, safer operations for the future. The journey may be complex, but the destination – a world where industrial processes are safe from both accidental failures and malicious attacks – is a goal worth striving for.