Top 15 Cyber Threats in Process Industries and How IEC 62443 Mitigates Them
The convergence of Information Technology (IT) and Operational Technology (OT) in process industries has unlocked unprecedented efficiency and innovation. However, this digital transformation has also exposed critical infrastructure to a new and evolving landscape of cyber threats. A successful attack on a process control network could lead to production downtime, equipment damage, environmental incidents, and even loss of life. To counter these risks, the internationally recognized IEC 62443 series of standards provides a comprehensive framework for securing Industrial Automation and Control Systems (IACS). This blog post will delve into the top 15 cyber threats facing process industries and explore how implementing the principles of IEC 62443 can provide robust mitigation.
Understanding the Core Principles of IEC 62443
Before we explore the specific threats, it’s crucial to grasp the fundamental concepts of the IEC 62443 standard. It is not a single document but a series of standards that take a holistic, risk-based approach to cybersecurity. Key to its philosophy are:
Defense-in-Depth: This strategy involves layering multiple security controls. If one layer is breached, subsequent layers are in place to thwart an attack.
Zones and Conduits: IEC 62443 advocates for segmenting the IACS into logical zones containing assets with similar security requirements. Communication between these zones is restricted to defined conduits, where security controls are applied.
Security Levels (SLs): The standard defines four Security Levels (SL 1-4) that specify the required security capabilities to protect against different threat actors, from casual hackers to nation-states.
Lifecycle Approach: IEC 62443 addresses security throughout the entire lifecycle of an IACS, from initial design and implementation to operation, maintenance, and decommissioning.
Shared Responsibility: It emphasizes that cybersecurity is a shared responsibility among all stakeholders, including asset owners, system integrators, and product suppliers.
This framework provides a structured and systematic way to manage and reduce cybersecurity risks in process industries.
High-Level View: Zones and Conduits in Action
To visualize how IEC 62443 structures a defense, consider a typical process plant network.
Block Diagram 1: High-Level Zone and Conduit Model based on IEC 62443

Description of Block Diagram 1: This diagram illustrates a simplified, yet powerful, zone and conduit architecture. The Enterprise Zone is the corporate IT network. The Process Control Zone is the core OT environment. The Safety Instrumented System (SIS) Zone contains the most critical safety functions and is highly restricted. The Industrial Demilitarized Zone (IDMZ) acts as a buffer, controlling all data flow between the IT and OT networks. Each connection between zones is a “conduit” protected by firewalls or other security measures, ensuring that a breach in a less critical zone does not automatically compromise more critical ones.
The Top 15 Cyber Threats and their Mitigation with IEC 62443
Here are 15 of the most significant cyber threats to process industries and how the IEC 62443 standard provides a framework for their mitigation.
1. Malware and Ransomware Infections
Malicious software, including ransomware, can be introduced into an IACS environment through various vectors, such as infected USB drives, phishing emails, or compromised laptops. A successful infection can disrupt or halt production, leading to significant financial losses.
How IEC 62443 Mitigates:
IEC 62443-3-3: System Security Requirements and Security Levels: This part of the standard mandates controls such as malware protection, which can be implemented through application whitelisting and antivirus software specifically designed for industrial environments.
IEC 62443-2-1: Establishing an IACS Security Program: This section requires the development of policies and procedures for managing removable media and portable devices, a common entry point for malware.
Zone and Conduit Architecture: By segmenting the network, the impact of a malware outbreak can be contained within a single zone, preventing its propagation to more critical parts of the system.
2. Unauthorized Access
Unauthorized individuals, both internal and external, gaining access to sensitive control systems can lead to manipulation of processes, theft of intellectual property, or sabotage.
How IEC 62443 Mitigates:
IEC 62443-3-3: This standard requires robust access control measures, including unique user identification and authentication, role-based access control (RBAC), and the principle of least privilege, ensuring users only have access to the information and functions necessary for their roles.
IEC 62443-4-2: Technical Security Requirements for IACS Components: This part specifies that devices such as PLCs and controllers must have built-in security features to enforce access control at the component level.
3. Supply Chain Attacks
Attackers can compromise IACS components, software, or systems during the manufacturing or integration process. This can introduce hidden backdoors or vulnerabilities that are difficult to detect.
How IEC 62443 Mitigates:
IEC 62443-4-1: Secure Product Development Lifecycle Requirements: This standard ensures that vendors and system integrators follow secure development practices, including threat modeling, secure coding standards, and vulnerability management, reducing the likelihood of compromised products entering the supply chain.
IEC 62443-2-4: Security Program Requirements for IACS Service Providers: This section outlines the security requirements for service providers who have access to the IACS, ensuring they adhere to the asset owner’s security policies.
4. Insider Threats
Disgruntled or negligent employees, contractors, or other insiders with legitimate access can intentionally or unintentionally cause significant damage to process control systems.
How IEC 62443 Mitigates:
IEC 62443-2-1: This standard requires the implementation of a comprehensive security program that includes personnel security measures such as background checks, security awareness training, and clear policies for revoking access when an individual’s employment is terminated.
IEC 62443-3-3: The requirement for audit logs and monitoring helps in detecting suspicious activities from insiders and provides a trail for forensic analysis.
5. Denial-of-Service (DoS) Attacks
DoS attacks aim to make a system or network resource unavailable to its intended users by overwhelming it with traffic or malformed packets. In a process environment, this could crash an HMI or a critical controller.
How IEC 62443 Mitigates:
IEC 62443-3-3: This part of the standard requires systems to be resilient to DoS attacks. This can be achieved through network segmentation, rate limiting of traffic, and the use of industrial firewalls that can filter malicious traffic.
Zone and Conduit Model: Proper segmentation ensures that a DoS attack targeting a less critical zone, like the corporate network, does not impact the availability of the process control network.
Block Diagram 2: Mitigating DoS Attacks with Network Segmentation
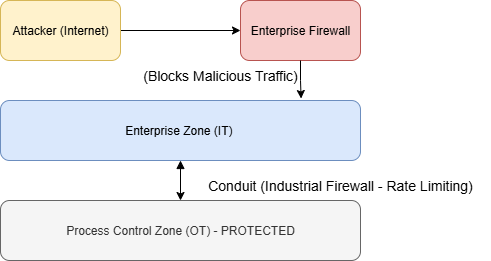
Description of Block Diagram 2: This diagram shows how network segmentation and layered firewalls can mitigate a DoS attack. The enterprise firewall provides the first line of defense. The industrial firewall at the conduit between the IT and OT zones can be configured with specific rules to limit the rate of traffic and filter out patterns associated with DoS attacks, protecting the critical process control zone.
6. Wireless Communication Vulnerabilities
The increasing use of wireless technologies in industrial environments introduces new attack vectors if not properly secured. Attackers could intercept or jam wireless signals, or gain unauthorized access to the network.
How IEC 62443 Mitigates:
IEC 62443-3-3: This standard has specific requirements for the security of wireless communications, including the use of strong encryption (like WPA3), mutual authentication between devices and the network, and measures to detect rogue access points.
7. Cloud Security Risks
As process data is increasingly stored and analyzed in the cloud, new risks related to data breaches, insecure APIs, and misconfigurations emerge.
How IEC 62443 Mitigates:
IEC 62443-2-1 and -3-2 (Risk Assessment): While not a cloud-specific standard, the risk assessment methodologies in IEC 62443 can be extended to cloud environments. This involves identifying and assessing the risks associated with cloud service providers and implementing appropriate controls. Secure conduits must be established between the on-premise IACS and the cloud platform.
8. Data Integrity Attacks
Attackers may not just steal data but may also try to manipulate it. For example, altering a sensor reading or a recipe in a batch process could have catastrophic consequences.
How IEC 62443 Mitigates:
IEC 62443-3-3: This part of the standard requires measures to ensure data integrity, such as using cryptographic hashes or digital signatures to verify that data has not been tampered with in transit or at rest.
9. Intellectual Property (IP) Theft
Process industries often have valuable intellectual property in the form of proprietary formulas, production processes, and operational data. Attackers may target IACS to steal this information.
How IEC 62443 Mitigates:
Robust Access Control and Network Segmentation: By implementing the access control and segmentation principles of IEC 62443, organizations can restrict access to sensitive IP to only authorized personnel and systems, making it much harder for attackers to exfiltrate this data.
10. Social Engineering and Phishing
Attackers often target the human element, using deception to trick employees into revealing credentials, installing malware, or providing access to secure areas.
How IEC 62443 Mitigates:
IEC 62443-2-1: This standard mandates comprehensive security awareness training for all personnel, including how to recognize and respond to social engineering and phishing attempts.
Block Diagram 3: The Human Firewall in a Social Engineering Attack
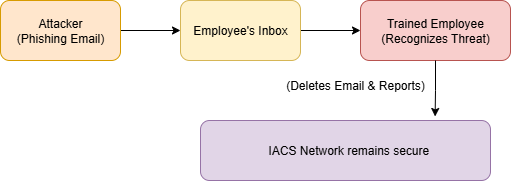
Description of Block Diagram 3: This conceptual diagram highlights the importance of the “human firewall.” Even with technical controls in place, a well-crafted phishing email might reach an employee. A properly trained employee, as mandated by IEC 62443-2-1, becomes the last line of defense, recognizing the threat and preventing the attack from succeeding.
11. Physical Security Breaches
Unauthorized physical access to control rooms, server racks, or field devices can lead to immediate and severe consequences.
How IEC 62443 Mitigates:
IEC 62443-3-3: While primarily a cybersecurity standard, it acknowledges the importance of physical security as a foundational layer. It requires physical security controls to be in place to protect critical assets.
12. Vulnerabilities in Legacy Systems
Many process plants still rely on legacy control systems that were designed before cybersecurity was a major concern. These systems often have known vulnerabilities that cannot be easily patched.
How IEC 62443 Mitigates:
Risk Assessment and Compensating Controls: IEC 62443’s risk assessment process (IEC 62443-3-2) helps in identifying the risks associated with legacy systems. When patching is not feasible, the standard guides the implementation of compensating controls, such as network segmentation to isolate the legacy system and intrusion detection systems to monitor for anomalous behavior.
Block Diagram 4: Protecting Legacy Systems with Compensating Controls
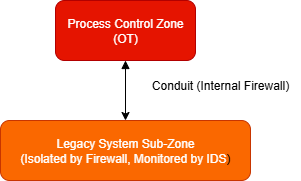
Description of Block Diagram 4: This diagram shows how a legacy system can be placed in its own “sub-zone” within the broader process control zone. An internal firewall restricts traffic to only what is absolutely necessary for the legacy system to function. An Intrusion Detection System (IDS) can monitor the traffic for any signs of an attack, providing a compensating control where patching is not possible.
13. Insecure Third-Party Remote Access
Providing remote access to vendors and service providers is often necessary for maintenance and support, but it can create a significant security risk if not managed properly.
How IEC 62443 Mitigates:
IEC 62443-3-3: This standard requires secure remote access solutions that enforce strong authentication (ideally multi-factor), encryption of the communication channel, and logging of all remote access sessions.
IEC 62443-2-4: This section ensures that third-party service providers adhere to the organization’s security policies and procedures.
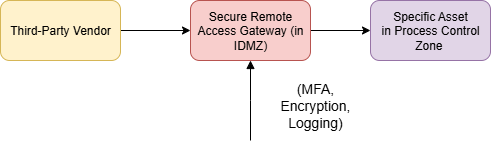
Block Diagram 5: Secure Remote Access for Third Parties

Description of Block Diagram 5: This diagram illustrates a secure remote access architecture. The third-party vendor does not have direct access to the process control network. Instead, they must connect through a secure remote access gateway located in the IDMZ. This gateway enforces multi-factor authentication (MFA), encrypts the entire session, and logs all activity for later review, providing a secure and auditable method for remote support.
14. Lack of Network Visibility and Monitoring
If you can’t see what’s happening on your network, you can’t detect or respond to an attack. Many OT networks lack the necessary tools for continuous monitoring.
How IEC 62443 Mitigates:
IEC 62443-3-3: This standard requires the implementation of security monitoring and event logging capabilities. This includes collecting logs from network devices, servers, and applications, and having a system in place to analyze these logs for signs of malicious activity.
15. Inadequate Incident Response Plan
When a cyber incident does occur, a slow and disorganized response can significantly increase the impact. Many organizations lack a well-defined and practiced incident response plan for their OT environments.
How IEC 62443 Mitigates:
IEC 62443-2-1: This section requires the development and maintenance of an incident response plan that is specifically tailored to the IACS environment. This plan should include procedures for detecting, containing, eradicating, and recovering from a cyber incident.
Conclusion: Building a Resilient Future with IEC 62443
The cyber threats facing process industries are real, persistent, and constantly evolving. A reactive approach to cybersecurity is no longer sufficient. The IEC 62443 standard provides a proactive and comprehensive framework for building resilience into the very fabric of industrial automation and control systems. By embracing its principles of defense-in-depth, network segmentation, and a lifecycle approach to security, organizations can significantly reduce their risk profile.
Adopting IEC 62443 is not just an IT or security initiative; it is a fundamental business imperative for any organization operating in the process industries. It is an investment in the safety of personnel, the protection of the environment, the continuity of operations, and the long-term viability of the business. The journey to full implementation may seem daunting, but it begins with a commitment to understanding the risks and taking a structured, standards-based approach to mitigating them. The time to start building a more secure and resilient future for your process control environment is now.
