IEC 62443 Explained: A Complete Guide to Industrial Cybersecurity
The digital transformation of the industrial world has ushered in an era of unprecedented efficiency and connectivity. However, this convergence of Information Technology (IT) and Operational Technology (OT) has also exposed critical infrastructure to a new and dangerous wave of cyber threats. A compromised industrial system can lead to production shutdowns, environmental damage, and even loss of life. In this high-stakes environment, a generic, IT-centric approach to cybersecurity is simply not enough. This is where the IEC 62443 series of standards comes in, offering a comprehensive and globally recognized framework for securing Industrial Automation and Control Systems (IACS). This guide will provide a deep dive into IEC 62443, explaining its core concepts, structure, and the path to achieving compliance.
What is IEC 62443? A High-Level Overview
At its core, IEC 62443 is a series of international standards that define a comprehensive framework for identifying and mitigating cybersecurity vulnerabilities in IACS. It is not a single document but a collection of standards designed to be used by all stakeholders involved in the lifecycle of an industrial system.
The standard’s journey began as ISA-99, developed by the International Society of Automation (ISA). Recognizing the critical need for a global standard, the International Electrotechnical Commission (IEC) adopted and further developed these principles, resulting in the IEC 62443 series we know today.
The fundamental philosophy of IEC 62443 is a risk-based approach. It moves away from a one-size-fits-all checklist and instead focuses on a continuous process of identifying, assessing, and mitigating risks based on the specific operational environment. This ensures that security measures are appropriate, effective, and sustainable.
The standard acknowledges that industrial cybersecurity is a shared responsibility and defines three key roles:
Asset Owners: The organizations that own and operate the IACS (e.g., a factory or power plant).
System Integrators: The companies responsible for designing, building, and commissioning the IACS.
Product Suppliers: The vendors who develop the hardware and software components that make up the IACS.
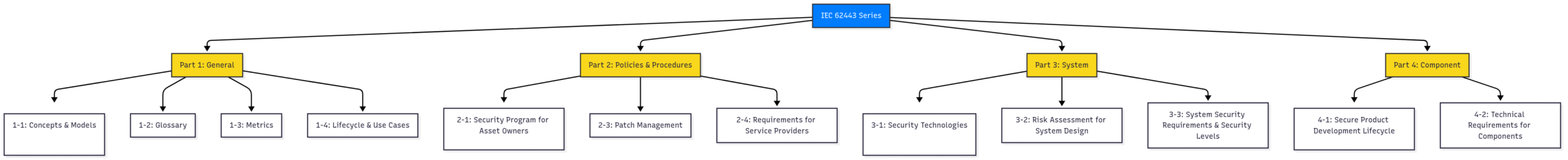
To address the needs of these different stakeholders, the IEC 62443 standard is organized into four main categories:
General: Foundational information, concepts, and models.
Policies & Procedures: Requirements for the security management program.
System: Guidelines for the secure design and implementation of IACS.
Component: Requirements for the secure development of IACS products.
Block Diagram 1: The Structure of IEC 62443
Core Concepts of IEC 62443
To effectively implement IEC 62443, it is essential to understand its fundamental concepts. These building blocks provide the methodology for creating a robust and resilient industrial cybersecurity posture.
Defense in Depth
Borrowed from military strategy, Defense in Depth is the principle of establishing multiple layers of protection. The idea is that if one security control fails, another is in place to thwart an attack. In the context of IEC 62443, this means implementing a combination of physical, technical, and administrative controls across the entire IACS environment. This multi-layered approach ensures there is no single point of failure.
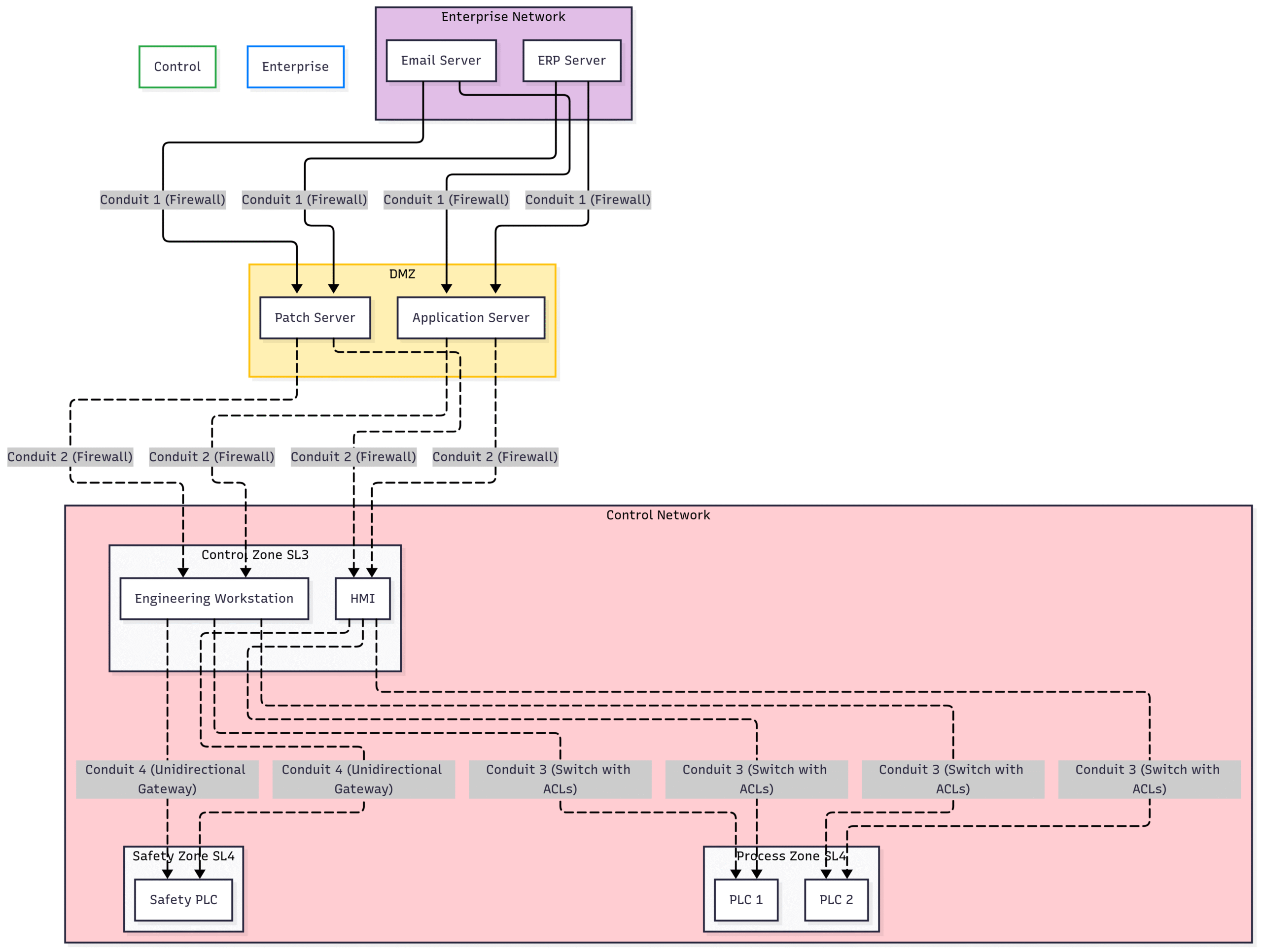
Zones and Conduits: The Foundation of Network Segmentation
One of the most powerful concepts in IEC 62443 is the segmentation of the IACS into Zones and Conduits. This “divide and conquer” strategy is critical for isolating critical processes and controlling the flow of data.
Zones are logical or physical groupings of assets that share common security requirements. For example, a set of controllers responsible for a critical manufacturing process could be grouped into a high-security zone. By creating these zones, you can apply specific security policies and controls tailored to the risk level of the assets within that zone.
Conduits are the communication channels that connect zones. The key principle here is that all communication between zones must pass through a defined conduit. This allows for the monitoring and enforcement of security policies on the data flowing between different parts of the system. For instance, a firewall acting as a conduit between the corporate network and the control network can restrict traffic to only what is explicitly permitted.
Block Diagram 2: Illustrating Zones and Conduits in an IACS Architecture
Security Levels (SLs): Measuring the Required Level of Protection
IEC 62443 introduces the concept of Security Levels (SLs) to define the required robustness of a system or component against a potential attack. There are five SLs:
SL 0: No specific security requirements.
SL 1: Protection against casual or coincidental violations.
SL 2: Protection against intentional violation by simple means with low resources, generic skills, and low motivation.
SL 3: Protection against intentional violation by sophisticated means with moderate resources, IACS-specific skills, and moderate motivation.
SL 4: Protection against intentional violation by sophisticated means with extended resources, IACS-specific skills, and high motivation.
The determination of the required SL for a particular zone is a result of a thorough risk assessment. It’s also important to distinguish between three types of SLs:
Target SL (SL-T): The desired level of security for a system, as determined by the risk assessment.
Achieved SL (SL-A): The actual level of security that the system provides. The goal is for the SL-A to meet or exceed the SL-T.
Capability SL (SL-C): The inherent security capabilities of a component or system.
Foundational Requirements (FRs): The Seven Pillars of Security
To achieve the different Security Levels, IEC 62443 defines seven Foundational Requirements (FRs). These FRs represent the fundamental security functions that must be implemented.
Identification and Authentication Control (IAC): Ensuring that all users and devices are uniquely identifiable and authenticated before being granted access.
Use Control (UC): Enforcing the privileges of authenticated users and devices, ensuring they can only perform their authorized functions.
System Integrity (SI): Protecting the integrity of the IACS to prevent unauthorized modification.
Data Confidentiality (DC): Ensuring that information is not disclosed to unauthorized individuals, entities, or processes.
Restricted Data Flow (RDF): Controlling and segmenting the flow of data between zones and conduits.
Timely Response to Events (TRE): Responding to and reporting on security violations in a timely manner.
Resource Availability (RA): Ensuring that the IACS is resilient against events that could cause a denial of service.
A Deeper Dive into the IEC 62443 Series
As mentioned earlier, the standard is divided into four main parts, each catering to a different aspect of industrial cybersecurity.
Part 1: General
This part lays the groundwork for the entire series. It defines the terminology, concepts, and models that are used throughout the other documents. It is the ideal starting point for anyone new to IEC 62443.
Part 2: Policies and Procedures
This section focuses on the human and organizational aspects of cybersecurity. It emphasizes that technology alone is not enough.
IEC 62443-2-1 provides the requirements for establishing and maintaining a Cybersecurity Management System (CSMS) for the asset owner.
IEC 62443-2-4 outlines the security program requirements for IACS service providers, including system integrators and maintenance teams.
Part 3: System Security
This part delves into the technical requirements for the secure design and implementation of an IACS.
IEC 62443-3-2 guides asset owners and system integrators on how to conduct a security risk assessment and define the target security levels for different zones.
IEC 62443-3-3 specifies the detailed system security requirements and maps them to the seven Foundational Requirements and four Security Levels.
Part 4: Component Security
This section is primarily aimed at product suppliers and defines the requirements for developing secure IACS components.
IEC 62443-4-1 details the requirements for a secure product development lifecycle, ensuring that security is considered at every stage, from design and coding to testing and deployment.
IEC 62443-4-2 provides the specific technical security requirements for IACS components, such as embedded devices, network equipment, and software applications.
Block Diagram 3: The IEC 62443 Certification Ecosystem

The Path to IEC 62443 Certification
Achieving certification against one or more parts of the IEC 62443 standard is a powerful way to demonstrate a commitment to industrial cybersecurity. It provides customers, partners, and regulators with confidence that a robust security program is in place.
The certification process typically involves the following steps:
Gap Analysis and Risk Assessment: The first step is to conduct a thorough assessment of the current security posture against the requirements of the relevant IEC 62443 standard. This will identify gaps and inform the risk assessment.
Implementation of Security Controls: Based on the findings of the gap analysis, the necessary technical, physical, and administrative controls are implemented to meet the target security level.
Auditing by a Recognized Certification Body: An accredited third-party auditor will conduct a detailed audit of the processes, documentation, and technical implementations to verify compliance with the standard.
Maintaining Compliance: Certification is not a one-time event. It requires a continuous commitment to maintaining and improving the security program, which is typically verified through annual surveillance audits.
There are different types of certification available, catering to the different roles in the IACS ecosystem:
Product Certification (IEC 62443-4-1 and 4-2): For product suppliers, demonstrating that their components are developed according to a secure lifecycle and meet specific technical security requirements.
System Certification (IEC 62443-3-3): For system integrators and asset owners, proving that an integrated IACS meets the required security level.
Process/CSMS Certification (IEC 62443-2-1 and 2-4): For asset owners and service providers, showing that they have mature and effective cybersecurity management processes.
Benefits of Adopting IEC 62443
Embracing the IEC 62443 framework offers a multitude of benefits that extend beyond simply preventing cyberattacks.
Enhanced Security and Resilience: A systematic, risk-based approach to security significantly reduces the likelihood and impact of a cyber incident.
Improved Operational Reliability: By securing the IACS, organizations can prevent costly production downtime and ensure the continuous and safe operation of their facilities.
Standardized Approach: IEC 62443 provides a common language and set of expectations for asset owners, integrators, and suppliers, streamlining procurement and integration processes.
Regulatory Compliance: Adherence to IEC 62443 can help organizations meet the requirements of various regional and industry-specific regulations, such as the NIS2 Directive in the European Union.
Competitive Advantage: In an increasingly security-conscious market, IEC 62443 certification can be a key differentiator, demonstrating a commitment to quality and security.
Conclusion
The IEC 62443 standard is no longer a niche topic for a handful of security experts; it is a critical business imperative for any organization that relies on Industrial Automation and Control Systems. By providing a flexible, risk-based, and comprehensive framework, it empowers organizations to build a resilient defense against the evolving landscape of cyber threats. The journey to IEC 62443 compliance may seem daunting, but the rewards in terms of security, reliability, and peace of mind are immeasurable. It is time for every industrial stakeholder to embrace this standard and secure the future of our critical infrastructure.
