Top 10 Cybersecurity Risks for Industrial Automation Systems
The convergence of information technology (IT) and operational technology (OT) has revolutionized industrial automation, unlocking unprecedented levels of efficiency and productivity. However, this digital transformation has also exposed critical infrastructure to a new and evolving landscape of cyber threats. Industrial Automation Systems (IAS), which control everything from manufacturing assembly lines to power grids and water treatment facilities, have become prime targets for malicious actors seeking to cause disruption, steal intellectual property, or even endanger public safety. This blog post delves into the top 10 cybersecurity risks facing industrial automation systems today, complete with block diagrams to illustrate these complex threats.
1. Malware and Ransomware Infections
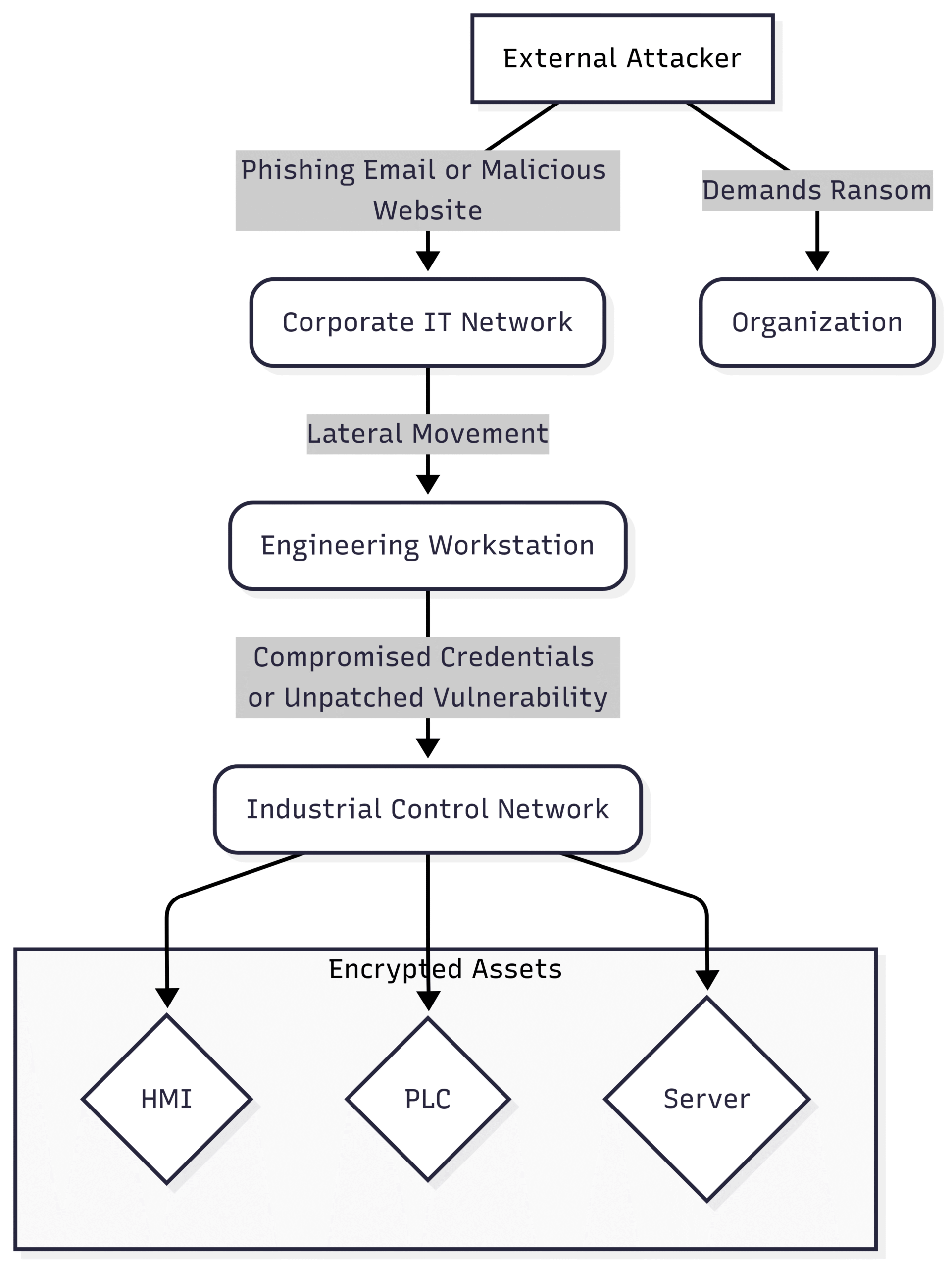
Malware, and its particularly nefarious variant, ransomware, represents one of the most significant threats to industrial automation. Unlike in the IT world where data loss is the primary concern, a malware outbreak in an OT environment can have devastating physical consequences. Ransomware can encrypt critical files on Human-Machine Interfaces (HMIs) or engineering workstations, rendering operators unable to monitor or control industrial processes. More sophisticated malware can directly target controllers, altering their logic and causing equipment to malfunction, leading to production downtime, damaged machinery, and potentially hazardous conditions.
Block Diagram: Ransomware Attack on an Industrial Network
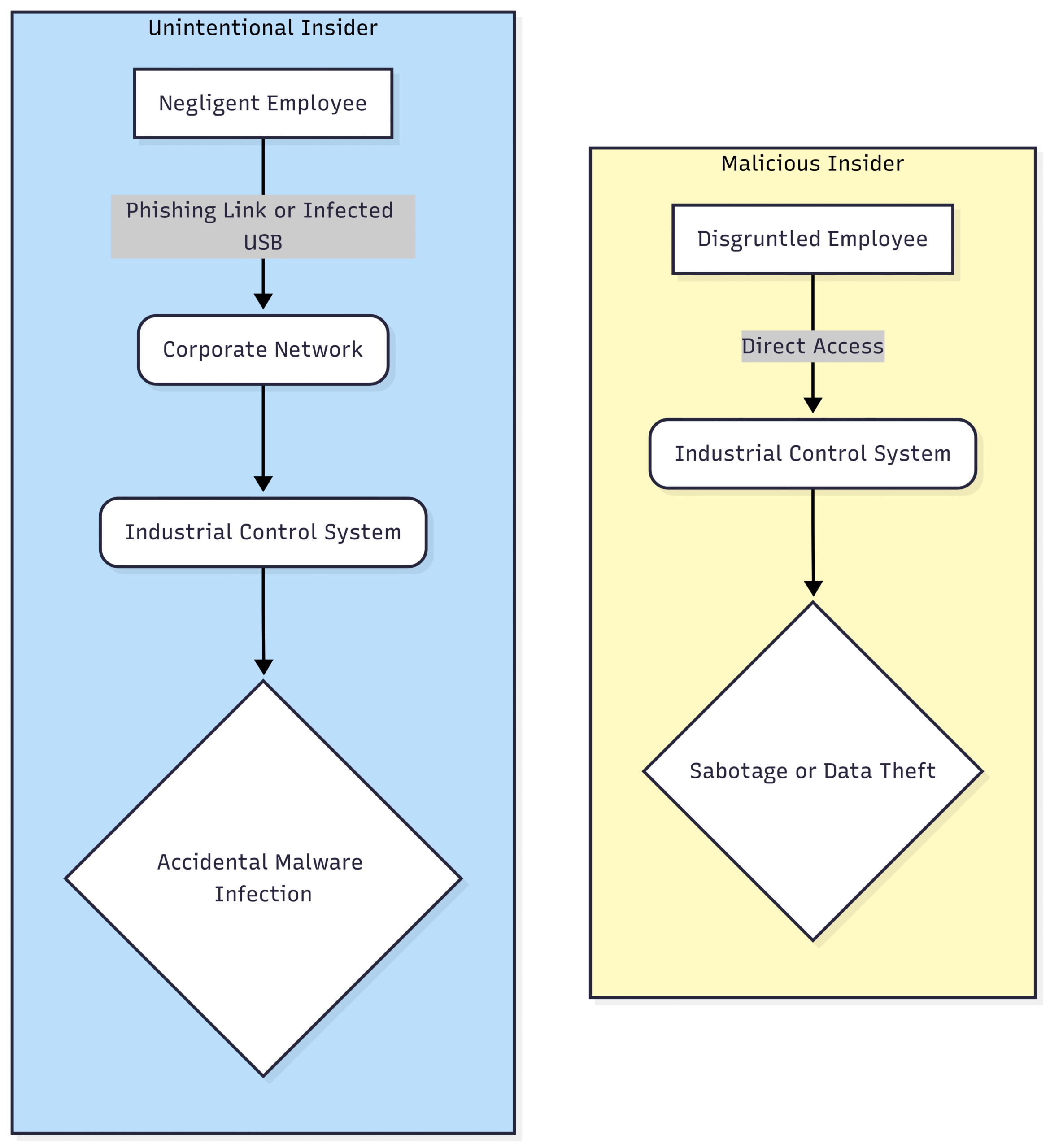
2. Insider Threats: The Danger Within
Insider threats are a particularly insidious risk as they originate from individuals with authorized access to industrial systems. These threats can be either malicious or unintentional. A disgruntled employee might intentionally sabotage a system, while a negligent worker could inadvertently introduce malware through a contaminated USB drive or fall victim to a social engineering scheme. The consequences can range from the theft of sensitive operational data to the deliberate manipulation of control processes, leading to catastrophic failures.
Block Diagram: Malicious and Unintentional Insider Threats
3. Supply Chain Attacks: A Compromised Foundation
Modern industrial automation systems are complex ecosystems of hardware and software from numerous vendors. This intricate supply chain presents a broad attack surface. A threat actor can compromise a less secure vendor, embedding malicious code into software updates or hardware components. When these seemingly legitimate products are integrated into an industrial facility, the malware can activate, providing the attacker with a backdoor into the network. These attacks are notoriously difficult to detect as they exploit the trust between an organization and its suppliers.
Block Diagram: Supply Chain Attack Vector

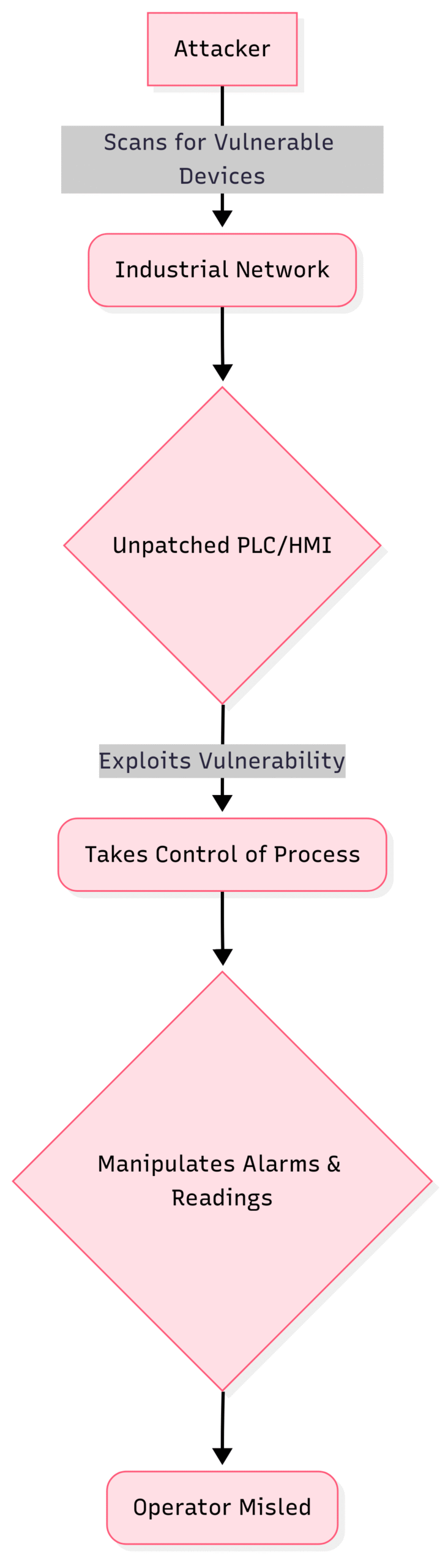
4. Vulnerabilities in PLCs and HMIs
Programmable Logic Controllers (PLCs) and Human-Machine Interfaces (HMIs) are the foundational components of any industrial automation system. Unfortunately, many of these devices were designed with a focus on reliability and performance, not security. They often lack modern security features like strong encryption and robust authentication mechanisms. Vulnerabilities in PLCs and HMIs can be exploited to gain unauthorized control over industrial processes, manipulate alarms, or display false information to operators, leading to incorrect decisions and potentially dangerous outcomes.
Block Diagram: Exploitation of PLC/HMI Vulnerabilities
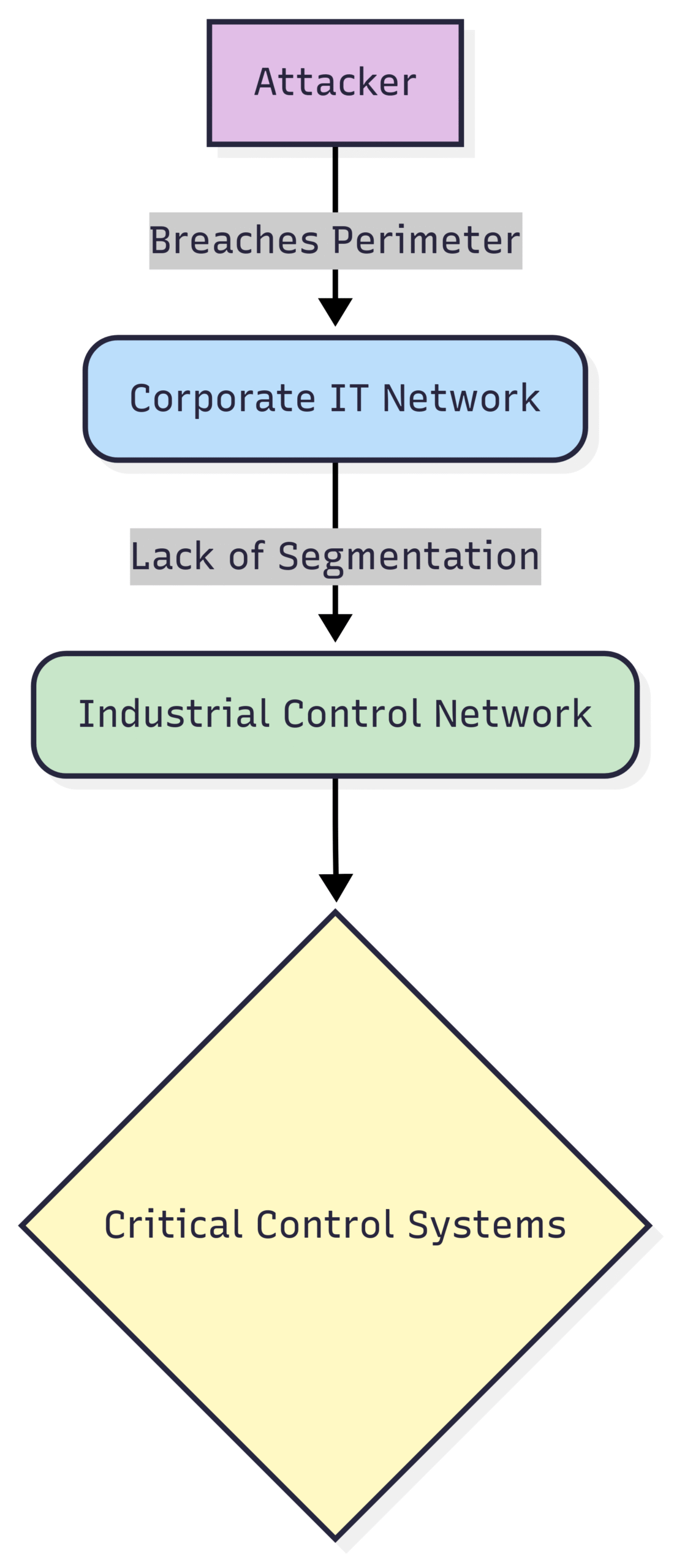
5. Weak Network Security and Segmentation
In the past, industrial control networks were often physically isolated from corporate IT networks (a concept known as the “air gap”). However, the need for data exchange and remote access has largely eroded this separation. Poor network segmentation allows attackers who have breached the corporate network to move laterally into the OT environment. A lack of robust firewalls, intrusion detection systems, and access controls on the industrial network creates a direct path for threat actors to reach critical control systems.
Block Diagram: Poor Network Segmentation
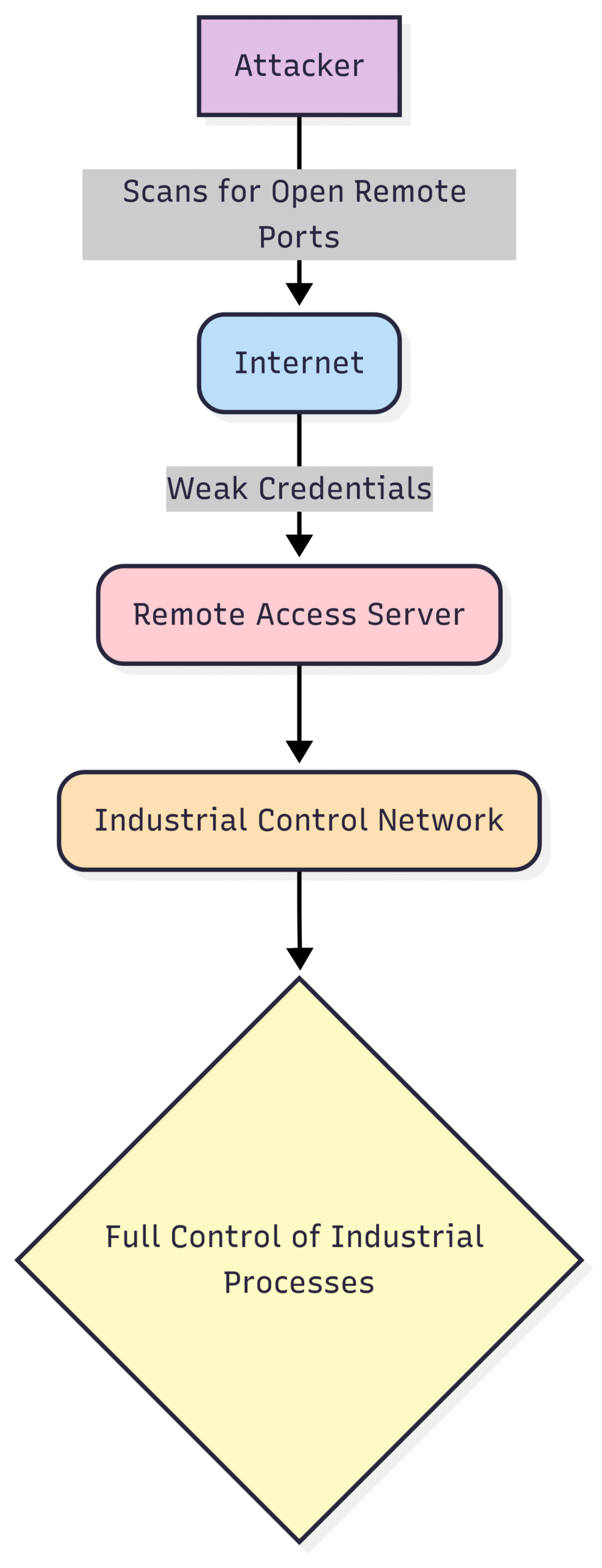
6. Insecure Remote Access
The ability to remotely access industrial systems for maintenance and monitoring is a significant operational advantage. However, if not implemented securely, it becomes a major vulnerability. Weak or default passwords, single-factor authentication, and unencrypted remote connections provide an easy entry point for attackers. Once they gain remote access, they can have the same level of control as an operator on-site, with the potential to disrupt operations from anywhere in the world.
Block Diagram: Insecure Remote Access Exploit
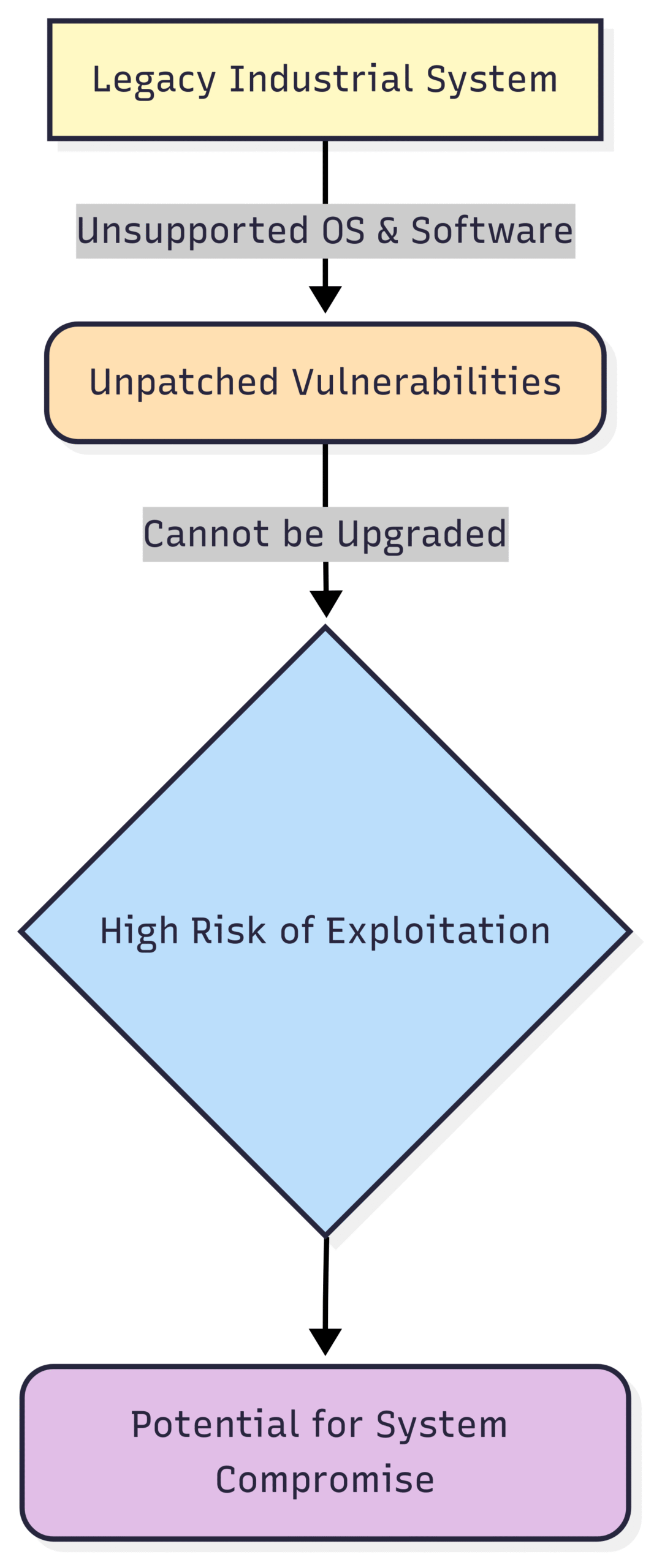
7. The Challenge of Legacy Systems
Industrial automation systems are built to last, with many components having operational lifespans of 20 years or more. This means that many facilities rely on legacy systems that are no longer supported by their original manufacturers. These aging systems may not be patchable for known vulnerabilities and may run on outdated operating systems. Replacing them can be prohibitively expensive, leaving them as ticking time bombs in the network, vulnerable to a wide range of exploits.
Block Diagram: Risk of Legacy Systems
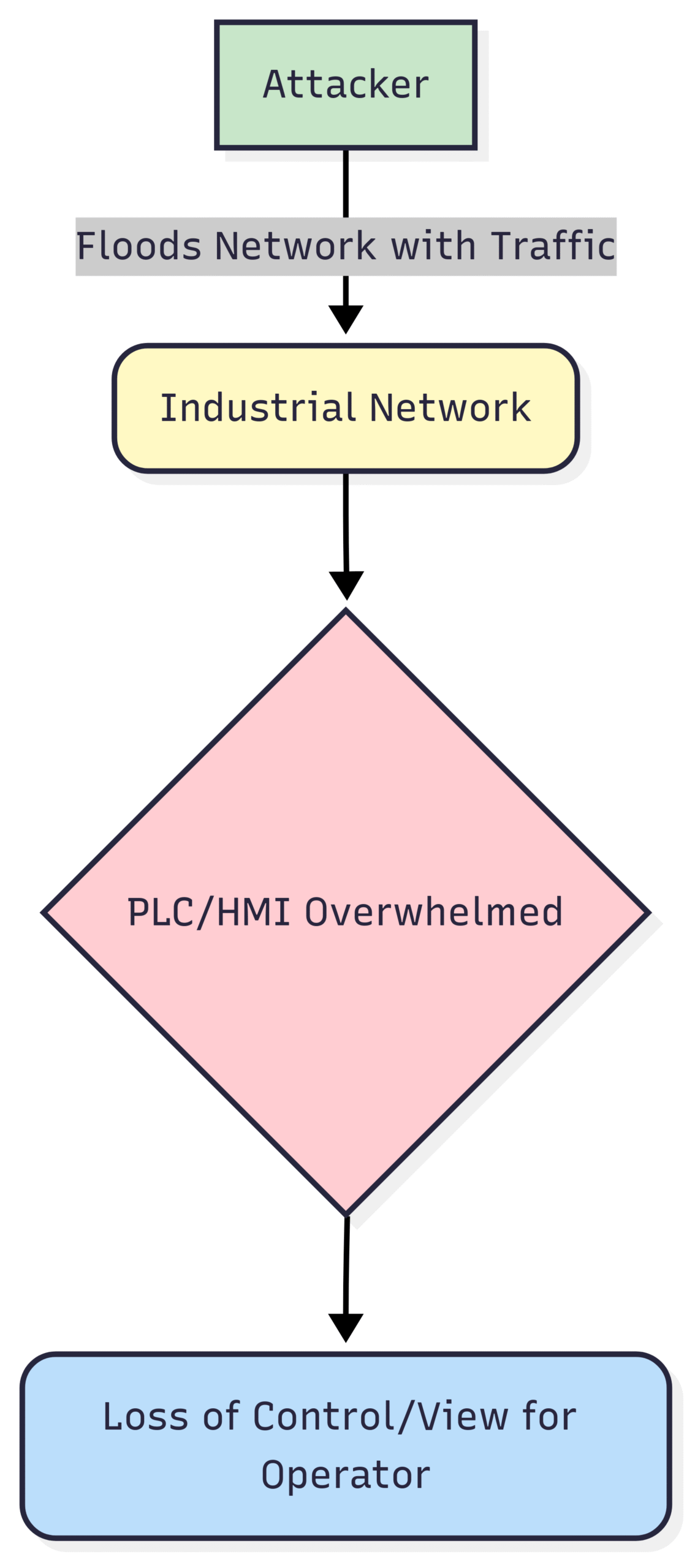
8. Denial-of-Service (DoS) Attacks
Denial-of-Service (DoS) attacks aim to make a machine or network resource unavailable to its intended users. In an industrial context, a DoS attack could flood a PLC or an HMI with so much network traffic that it becomes unresponsive. This could lead to a loss of view or control for operators, forcing a manual shutdown of processes and resulting in significant production losses. Even a temporary disruption can have cascading effects throughout a tightly integrated manufacturing process.
Block Diagram: Denial-of-Service Attack on a Control System
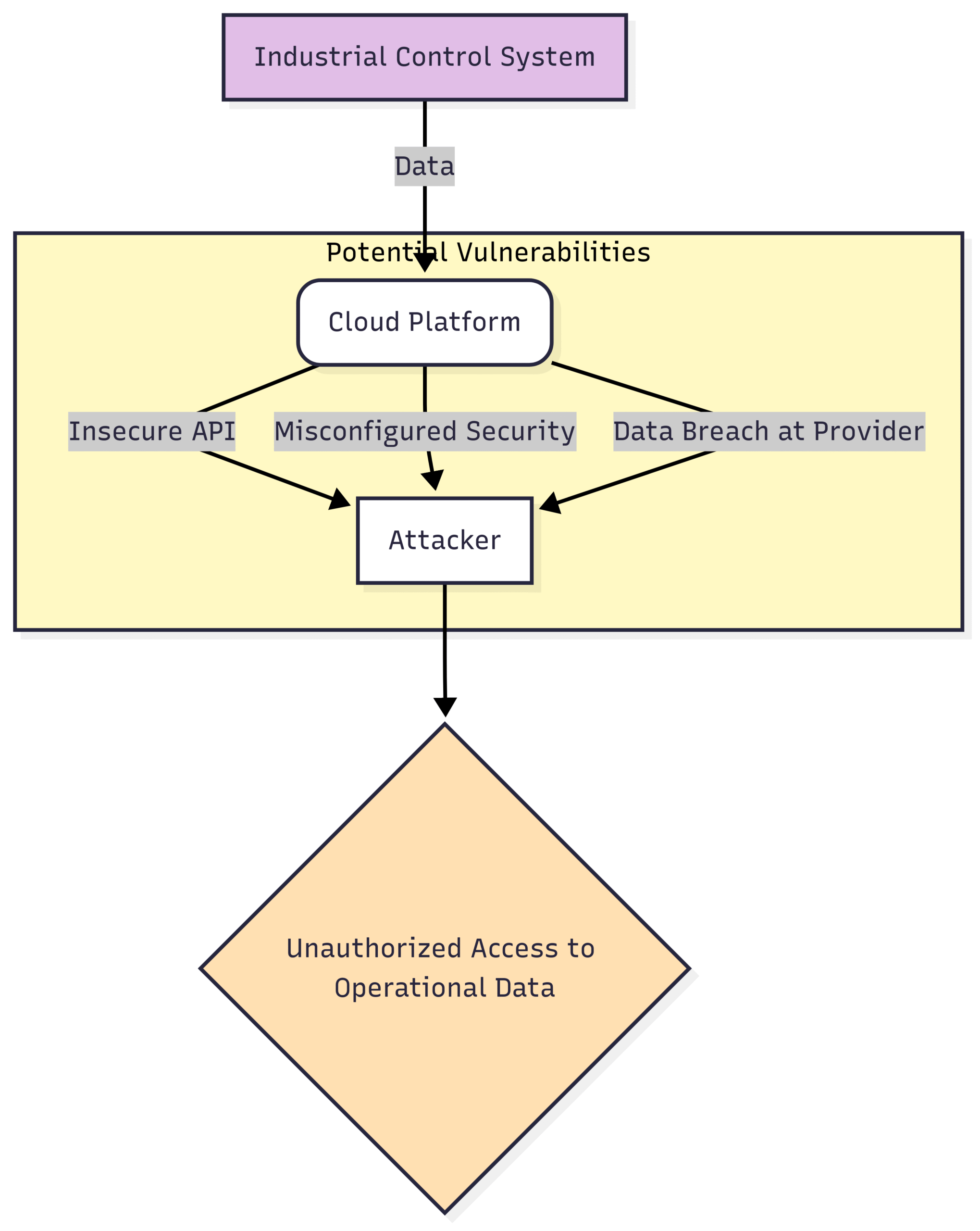
9. Cloud Integration Risks
The adoption of cloud computing in industrial environments for data storage, analytics, and remote management offers numerous benefits. However, it also introduces new security risks. Misconfigured cloud security settings, insecure APIs, and data breaches at the cloud service provider can expose sensitive operational data and potentially provide a pathway for attackers to access the industrial network. Securely managing the flow of data between on-premise OT systems and the cloud is a critical challenge.
Block Diagram: Cloud Integration Security Risks
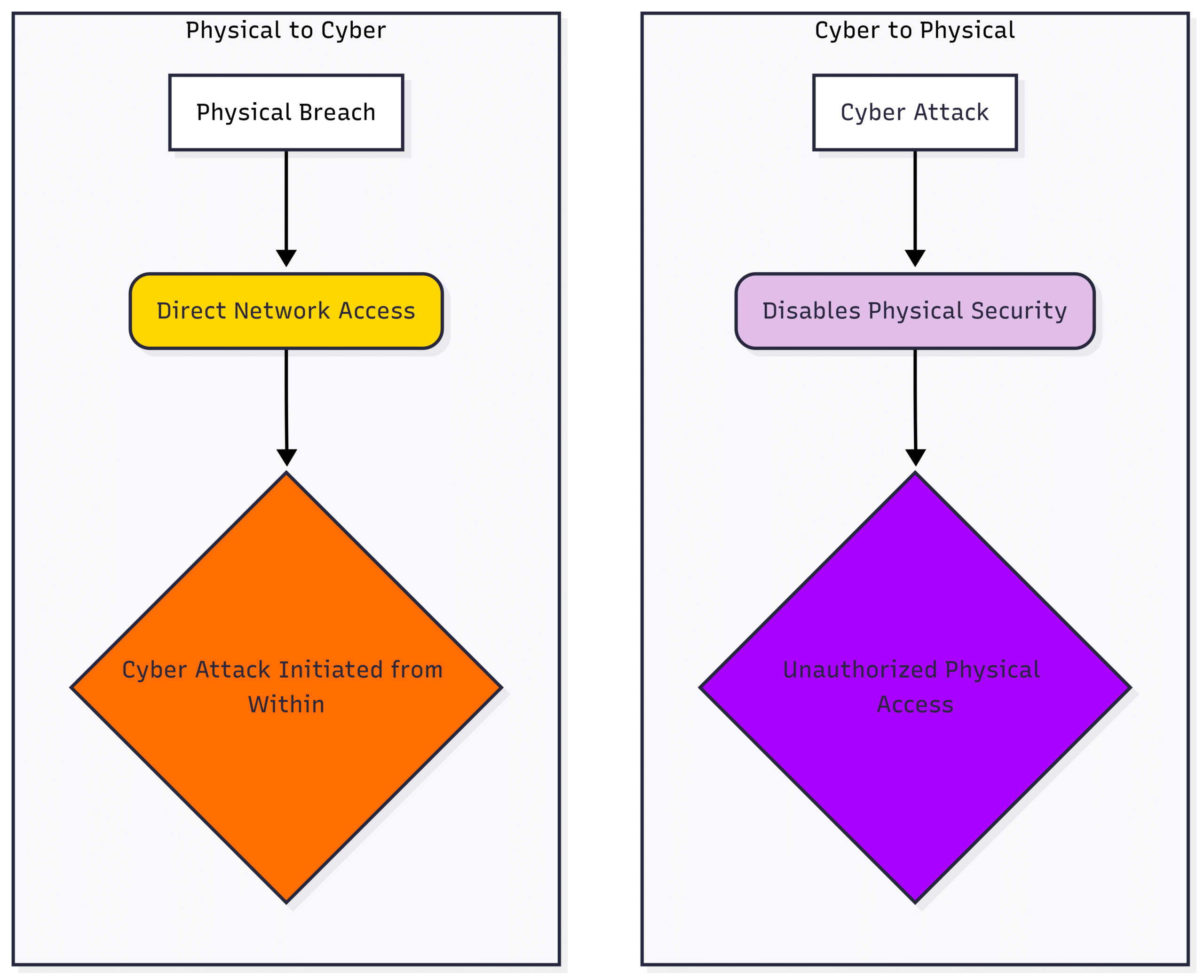
10. Convergence of Physical and Cybersecurity Threats
The lines between physical security and cybersecurity are blurring. A physical breach of a facility can lead to a cyber-attack, and a cyber-attack can have physical consequences. For example, an attacker could use a cyber-attack to disable security cameras and access control systems to gain physical entry to a sensitive area. Conversely, an unauthorized individual with physical access could plug a malicious device directly into the industrial network. A holistic security strategy must address both the physical and digital domains.
Block Diagram: Physical and Cybersecurity Convergence
In conclusion, securing industrial automation systems requires a multi-layered, defense-in-depth approach that addresses people, processes, and technology. By understanding these top 10 risks, organizations can take proactive steps to mitigate vulnerabilities, enhance their security posture, and ensure the safe and reliable operation of their critical infrastructure in an increasingly connected world.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.