IEC 62443 Compliance Checklist for Instrumentation Engineers: A Practical Guide
The convergence of operational technology (OT) and information technology (IT) has brought unprecedented efficiency and connectivity to industrial processes. However, this interconnectivity has also opened the door to a new wave of cybersecurity threats that can have devastating consequences for safety, availability, and integrity. For instrumentation engineers, who work at the very heart of industrial automation and control systems (IACS), understanding and implementing robust cybersecurity measures is no longer a niche skill but a fundamental responsibility. The IEC 62443 series of standards provides a comprehensive framework for securing IACS, and this blog post offers a detailed compliance checklist specifically tailored for instrumentation professionals.
This guide will break down the essential aspects of IEC 62443, translating the standard’s foundational requirements into practical, actionable steps for instrumentation engineers. We will also utilize block diagrams to illustrate how these security concepts apply to typical instrumentation and control architectures.
Understanding the Landscape: What is IEC 62443?
IEC 62443 is an international series of standards that provides a flexible and comprehensive framework for addressing and mitigating security vulnerabilities in IACS environments. It’s not a one-size-fits-all solution but rather a risk-based approach to cybersecurity. The standard is divided into four main categories:
General: Introduces the fundamental concepts, terminology, and models.
Policies and Procedures: Focuses on the human element, outlining requirements for security programs, patch management, and the roles of various stakeholders.
System: Provides technical requirements for the security of IACS at the system level, including the crucial concepts of zones and conduits.
Component: Specifies the security requirements for the individual components that make up the IACS, such as PLCs, sensors, and actuators.
For instrumentation engineers, the “System” and “Component” parts are particularly relevant, as they directly influence the selection, implementation, and maintenance of instrumentation and control devices.
A core concept within IEC 62443 is the Security Level (SL). There are five SLs, ranging from SL 0 (no specific security requirements) to SL 4 (protection against intentional violation using sophisticated means with extensive resources). The required SL for a particular system or component is determined by a thorough risk assessment.
Another key principle is the use of zones and conduits. A zone is a logical grouping of assets that share common security requirements. A conduit is the communication channel between zones. By segmenting the IACS into zones and controlling the data flow through conduits, the impact of a security breach can be contained.
The Instrumentation Engineer’s Role in IEC 62443 Compliance
Instrumentation engineers play a pivotal role in implementing IEC 62443. Their expertise in measurement and control devices, communication protocols, and system integration is essential for translating the standard’s requirements into tangible security controls. From the initial design and specification to commissioning and ongoing maintenance, instrumentation engineers are on the front lines of IACS cybersecurity.
The following checklist is structured around the seven Foundational Requirements (FRs) of IEC 62443, providing specific actions and considerations for instrumentation engineers.
Foundational Requirement 1: Access Control (AC)
Access Control is about ensuring that only authorized individuals, devices, and software can access the IACS. For instrumentation engineers, this extends from the control room down to the individual field device.
Checklist for Access Control:
Physical Access:
Are field instrument enclosures, junction boxes, and marshalling cabinets kept locked and secure?
Is there a formal procedure for accessing these enclosures, including a log of who accessed them and when?
Are unused ports on switches and other network devices in the field physically disabled?
Logical Access:
Are default passwords on all smart instruments, PLCs, and other configurable devices changed upon installation?
Is unique user authentication required for accessing device configuration menus?
Are different user roles defined with varying levels of access (e.g., read-only for operators, full access for maintenance engineers)?
Is multi-factor authentication considered for critical devices or remote access?
Remote Access:
Is remote access to instrumentation and control systems strictly controlled and monitored?
Are secure communication protocols (e.g., VPNs with strong encryption) used for all remote connections?
Is there a clear policy defining who is authorized for remote access and under what circumstances?
Foundational Requirement 2: Use Control (UC)
Use Control goes a step further than Access Control by restricting the actions that authorized users can perform.
Checklist for Use Control:
Privilege Management:
Are user accounts configured with the principle of least privilege, meaning they only have the permissions necessary to perform their job function?
Are administrative privileges for configuring instruments and control logic strictly limited to authorized personnel?
Is there a formal process for granting and revoking user privileges?
Session Control:
Do device configuration sessions automatically time out after a period of inactivity?
Are users required to log out of configuration tools when they are finished?
Foundational Requirement 3: System Integrity (SI)
System Integrity focuses on protecting the IACS from unauthorized modification or corruption. For instrumentation engineers, this means ensuring the reliability and trustworthiness of the data coming from and going to field devices.
Checklist for System Integrity:
Firmware and Software Integrity:
Is there a formal process for validating the source and integrity of firmware updates for smart instruments and PLCs before they are installed?
Are cryptographic hashes or digital signatures used to verify the authenticity of firmware files?
Is there an inventory of all firmware versions currently deployed in the field?
Configuration Integrity:
Are regular backups of device configurations performed and stored securely?
Are there mechanisms in place to detect unauthorized changes to instrument configurations?
Is a change management process followed for all modifications to control logic and instrument parameters?
Data Integrity:
For critical measurements, are diagnostic features on smart instruments (e.g., NAMUR NE 107 diagnostics) monitored to detect potential sensor or device failures?
Are communication protocols that include error checking and data validation used (e.g., HART, Foundation Fieldbus)?
Block Diagram: System Integrity in an Instrumentation Loop

A simplified block diagram illustrating where system integrity controls are applied in a typical instrumentation loop. Firmware and configuration integrity are crucial at both the transmitter and PLC levels.
Foundational Requirement 4: Data Confidentiality (DC)
Data Confidentiality aims to prevent the unauthorized disclosure of information. While availability and integrity are often the primary concerns in OT, confidentiality is becoming increasingly important, especially with the rise of industrial espionage.
Checklist for Data Confidentiality:
Data in Transit:
For wireless instrumentation (e.g., WirelessHART), is encryption enabled to protect the confidentiality of the transmitted data?
When data is transmitted over public networks (e.g., for remote monitoring), is it encrypted using strong, industry-standard protocols?
Data at Rest:
Are sensitive configuration files and historical data stored in an encrypted format?
Is access to databases containing process data restricted to authorized personnel?
Foundational Requirement 5: Restricted Data Flow (RDF)
Restricted Data Flow is about controlling the communication paths within the IACS. This is where the concept of zones and conduits is implemented.
Checklist for Restricted Data Flow:
Network Segmentation:
Is the control network segmented from the business network using a firewall?
Are critical control loops isolated on their own dedicated network segments?
Are wireless instrumentation networks physically and logically separated from wired networks?
Conduit Control:
Are firewalls or other security appliances used to control the flow of data between zones?
Are firewall rules configured to only allow necessary communication between zones (i.e., “deny by default”)?
Is unidirectional communication (using data diodes) considered for sending data from the OT network to the IT network without allowing any return path?
Block Diagram: Zones and Conduits in an IACS Architecture
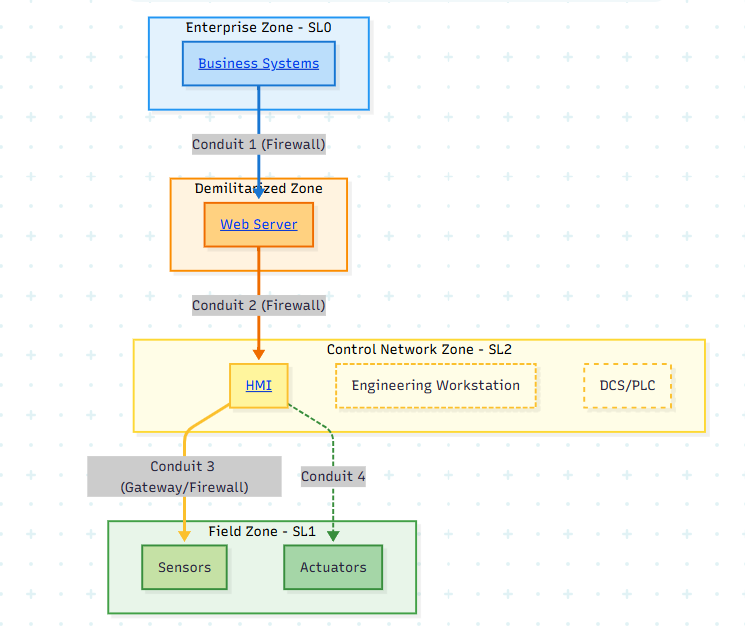
This block diagram shows a simplified IACS architecture segmented into zones with controlled communication through conduits. As an instrumentation engineer, understanding how your devices fit into these zones is critical.
Foundational Requirement 6: Timely Response to Events (TRE)
Timely Response to Events is about detecting and responding to security incidents in a timely manner to minimize their impact.
Checklist for Timely Response to Events:
Event Logging and Monitoring:
Are security-related events (e.g., failed login attempts, configuration changes) on smart instruments and PLCs logged?
Are these logs centrally collected and monitored for suspicious activity?
Are alerts generated for critical security events?
Incident Response Plan:
Is there a documented incident response plan that outlines the steps to be taken in the event of a cybersecurity incident?
Does the plan include contact information for key personnel, including instrumentation engineers?
Are incident response drills conducted regularly?
Foundational Requirement 7: Resource Availability (RA)
Resource Availability ensures that the IACS is resilient to attacks that could deny access to critical resources. For instrumentation engineers, this means ensuring that control loops remain operational and that safety systems are not compromised.
Checklist for Resource Availability:
Redundancy:
For critical control loops, are redundant instruments and controllers in place?
Is redundant networking (e.g., using parallel redundancy protocol – PRP) used for critical communication paths?
Denial of Service Protection:
Are measures in place to protect against denial-of-service attacks that could flood the network and overwhelm PLCs or other devices?
Are network devices configured to filter out malicious traffic?
Backup and Recovery:
Are regular backups of all critical systems and configurations performed?
Is there a tested disaster recovery plan in place to restore operations in the event of a major incident?
The Journey to Compliance: A Continuous Process
Achieving compliance with IEC 62443 is not a one-time project but an ongoing journey. It requires a cultural shift towards a security-first mindset. For instrumentation engineers, this means integrating cybersecurity considerations into every aspect of their work, from the initial design to the daily maintenance of the systems that keep our industries running safely and efficiently. By using this checklist as a guide, instrumentation professionals can take a leading role in securing our critical infrastructure for the future.
