An unsettling reality for the oil and gas industry is that the very systems controlling immense physical processes, from extraction and refining to transportation and distribution, are increasingly vulnerable to cyberattacks. The convergence of Information Technology (IT) and Operational Technology (OT) has brought unprecedented efficiency but has also flung open the doors to a new breed of threats. A single breach can have catastrophic consequences, leading to production downtime, environmental disasters, and even loss of life. In this high-stakes environment, a reactive or single-layered security approach is not just inadequate; it’s an invitation to disaster. This is where the principles of Defense in Depth, guided by the internationally recognized IEC 62443 standard, provide a robust and resilient framework for securing critical infrastructure.
This comprehensive guide will delve into the intricacies of implementing a Defense in Depth strategy in the oil and gas sector, using the IEC 62443 standard as a blueprint. We will explore the foundational concepts, practical implementation steps, and the crucial role of a multi-layered security posture in safeguarding your operations.
The Fortress Mentality: Understanding Defense in Depth
At its core, Defense in Depth is a security strategy that layers multiple, independent security controls to protect an asset. The core idea is that if one layer of defense is breached, subsequent layers are in place to thwart the attack. Think of a medieval castle: it has a moat, a drawbridge, high walls, watchtowers, and guards at every gate. Each of these is a layer of defense. If an intruder crosses the moat, they still have to contend with the walls, the guards, and so on.
In the context of cybersecurity, these layers are not physical but a combination of technical, administrative, and physical controls. The primary goal is to provide redundancy in security, ensuring that a failure in one control does not lead to a complete compromise of the system.
The Layers of Defense in Depth
A typical Defense in Depth model for an industrial control system (ICS) environment, prevalent in the oil and gas industry, includes the following layers:
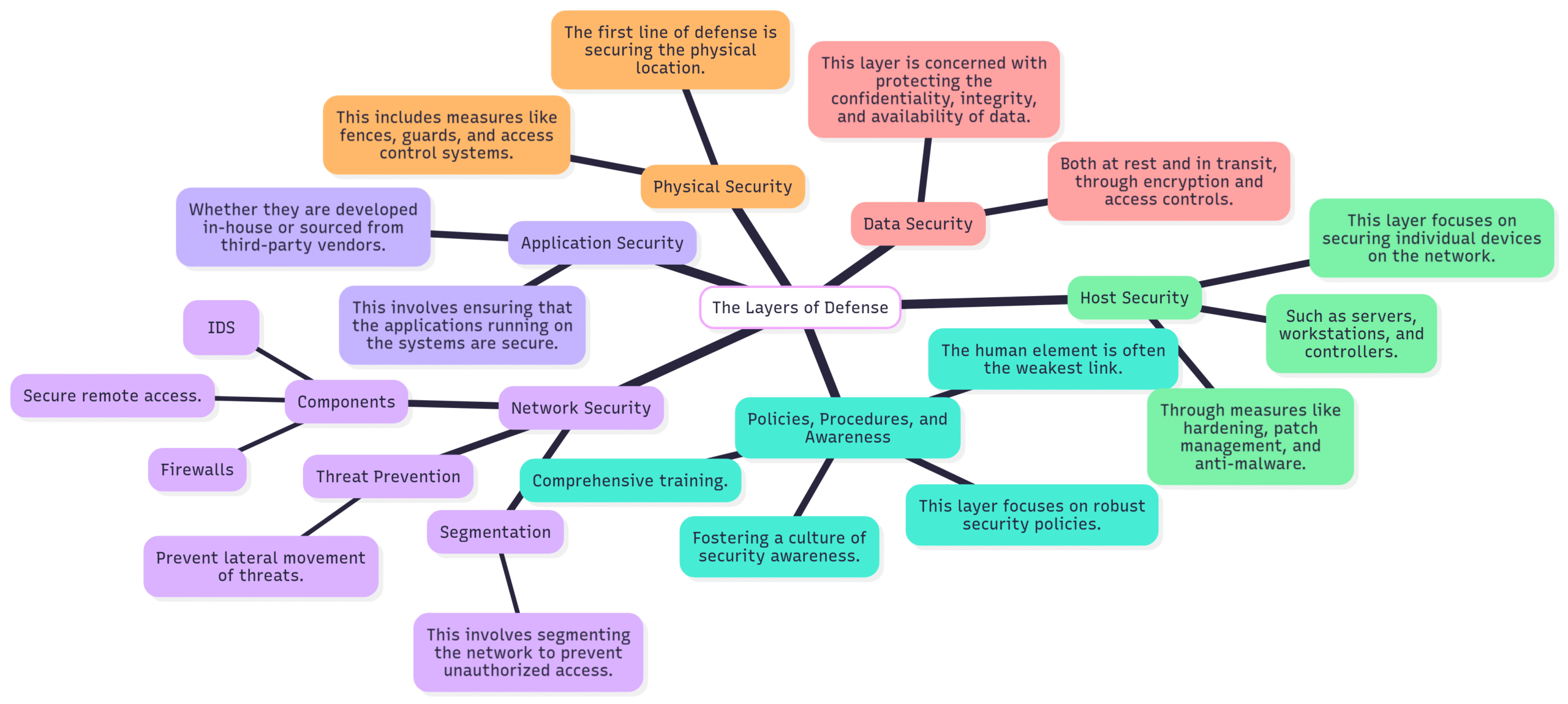
Policies, Procedures, and Awareness: The human element is often the weakest link. This layer focuses on robust security policies, comprehensive training, and fostering a culture of security awareness.
Physical Security: The first line of defense is securing the physical location of critical assets through measures like fences, guards, and access control systems.
Network Security: This involves segmenting the network to prevent unauthorized access and the lateral movement of threats. Firewalls, intrusion detection systems (IDS), and secure remote access are key components.
Host Security: This layer focuses on securing individual devices on the network, such as servers, workstations, and controllers, through measures like hardening, patch management, and anti-malware.
Application Security: This involves ensuring that the applications running on the systems are secure, whether they are developed in-house or sourced from third-party vendors.
Data Security: This layer is concerned with protecting the confidentiality, integrity, and availability of data, both at rest and in transit, through encryption and access controls.
IEC 62443: The Gold Standard for OT Cybersecurity
While Defense in Depth provides the “what,” the IEC 62443 standard provides the “how.” It is a series of standards, technical reports, and related information that define procedures for implementing electronically secure Industrial Automation and Control Systems (IACS). Developed by a global team of experts, it is widely regarded as the leading standard for OT cybersecurity.
What makes IEC 62443 particularly effective for the oil and gas industry is its risk-based approach. It doesn’t prescribe a one-size-fits-all solution. Instead, it provides a framework for assessing risk and applying appropriate security controls.
Key Concepts of IEC 62443
To effectively leverage IEC 62443, it’s essential to understand its core concepts:
Security Levels (SLs): IEC 62443 defines four Security Levels (SL 1 to SL 4) that represent the level of security robustness required for a particular system or component. The target SL is determined based on a risk assessment.
SL 1: Protection against casual or coincidental violation.
SL 2: Protection against intentional violation using simple means.
SL 3: Protection against intentional violation using sophisticated means.
SL 4: Protection against intentional violation using sophisticated means with extended resources.
Zones and Conduits: This is the cornerstone of implementing Defense in Depth with IEC 62443. The standard advocates for segmenting the IACS into logical groups of assets called zones that share common security requirements. All communication between zones must occur through defined pathways called conduits, where security controls can be applied.
Foundational Requirements (FRs): IEC 62443 outlines seven Foundational Requirements that form the basis of a secure IACS:
Identification and Authentication Control (IAC): Verifying the identity of users and devices.
Use Control (UC): Enforcing privileges and access rights.
System Integrity (SI): Ensuring the integrity of the system and its data.
Data Confidentiality (DC): Protecting the confidentiality of data.
Restricted Data Flow (RDF): Controlling the flow of data between zones.
Timely Response to Events (TRE): Detecting and responding to security events in a timely manner.
Resource Availability (RA): Ensuring the availability of critical resources.
Figure 2: A block diagram illustrating the concept of Zones and Conduits in IEC 62443.
Implementing Defense in Depth with IEC 62443 in Oil and Gas: A Practical Guide
Now, let’s bring these concepts together and outline a practical, step-by-step approach to achieving Defense in Depth in an oil and gas facility using the IEC 62443 framework.
Step 1: Risk Assessment – The Starting Point
Before implementing any security controls, you need to understand your risks. A thorough risk assessment will help you identify your critical assets, potential threats, and existing vulnerabilities. This assessment will be the basis for determining the target Security Levels for different parts of your plant.
For an oil and gas facility, critical assets could include:
Safety Instrumented Systems (SIS): These are the last line of defense against catastrophic failures.
Distributed Control Systems (DCS): These control the core processes of the plant.
Supervisory Control and Data Acquisition (SCADA) Systems: These are used for monitoring and controlling geographically dispersed assets like pipelines.
Programmable Logic Controllers (PLCs): These control specific equipment and processes.
Step 2: Network Segmentation – Building Your Digital Fortress
Once you have identified your critical assets and their required Security Levels, the next step is to segment your network into zones. This is arguably the most critical step in implementing Defense in Depth.
A typical oil and gas architecture can be segmented into the following zones:
Enterprise Zone (IT Zone): This is the corporate network where standard IT systems reside. It typically has a lower Security Level (e.g., SL 1 or SL 2).
Industrial Demilitarized Zone (IDMZ): This acts as a buffer zone between the Enterprise Zone and the Process Control Zone. It houses systems that need to be accessed from both zones, such as data historians and remote access servers. The IDMZ is a critical component for enforcing restricted data flow.
Process Control Zone (OT Zone): This is where the most critical assets, like the DCS, SIS, and PLCs, reside. This zone will have the highest Security Level (e.g., SL 3 or SL 4).
Safety Zone: In some cases, the SIS may be placed in its own dedicated zone with the highest level of security to ensure its integrity and availability.
Field Device Zone: This zone includes the sensors, actuators, and other field devices that are connected to the controllers.
Communication between these zones should be strictly controlled through conduits, which are essentially firewalls and other security devices that enforce access control policies.
Figure 3: A detailed block diagram showing network segmentation in an oil and gas facility based on IEC 62443.
Step 3: Securing the Layers – Applying the Foundational Requirements
With your network segmented, you can now apply the seven Foundational Requirements of IEC 62443 to each layer of your Defense in Depth strategy.
Layer 1: Policies, Procedures, and People
IEC 62443-2-1: Security Program Requirements for IACS Asset Owners: This part of the standard provides guidance on establishing, implementing, maintaining, and improving a cybersecurity management system.
Actionable Steps:
Develop a comprehensive cybersecurity policy that is aligned with your business objectives.
Implement a security awareness training program for all employees and contractors.
Establish clear roles and responsibilities for cybersecurity.
Develop and regularly test an incident response plan.
Layer 2: Physical Security
While not explicitly detailed in IEC 62443, physical security is a prerequisite for cybersecurity.
Actionable Steps:
Implement physical access controls to sensitive areas like control rooms and data centers.
Use surveillance cameras to monitor critical locations.
Secure all physical ports on control system devices.
Layer 3: Network Security
IEC 62443-3-3: System Security Requirements and Security Levels: This standard defines the security requirements for systems based on their target Security Level.
Actionable Steps:
Deploy firewalls at the conduits to enforce strict access control rules between zones.
Implement an Intrusion Detection and Prevention System (IDS/IPS) to monitor network traffic for malicious activity.
Establish a secure remote access solution with multi-factor authentication for any access to the Process Control Zone.
Disable all unused ports and services on network devices.
Layer 4: Host Security
IEC 62443-4-2: Technical Security Requirements for IACS Components: This part of the standard outlines the security requirements for the individual components of the IACS.
Actionable Steps:
Harden all operating systems and applications by disabling unnecessary services and accounts.
Implement a robust patch management program to ensure that all systems are up-to-date with the latest security patches. This can be challenging in an OT environment, so a risk-based approach is necessary.
Deploy application whitelisting to ensure that only authorized applications can run on critical systems.
Use anti-malware solutions that are specifically designed for OT environments.
Layer 5: Application Security
IEC 62443-4-1: Secure Product Development Lifecycle Requirements: This standard provides guidance to vendors on how to develop secure products.
Actionable Steps:
When procuring new systems or components, give preference to vendors who can demonstrate compliance with IEC 62443-4-1.
For in-house developed applications, implement a secure software development lifecycle (SSDLC).
Perform regular vulnerability scans of all applications.
Layer 6: Data Security
This is covered under the Data Confidentiality (DC) and System Integrity (SI) Foundational Requirements.
Actionable Steps:
Encrypt all sensitive data, both at rest and in transit.
Implement data integrity checks to ensure that data has not been tampered with.
Enforce strict access controls to sensitive data.
Step 4: Continuous Monitoring and Improvement
Defense in Depth is not a one-time project; it’s an ongoing process. The threat landscape is constantly evolving, and your security controls need to adapt accordingly.
Actionable Steps:
Implement a centralized logging and monitoring solution to collect and analyze security events from across your IACS environment.
Conduct regular security assessments and penetration testing to identify and address new vulnerabilities.
Stay up-to-date with the latest threat intelligence and security best practices.
Continuously review and improve your security policies and procedures.
Conclusion: Building a Resilient Future for Oil and Gas
The oil and gas industry is at a critical juncture. The benefits of digital transformation are undeniable, but so are the risks. By embracing a Defense in Depth strategy, guided by the robust framework of IEC 62443, organizations can build a resilient security posture that protects their people, their assets, and the environment.
Implementing a comprehensive cybersecurity program is a significant undertaking, but the cost of inaction is far greater. It requires a commitment from all levels of the organization, from the boardroom to the plant floor. By taking a proactive, multi-layered approach to security, the oil and gas industry can not only mitigate the risks of today but also build a secure and prosperous future.
