IEC 62443 Framework for SCADA and DCS Systems
The digital transformation of industrial environments has ushered in an unprecedented era of efficiency and connectivity. However, this evolution has also exposed the very heart of modern industry – Supervisory Control and Data Acquisition (SCADA) and Distributed Control Systems (DCS) – to a new and ever-growing wave of cyber threats. In this in-depth blog, we will explore how the IEC 62443 framework provides a robust and comprehensive methodology for securing these critical systems, ensuring the safety, integrity, and availability of industrial operations.
For decades, SCADA and DCS environments were largely isolated, proprietary systems, their security concerns limited to physical access control. Today, the convergence of Information Technology (IT) and Operational Technology (OT) has created a complex, interconnected landscape. While this integration unlocks immense potential for data analysis and remote management, it also creates new attack vectors for malicious actors seeking to disrupt critical infrastructure, steal intellectual property, or even cause physical harm.
In this new paradigm, a piecemeal or purely IT-focused approach to cybersecurity is insufficient. The unique demands of industrial automation and control systems (IACS) – where uptime and deterministic performance are paramount – require a specialized, defense-in-depth strategy. This is where the International Electrotechnical Commission (IEC) 62443 series of standards comes into play.
What is the IEC 62443 Framework? A Blueprint for Industrial Cybersecurity
The IEC 62443 is not just another cybersecurity standard; it is a comprehensive framework specifically designed to address the unique security challenges of IACS. Developed by a global team of experts, it provides a structured and risk-based approach to cybersecurity that is applicable across a wide range of industries, from manufacturing and energy to water treatment and transportation.
A key philosophical underpinning of IEC 62443 is the concept of shared responsibility. Cybersecurity is not solely the responsibility of the asset owner; it is a collaborative effort that extends to system integrators, product suppliers, and service providers. Each stakeholder has a role to play in ensuring the overall security of the industrial environment.
The standard is divided into four main categories, each addressing a different aspect of IACS security:
General (62443-1): This section lays the groundwork, defining terminology, concepts, and models that are used throughout the series.
Policies and Procedures (62443-2): This part focuses on the human element and organizational aspects of cybersecurity, including the requirements for a robust Cybersecurity Management System (CSMS).
System (62443-3): This category delves into the technical requirements for secure IACS design and implementation, including the crucial concepts of zones and conduits.
Component (62443-4): This section provides guidance for product suppliers on how to develop secure IACS components and systems.
By addressing people, processes, and technology, the IEC 62443 framework provides a holistic and lifecycle-based approach to industrial cybersecurity.
The Seven Foundational Requirements: The Pillars of IEC 62443
At the core of the IEC 62443 framework are seven Foundational Requirements (FRs). These FRs represent the fundamental security principles that must be addressed to achieve a robust cybersecurity posture. Let’s explore each of these in detail:

FR 1: Identification and Authentication Control (IAC): This requirement is all about ensuring that only authorized individuals and systems can access the IACS. This goes beyond simple username and password combinations and can include multi-factor authentication, role-based access control (RBAC), and strong password policies.
FR 2: Use Control (UC): Once a user or system is authenticated, their actions must be restricted to only what is necessary for their role. This principle of least privilege ensures that even if an account is compromised, the potential for damage is limited.
FR 3: System Integrity (SI): This FR focuses on protecting the IACS from unauthorized modification. This includes ensuring the integrity of software, firmware, and configuration data. Mechanisms like digital signatures and secure boot processes are crucial for maintaining system integrity.
FR 4: Data Confidentiality (DC): While availability is often the top priority in OT, data confidentiality is also critical, especially for sensitive process information or intellectual property. This requirement addresses the need to protect data from unauthorized disclosure, both in transit and at rest, through measures like encryption.
FR 5: Restricted Data Flow (RDF): This foundational requirement is the cornerstone of network segmentation. By controlling the flow of data between different parts of the IACS, the impact of a security breach can be contained. This is where the concept of zones and conduits becomes vital.
FR 6: Timely Response to Events (TRE): No security system is impenetrable. Therefore, it is essential to have mechanisms in place to detect and respond to security incidents in a timely manner. This includes logging and monitoring security events, as well as having a well-defined incident response plan.
FR 7: Resource Availability (RA): In the world of industrial control, availability is king. This FR addresses the need to protect the IACS from attacks that could deny or degrade its essential services. This includes protecting against denial-of-service (DoS) attacks and ensuring that the system can recover quickly from a failure.
Zones and Conduits: The Art of Network Segmentation
One of the most powerful concepts introduced by IEC 62443 is the use of zones and conduits for network segmentation. This approach moves away from the traditional, flat network architecture and creates a more defensible and resilient environment.
Zones: A zone is a logical grouping of assets that share common security requirements. These assets can be physical (e.g., a specific production line) or logical (e.g., a group of servers with the same function). By grouping assets into zones, you can apply targeted security controls and limit the impact of a breach to a specific area.
Conduits: A conduit is the communication path between two or more zones. By defining and securing these conduits, you can control the flow of information between zones, ensuring that only authorized traffic is allowed to pass.
A Practical Example: Securing a SCADA System with Zones and Conduits
Let’s consider a typical SCADA system used for monitoring and controlling a remote pipeline. A traditional network architecture might have all devices connected to a single network, making it vulnerable to a single point of failure.
By applying the zones and conduits concept, we can create a much more secure architecture:
Block Diagram 1: SCADA System Segmentation with IEC 62443 Zones and Conduits
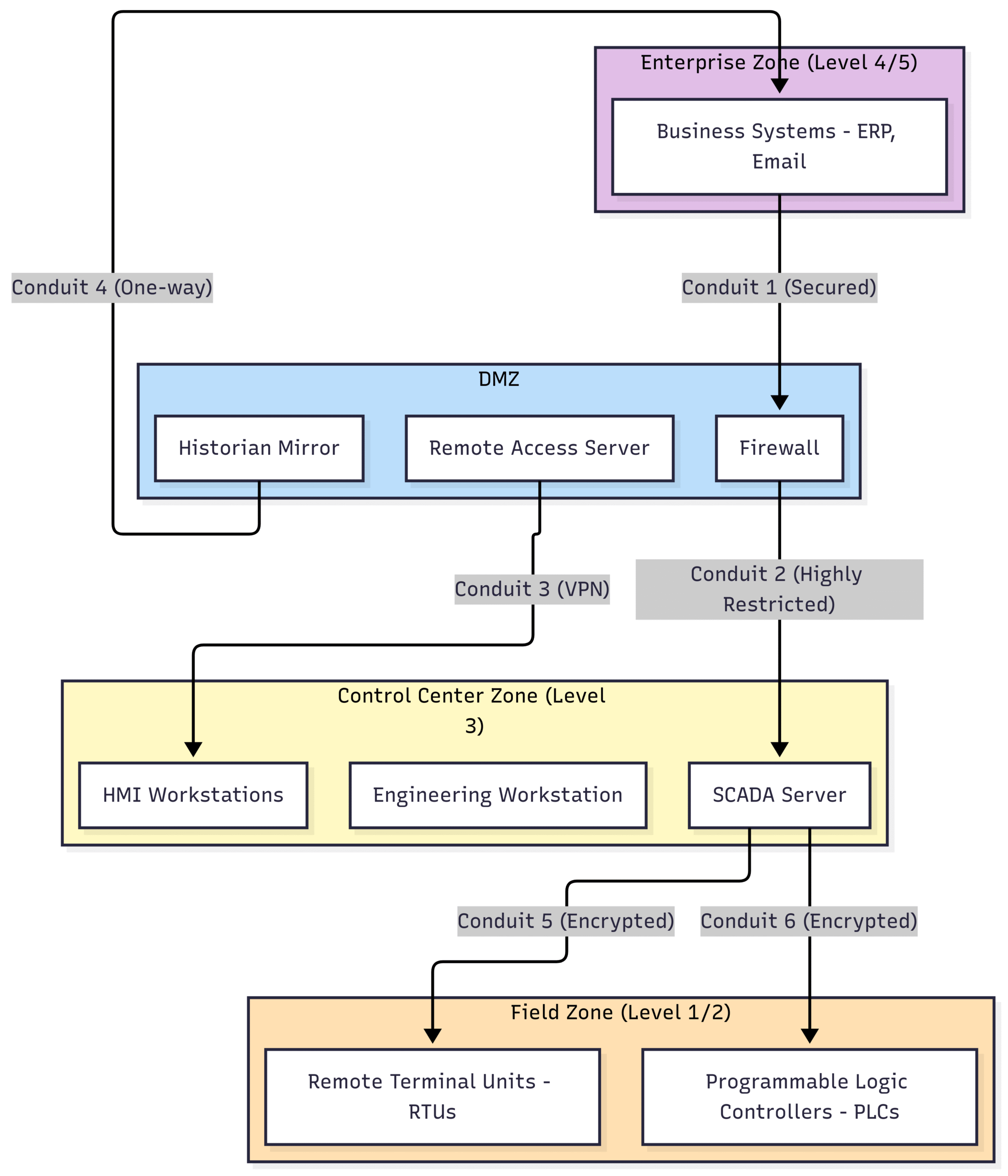
In this segmented architecture:
The Enterprise Zone contains the corporate IT systems, which are separated from the OT environment by a Demilitarized Zone (DMZ).
The DMZ acts as a buffer, containing servers that need to be accessed from both the IT and OT networks, such as a remote access server and a mirror of the data historian.
The Control Center Zone houses the critical SCADA servers and human-machine interface (HMI) workstations. Access to this zone is tightly controlled.
The Field Zone contains the RTUs and PLCs that are directly connected to the pipeline equipment.
Each conduit between these zones would have specific security controls, such as firewalls with strict access control lists, encrypted communication protocols, and intrusion detection systems. This ensures that a compromise in the Enterprise Zone does not automatically lead to a compromise of the critical control systems in the Field Zone.
The IEC 62443 Lifecycle: A Continuous Journey of Improvement
Implementing IEC 62443 is not a one-time project; it is a continuous lifecycle of assessment, implementation, and maintenance. The standard outlines a cyclical process to ensure that cybersecurity remains effective in the face of evolving threats and changing technologies.
The IEC 62443 Cybersecurity Lifecycle:
Assess: The lifecycle begins with a thorough risk assessment to identify and prioritize the cybersecurity risks to the IACS. This involves identifying critical assets, potential threats and vulnerabilities, and the potential impact of a security breach.
Implement: Based on the results of the risk assessment, appropriate security controls are implemented. This includes technical controls (e.g., firewalls, intrusion detection systems), as well as policies and procedures. The concept of Security Levels (SLs) is crucial here. IEC 62443 defines four Security Levels, from SL 1 (protection against casual or coincidental violation) to SL 4 (protection against intentional violation using sophisticated means with extended resources). The target SL for each zone is determined by the risk assessment.
Maintain: Once security controls are in place, they must be continuously monitored and maintained to ensure their effectiveness. This includes patch management, vulnerability scanning, and regular security audits.
Improve: The cybersecurity landscape is constantly changing, so it is essential to have a process for continuous improvement. This involves regularly reviewing the risk assessment, updating security controls as needed, and learning from security incidents.
Diving Deeper: The Risk Assessment Process
A thorough risk assessment is the foundation of a successful IEC 62443 implementation. The standard provides a structured approach to risk assessment, which typically involves the following steps:
System under Consideration (SuC) Definition: Clearly define the scope of the assessment, including the boundaries of the IACS and all its components.
High-Level Risk Assessment: Identify the most critical assets and the worst-case scenarios. This helps to prioritize the more detailed assessment efforts.
Detailed Risk Assessment: For each zone and conduit, identify potential threats and vulnerabilities. Analyze the likelihood and impact of each risk to determine the required Security Level.
Risk Mitigation: Develop a plan to mitigate the identified risks. This may involve implementing new security controls, improving existing ones, or accepting a certain level of residual risk.
Challenges and Best Practices for Implementing IEC 62443
While the IEC 62443 framework provides a clear roadmap for securing industrial control systems, the journey to full implementation can have its challenges.
Common Challenges:
Legacy Systems: Many industrial environments rely on legacy systems that were not designed with cybersecurity in mind. Retrofitting these systems with modern security controls can be difficult and expensive.
Skills Gap: There is a shortage of cybersecurity professionals with expertise in both IT and OT environments.
Cultural Resistance: The convergence of IT and OT can lead to cultural clashes between engineering and IT departments, each with different priorities and perspectives.
Cost and Resources: Implementing a comprehensive cybersecurity program can be a significant investment in terms of both time and money.
Best Practices for Success:
Executive Sponsorship: Strong support from executive leadership is essential for securing the necessary resources and driving the cultural change required for a successful cybersecurity program.
Cross-Functional Teams: Establish a cross-functional team with representatives from engineering, operations, and IT to ensure that all perspectives are considered.
Start with a Pilot Project: Begin with a smaller, less critical system to gain experience and demonstrate the value of the IEC 62443 framework before rolling it out to the entire organization.
Leverage Vendor Expertise: Work closely with IACS vendors who have experience in implementing the IEC 62443 standard. Many vendors now offer products and services that are certified to be compliant with the standard.
Continuous Training and Awareness: Regularly train employees on cybersecurity best practices and create a culture of security awareness throughout the organization.
The Future of Industrial Cybersecurity is Here
The increasing digitization of the industrial world brings with it immense opportunities, but also significant risks. The IEC 62443 framework provides a comprehensive and internationally recognized approach to managing these risks and securing the critical infrastructure that we all rely on.
By embracing the principles of shared responsibility, defense-in-depth, and a continuous lifecycle of improvement, organizations can build a resilient and secure industrial environment that is prepared to face the challenges of the 21st century. The journey to IEC 62443 compliance may seem daunting, but the long-term benefits of a secure and reliable industrial control system are well worth the effort. The future of our industrial world depends on it.
