A Comprehensive Guide to IEC 62443 Certification for Your Process Plant
In the intricate and interconnected world of modern process plants, the convergence of operational technology (OT) and information technology (IT) has unlocked unprecedented efficiency and innovation. However, this digital transformation has also exposed critical industrial automation and control systems (IACS) to a new and ever-evolving landscape of cyber threats. A successful cyberattack on a process plant can have devastating consequences, ranging from production downtime and financial losses to catastrophic safety and environmental incidents. To navigate this high-stakes environment, a robust and internationally recognized framework for cybersecurity is not just an advantage—it’s a necessity. This is where the IEC 62443 series of standards comes into play, offering a comprehensive and risk-based approach to securing your most critical assets. This guide will walk you through everything you need to know about achieving IEC 62443 certification for your process plant, empowering you to build a resilient and secure industrial ecosystem.
What is IEC 62443 and Why is it Crucial for Process Plants?
The IEC 62443 standard is the leading international benchmark for the cybersecurity of IACS. Developed by the International Electrotechnical Commission (IEC), it provides a structured framework for asset owners, system integrators, and product manufacturers to manage and mitigate cybersecurity risks throughout the entire lifecycle of their industrial systems. Unlike generic IT security standards, IEC 62443 is specifically tailored to the unique operational realities and safety requirements of the OT environment found in process plants.
For process plants, which include industries such as oil and gas, chemical manufacturing, pharmaceuticals, and power generation, the stakes are exceptionally high. The potential impact of a cyber incident extends far beyond data breaches. A compromised control system could lead to:
Production Halts: Malicious actors could manipulate processes, leading to costly shutdowns and an inability to meet production targets.
Equipment Damage: Incorrect commands sent to critical equipment like turbines, reactors, or pumps could cause physical damage, requiring expensive repairs and lengthy downtime.
Safety Incidents: The manipulation of safety instrumented systems (SIS) could lead to catastrophic events, endangering personnel and the surrounding community.
Environmental Spills: Unauthorized access to control systems could result in the release of hazardous materials, causing significant environmental damage and regulatory fines.
Intellectual Property Theft: Process recipes, proprietary formulas, and other sensitive operational data are valuable targets for industrial espionage.
By adopting the IEC 62443 framework, process plants can move from a reactive to a proactive cybersecurity posture. The standard provides a common language and a set of best practices that enable a systematic and measurable approach to securing the IACS.
Deconstructing the IEC 62443 Standard: A Multi-layered Approach
The IEC 62443 series is not a single document but a collection of standards organized into four main categories, each addressing a different aspect of IACS cybersecurity. This layered approach ensures that all stakeholders in the industrial ecosystem have clear guidance on their roles and responsibilities.
Part 1: General: This section provides the foundational concepts, models, and terminology used throughout the standard. It sets the stage for understanding the principles of IACS cybersecurity.
Part 2: Policies and Procedures: This part focuses on the human element of cybersecurity, outlining the requirements for establishing and maintaining a robust Cybersecurity Management System (CSMS). For process plant operators, IEC 62443-2-1 is particularly important as it details the requirements for an IACS asset owner’s cybersecurity program.
Part 3: System Security: This is a critical section for the design and implementation of secure IACS. IEC 62443-3-2 guides organizations on how to conduct a thorough risk assessment and define security zones and conduits. IEC 62443-3-3 specifies the system security requirements and security levels (SLs).
Part 4: Component Security: This part is primarily aimed at product manufacturers and developers, outlining the requirements for the secure development of IACS components. IEC 62443-4-1 details the secure product development lifecycle requirements, while IEC 62443-4-2 specifies the technical security requirements for IACS components.
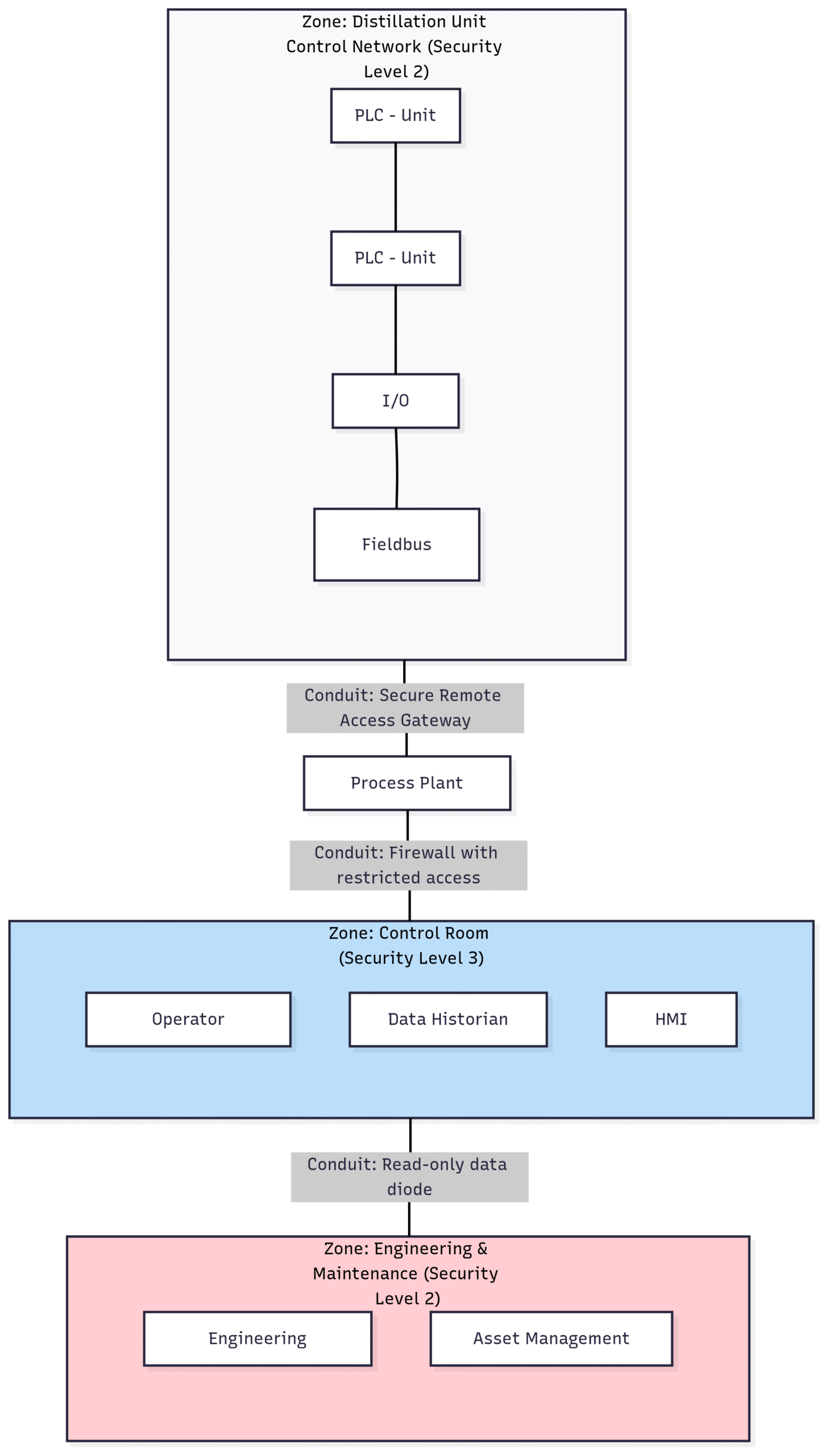
A key concept that underpins the entire standard is the Purdue Enterprise Reference Architecture, which provides a model for segmenting industrial networks into logical levels.
Block Diagram: The Purdue Model for IACS Segmentation
This diagram illustrates the hierarchical nature of a typical process plant network, with the IDMZ acting as a crucial buffer between the corporate IT network and the sensitive OT environment.
The Core Concepts: Zones, Conduits, and Security Levels
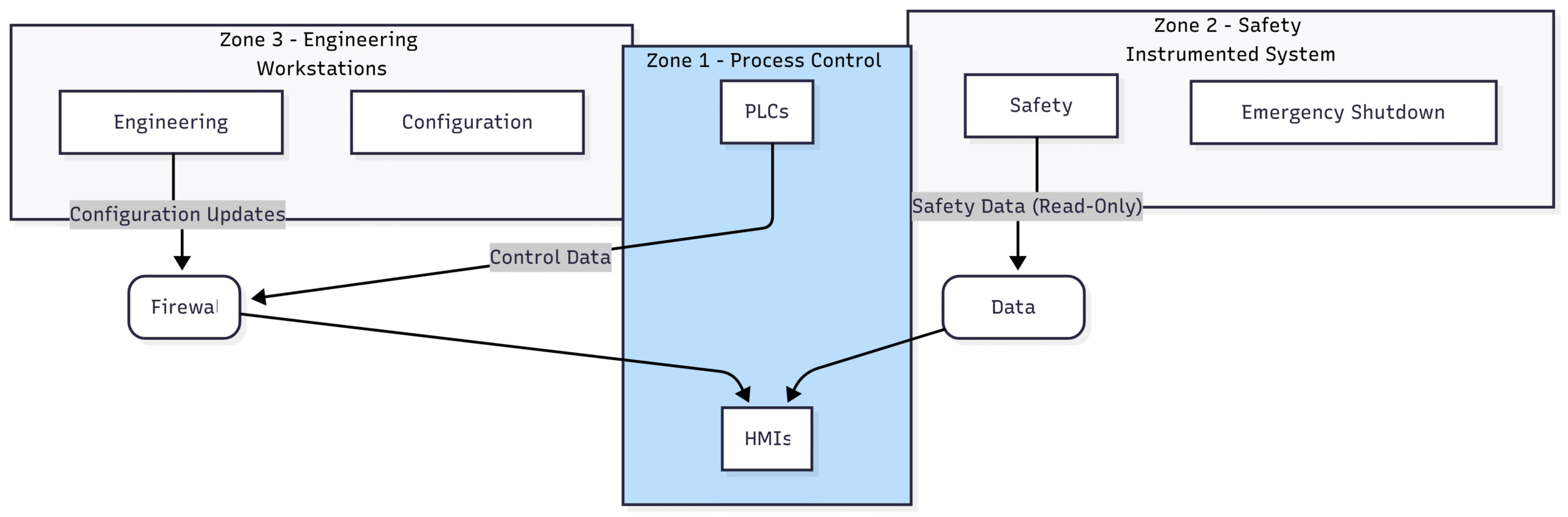
Two of the most fundamental and powerful concepts introduced by IEC 62443 are zones and conduits. This approach allows for a granular and targeted application of security controls, moving away from a one-size-fits-all security posture.
Zones: A zone is a logical grouping of assets that share common security requirements. These assets can be physical (e.g., all equipment in a specific processing unit) or logical (e.g., all systems related to a particular control function). By segmenting the IACS into zones, you can contain the impact of a security breach within a specific area, preventing it from propagating throughout the entire plant.
Conduits: Conduits are the communication pathways that connect different zones. The security of these conduits is paramount, as they represent potential entry points for attackers. IEC 62443 requires that all communication flowing through a conduit be secured and that security controls be implemented to protect the integrity and confidentiality of the data.
Block Diagram: Zones and Conduits in a Process Plant
This simplified diagram shows how a process plant’s IACS can be segmented into zones with controlled communication through secure conduits, such as firewalls and data diodes.
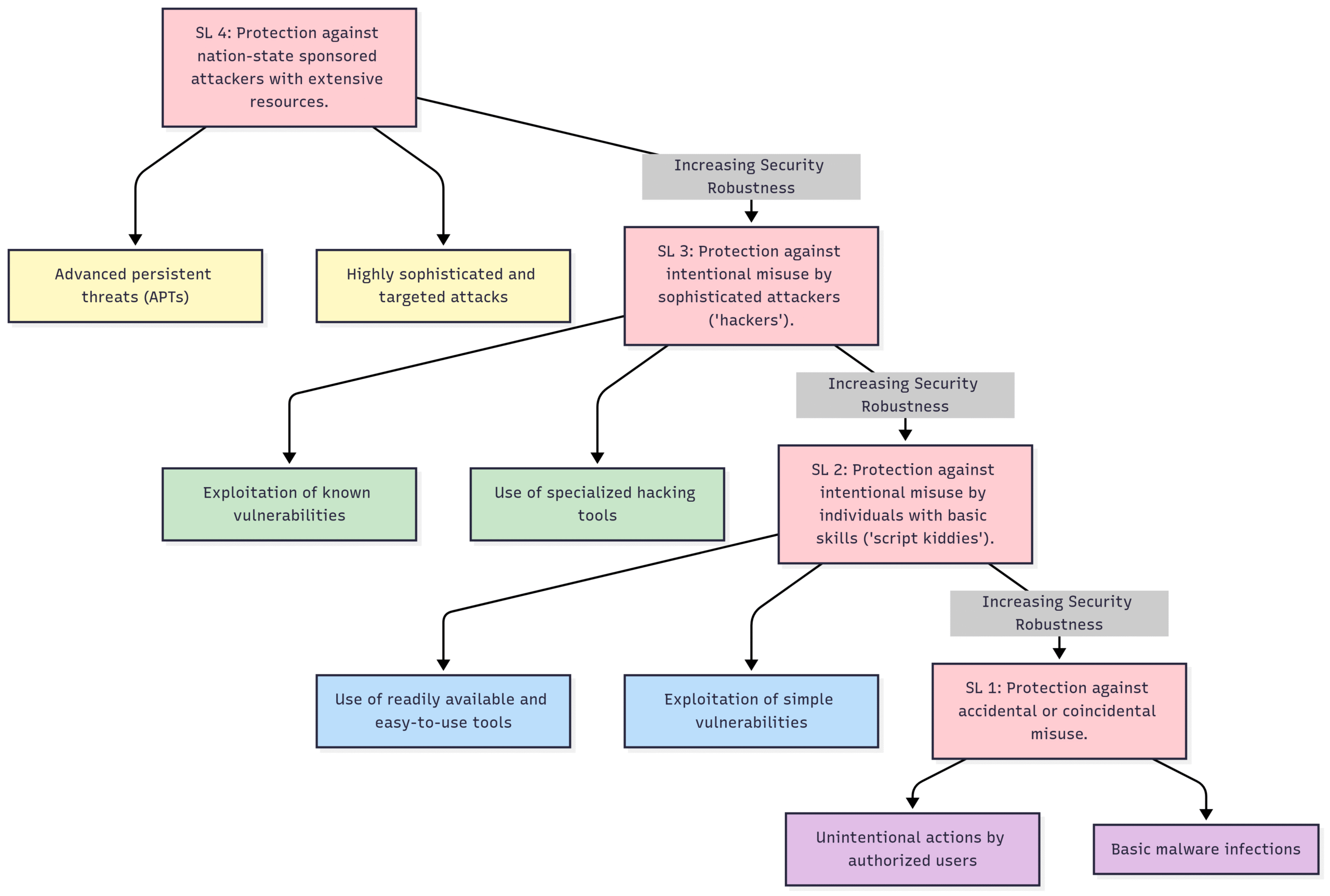
Complementing the concept of zones and conduits are the Security Levels (SLs). IEC 62443 defines four security levels to provide a graded approach to security, allowing organizations to apply controls that are commensurate with the identified risks.
Security Level 1 (SL1): Protects against casual or coincidental violations.
Security Level 2 (SL2): Protects against intentional violations with simple means, low resources, generic skills, and low motivation.
Security Level 3 (SL3): Protects against intentional violations with sophisticated means, moderate resources, IACS-specific skills, and moderate motivation.
Security Level 4 (SL4): Protects against intentional violations with sophisticated means, extensive resources, IACS-specific skills, and high motivation.
For each zone, a target security level (SL-T) is determined based on a thorough risk assessment. The achieved security level (SL-A) is then a measure of the security controls that have been implemented. The goal is to ensure that the SL-A meets or exceeds the SL-T for each zone.
The Journey to Certification: A Phased Approach
Achieving IEC 62443 certification is a journey, not a destination. It requires a sustained commitment from all levels of the organization and a systematic approach to implementation. The certification process can be broken down into several key phases:
Phase 1: Scoping and Initial Assessment
The first step is to define the scope of the certification. Will it cover the entire plant or a specific critical process unit? Once the scope is defined, a gap analysis should be conducted to assess the current state of your IACS cybersecurity against the requirements of the IEC 62443 standard. This initial assessment will identify areas of weakness and provide a roadmap for remediation.
Phase 2: Risk Assessment
This is the cornerstone of the IEC 62443 framework. A detailed risk assessment, as outlined in IEC 62443-3-2, must be performed to identify and prioritize cybersecurity risks. This involves:
System Characterization: Documenting the IACS assets, their interconnections, and their criticality to the process.
Threat Identification: Identifying potential threat sources, both internal and external.
Vulnerability Analysis: Identifying weaknesses in the system that could be exploited by threats.
Consequence Analysis: Determining the potential impact of a successful cyberattack on safety, production, and the environment.
Risk Determination: Calculating the level of risk for each identified scenario.
The results of the risk assessment will inform the selection of appropriate security controls and the determination of the target security levels for each zone.
Phase 3: Implementation of Security Controls
Based on the findings of the risk assessment, you will need to implement a range of technical and procedural security controls. These may include:
Network Segmentation: Implementing zones and conduits using firewalls, data diodes, and other network security technologies.
Access Control: Implementing strong authentication and authorization mechanisms to ensure that only authorized personnel can access critical systems.
System Hardening: Disabling unnecessary services and ports on servers and workstations to reduce the attack surface.
Malware Protection: Implementing application whitelisting and other measures to prevent the execution of unauthorized software.
Patch Management: Establishing a process for testing and applying security patches in a timely manner without disrupting operations.
Incident Response: Developing and practicing an incident response plan to ensure a coordinated and effective response to a security incident.
Security Awareness Training: Educating employees about cybersecurity risks and their role in protecting the IACS.
Phase 4: Auditing and Certification
Once the security controls have been implemented, you will need to engage an accredited third-party certification body to conduct an audit. The auditors will review your documentation, interview personnel, and perform technical tests to verify that your IACS meets the requirements of the IEC 62443 standard. If the audit is successful, you will be awarded an IEC 62443 certificate.
Block Diagram: The IEC 62443 Certification Lifecycle
This diagram illustrates the continuous nature of IEC 62443 compliance, emphasizing that certification is not a one-time event but an ongoing process of improvement.
Phase 5: Continuous Monitoring and Improvement
Cybersecurity is a dynamic field, and new threats and vulnerabilities emerge constantly. Therefore, maintaining IEC 62443 certification requires a commitment to continuous monitoring and improvement. This includes:
Regular Security Audits: Conducting periodic internal and external audits to ensure that security controls remain effective.
Threat Intelligence: Staying informed about the latest cyber threats and vulnerabilities that could affect your IACS.
Security Testing: Performing regular penetration testing and vulnerability assessments to identify and address new weaknesses.
Management of Change: Ensuring that any changes to the IACS are assessed for their impact on cybersecurity.
The Business Case for IEC 62443 Certification: Benefits and Challenges
Embarking on the IEC 62443 certification journey is a significant undertaking, but the benefits far outweigh the challenges.
Benefits of Certification:
Enhanced Security Posture: A demonstrable improvement in your plant’s resilience against cyber threats.
Reduced Risk of Incidents: A proactive approach to risk management that minimizes the likelihood and impact of a security breach.
Improved Operational Reliability: A more stable and secure control environment leads to increased uptime and productivity.
Regulatory Compliance: In many industries, compliance with standards like IEC 62443 is becoming a regulatory requirement.
Increased Stakeholder Confidence: Certification provides assurance to customers, investors, and insurers that you are taking cybersecurity seriously.
Competitive Advantage: In an increasingly security-conscious market, IEC 62443 certification can be a key differentiator.
Challenges to Consider:
Cost: Achieving and maintaining certification involves costs for consulting, training, technology, and audits.
Complexity: The IEC 62443 standard is comprehensive and can be complex to interpret and implement without expert guidance.
Resource Allocation: Certification requires a dedicated team with the right skills and expertise.
Cultural Change: Shifting from a traditional, air-gapped mindset to a security-conscious culture can be challenging.
Legacy Systems: Older IACS may not have been designed with cybersecurity in mind and may require significant upgrades or replacement.
Your Roadmap to a Secure Future
In the digital age, the security of your process plant’s industrial automation and control systems is inextricably linked to its safety, reliability, and profitability. IEC 62443 provides a clear and comprehensive roadmap for navigating the complexities of IACS cybersecurity. By embracing the principles of risk assessment, defense-in-depth, and continuous improvement, you can build a resilient and secure industrial environment that is prepared to face the challenges of tomorrow.
The journey to IEC 62443 certification is a strategic investment in the long-term viability of your process plant. It is a testament to your commitment to operational excellence and a clear signal to all stakeholders that you are a leader in the secure and responsible operation of critical infrastructure. Start your journey today and unlock a future of enhanced resilience and sustainable success.