IEC 62443 Policies and Procedures for Instrumentation Projects
In the intricate and interconnected world of industrial automation, the security of your instrumentation and control systems is no longer an afterthought—it’s a critical necessity. As cyber threats to operational technology (OT) environments become more sophisticated and prevalent, a reactive approach to cybersecurity is a recipe for disaster. This is where the IEC 62443 series of standards emerges as the definitive framework for establishing and maintaining a robust cybersecurity posture. This comprehensive guide will walk you through the essential policies and procedures of IEC 62443, with a specific focus on their application in instrumentation projects, equipping you with the knowledge to build a secure and resilient foundation for your industrial processes.
The increasing digitization of industrial processes, often referred to as Industry 4.0, has brought about unprecedented efficiency and productivity. However, this connectivity also exposes critical infrastructure to a new realm of vulnerabilities. A compromised instrumentation system can lead to catastrophic consequences, including production downtime, equipment damage, environmental incidents, and even threats to human safety. The IEC 62443 standards provide a structured and risk-based approach to mitigating these threats, ensuring the confidentiality, integrity, and availability of your industrial automation and control systems (IACS).
This blog post will delve into the core concepts of IEC 62443, breaking down its key components and offering practical guidance on their implementation within the context of instrumentation projects. We will explore the importance of a defense-in-depth strategy, the critical roles of asset owners, system integrators, and product suppliers, and the practical application of zones, conduits, and security levels. By the end of this article, you will have a thorough understanding of how to leverage IEC 62443 to develop and maintain a comprehensive cybersecurity program for your instrumentation systems.
Understanding the IEC 62443 Framework: A Holistic Approach to OT Cybersecurity
The IEC 62443 series is not a single, monolithic standard but rather a collection of documents organized into four main categories: General, Policies and Procedures, System, and Component. This structured approach ensures that all aspects of IACS cybersecurity are addressed, from foundational concepts to the specific security requirements for individual devices.
For instrumentation projects, a key takeaway is the principle of shared responsibility. The security of an IACS is not solely the responsibility of the asset owner or the system integrator. It is a collaborative effort that requires the active participation of all stakeholders, including the manufacturers of the instrumentation devices themselves.
The Four Pillars of IEC 62443:
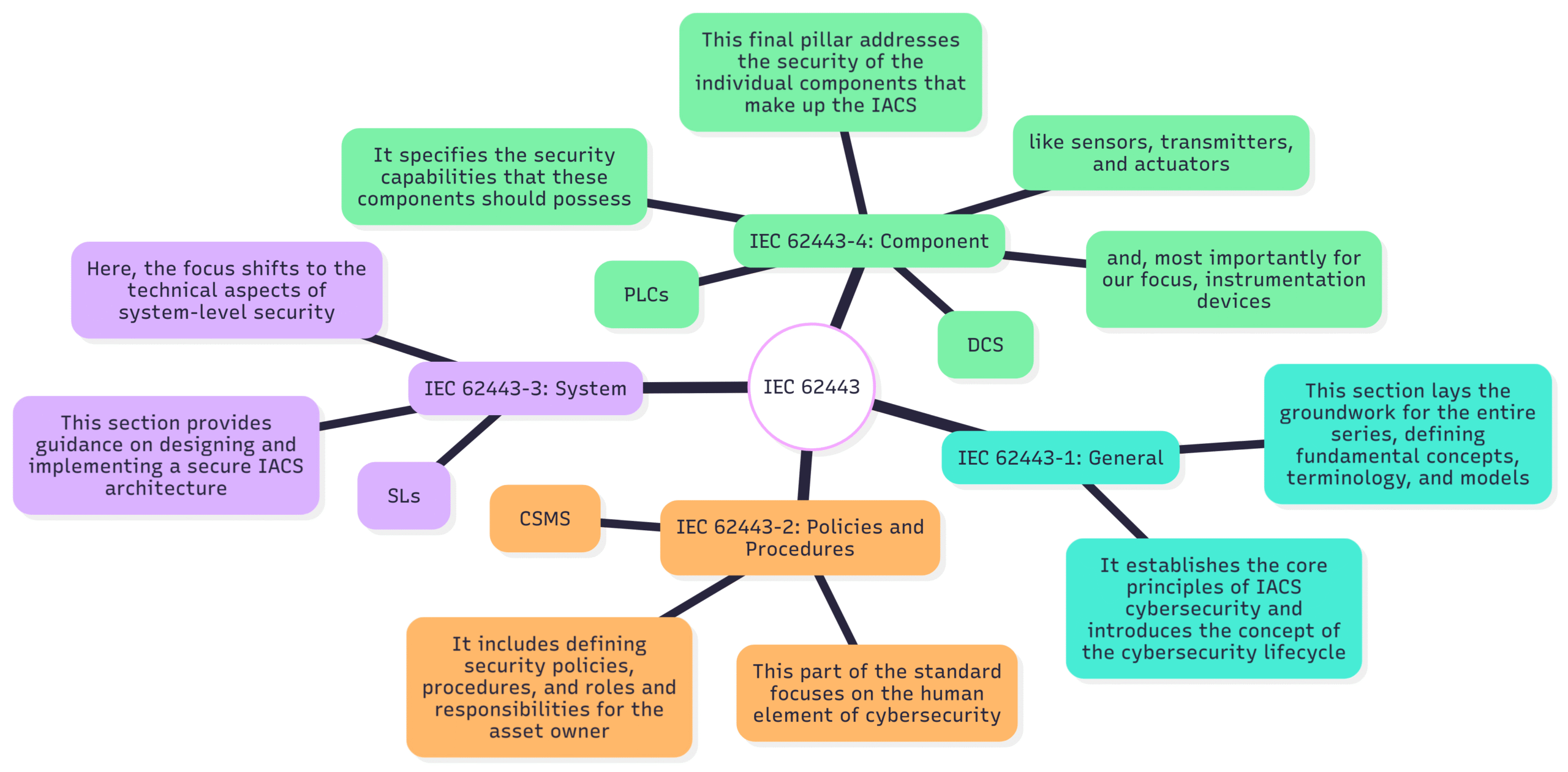
IEC 62443-1: General: This section lays the groundwork for the entire series, defining fundamental concepts, terminology, and models. It establishes the core principles of IACS cybersecurity and introduces the concept of the cybersecurity lifecycle.
IEC 62443-2: Policies and Procedures: This part of the standard focuses on the human element of cybersecurity. It outlines the requirements for establishing, implementing, and maintaining a comprehensive Cybersecurity Management System (CSMS). This includes defining security policies, procedures, and roles and responsibilities for the asset owner.
IEC 62443-3: System: Here, the focus shifts to the technical aspects of system-level security. This section provides guidance on designing and implementing a secure IACS architecture, including the critical concepts of zones and conduits and the assignment of security levels (SLs).
IEC 62443-4: Component: This final pillar addresses the security of the individual components that make up the IACS, such as programmable logic controllers (PLCs), distributed control systems (DCS), and, most importantly for our focus, instrumentation devices like sensors, transmitters, and actuators. It specifies the security capabilities that these components should possess.
By addressing these four key areas, the IEC 62443 framework provides a comprehensive and defense-in-depth approach to securing industrial environments.
The Heart of the Matter: Risk Assessment in Instrumentation Projects
Before you can effectively secure your instrumentation systems, you must first understand the risks they face. The IEC 62443 series places a strong emphasis on a risk-based approach to cybersecurity. This involves a systematic process of identifying, analyzing, and evaluating potential threats and vulnerabilities to your IACS.
For instrumentation projects, the risk assessment process needs to be particularly granular. Consider the potential impact of a compromised sensor providing false readings to a control system, or a smart valve actuator being manipulated to disrupt a critical process. The consequences can range from minor production inefficiencies to major safety incidents.
The risk assessment process, as outlined in IEC 62443-3-2, typically involves the following steps:
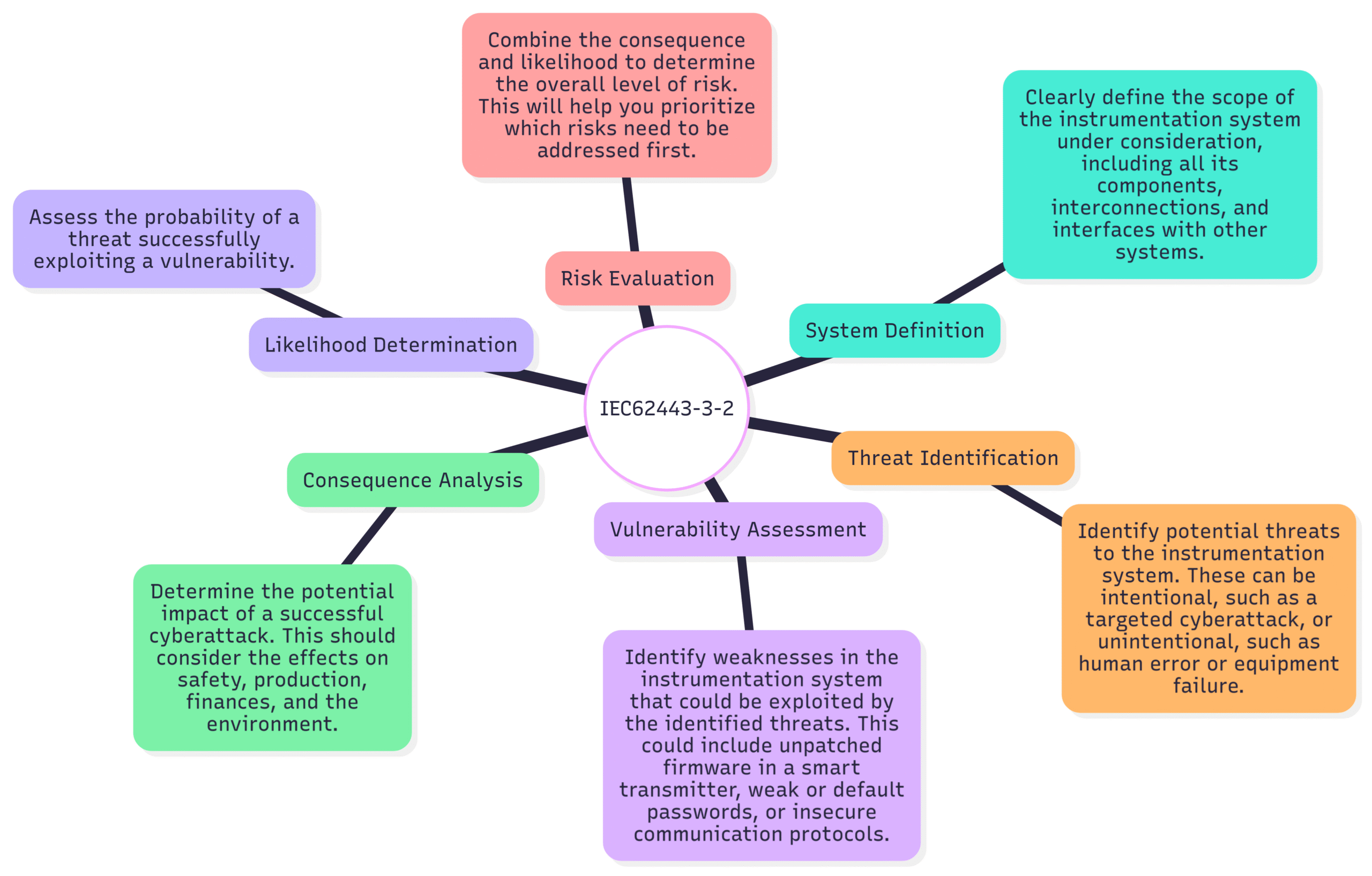
System Definition: Clearly define the scope of the instrumentation system under consideration, including all its components, interconnections, and interfaces with other systems.
Threat Identification: Identify potential threats to the instrumentation system. These can be intentional, such as a targeted cyberattack, or unintentional, such as human error or equipment failure.
Vulnerability Assessment: Identify weaknesses in the instrumentation system that could be exploited by the identified threats. This could include unpatched firmware in a smart transmitter, weak or default passwords, or insecure communication protocols.
Consequence Analysis: Determine the potential impact of a successful cyberattack. This should consider the effects on safety, production, finances, and the environment.
Likelihood Determination: Assess the probability of a threat successfully exploiting a vulnerability.
Risk Evaluation: Combine the consequence and likelihood to determine the overall level of risk. This will help you prioritize which risks need to be addressed first.
By conducting a thorough risk assessment, you can make informed decisions about the security measures that are necessary to protect your instrumentation projects, ensuring that your resources are allocated effectively.
A Blueprint for Security: Zones and Conduits in Instrumentation Architecture
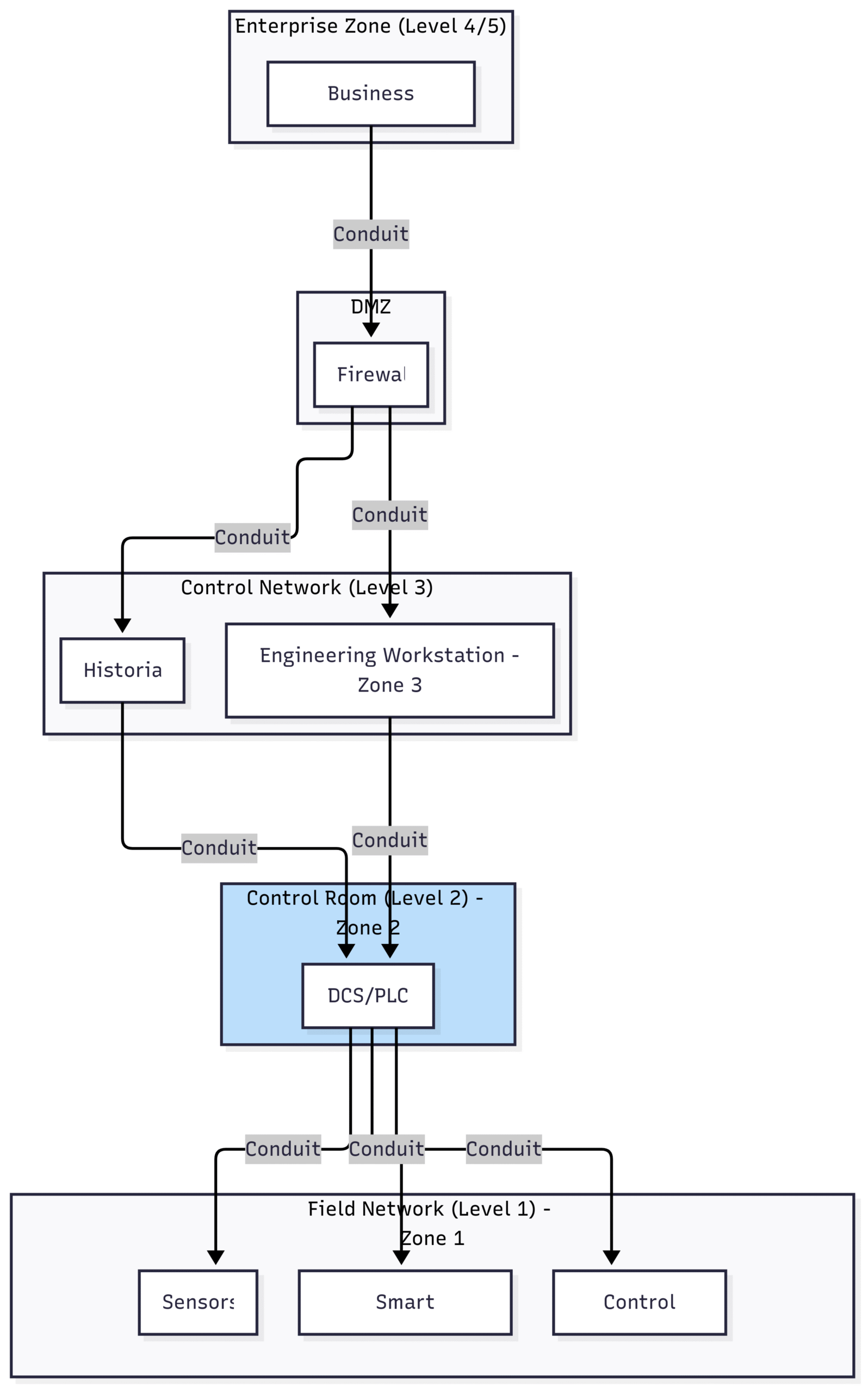
One of the most powerful concepts introduced by IEC 62443 is the use of zones and conduits to segment and secure an IACS. This approach is fundamental to creating a defense-in-depth strategy and is particularly relevant for the diverse and distributed nature of instrumentation systems.
Zones are logical groupings of assets that share common security requirements. In an instrumentation project, a zone could be defined by a specific process area, a particular control loop, or a set of instruments with the same criticality. For example, all the instruments associated with a critical safety shutdown system would likely be placed in a dedicated, highly secured zone.
Conduits are the communication channels that connect different zones. These are the pathways through which data flows between instruments, controllers, and other systems. By defining and securing these conduits, you can control the flow of information and prevent unauthorized access between zones.
Applying Zones and Conduits to an Instrumentation Project: A Practical Example
Imagine a typical process control system in a chemical plant. We can use the concept of zones and conduits to create a secure architecture for its instrumentation:
Zone 1: Field Instruments: This zone would encompass all the sensors, transmitters, and actuators in the field. These devices are often physically exposed and may use legacy communication protocols, making them a primary target for attackers. Security controls in this zone would focus on physical security, device hardening, and the use of secure communication protocols where possible.
Zone 2: Control Room: This zone would contain the distributed control system (DCS) or programmable logic controllers (PLCs) that receive data from the field instruments and send control commands. This is a critical zone that requires strong access controls, network segmentation, and continuous monitoring.
Zone 3: Engineering Workstations: This zone would include the computers used by engineers to configure and maintain the instrumentation and control systems. Access to this zone should be strictly controlled and monitored to prevent the introduction of malware or unauthorized changes.
Conduits: The communication links between these zones would be defined as conduits. For example, the fieldbus network connecting the field instruments to the control system would be a conduit. Security measures for this conduit would include firewalls, intrusion detection systems, and encryption to protect the data in transit.
This segmentation approach ensures that a security breach in one zone does not automatically compromise the entire system.
Block Diagram: IEC 62443 Zones and Conduits in an Instrumentation Project
A simplified block diagram illustrating the application of zones and conduits in an instrumentation project, based on the Purdue Model for Control Hierarchy.
Defining the Target: Security Levels (SLs) in IEC 62443
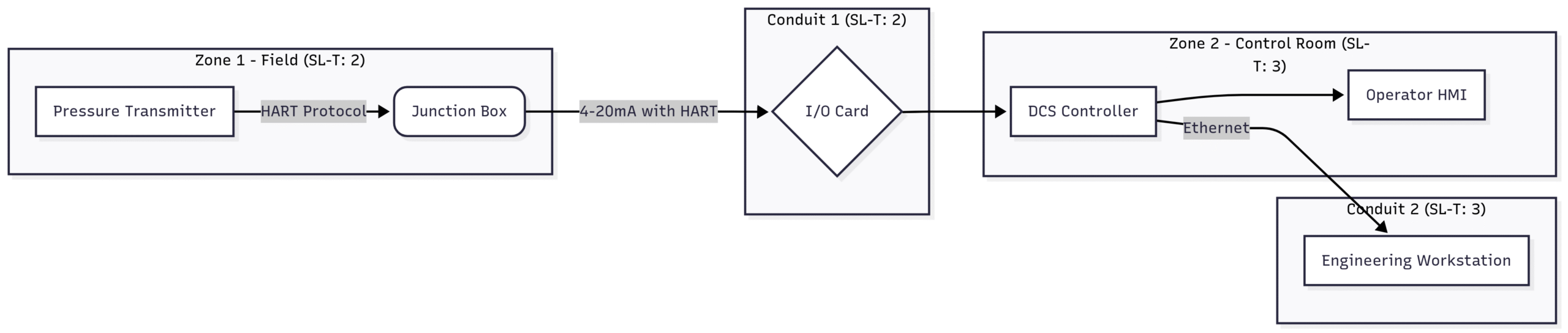
Not all instrumentation systems require the same level of security. A sensor monitoring a non-critical process parameter will have a different security requirement than a safety instrumented system (SIS) designed to prevent a catastrophic event. IEC 62443 addresses this by introducing the concept of Security Levels (SLs).
Security Levels provide a standardized way to define the required security capabilities for a particular zone or conduit. There are four security levels defined in the standard:
SL 1: Protection against casual or coincidental violation. This level provides basic security measures to protect against unintentional misuse.
SL 2: Protection against intentional violation by simple means. This level requires more robust security controls to defend against attackers with limited resources and skills.
SL 3: Protection against intentional violation by sophisticated means. This level is designed to protect against skilled attackers with significant resources.
SL 4: Protection against intentional violation by sophisticated means with extended resources. This is the highest level of security, intended to defend against nation-state-sponsored attacks.
Determining the Target Security Level (SL-T)
The target security level for a particular zone or conduit is determined through the risk assessment process. The higher the risk associated with a particular part of the system, the higher the required SL-T. For example, the critical safety system mentioned earlier would likely have an SL-T of 3 or 4, while a less critical monitoring system might only require an SL-T of 1 or 2.
Once the SL-T has been determined, the next step is to select and implement security controls that will achieve that level of security. IEC 62443-3-3 provides a detailed list of system security requirements and their mapping to the different security levels.
It is also important to consider the achieved security level (SL-A), which is the actual level of security that has been implemented and verified. The goal is to ensure that the SL-A is equal to or greater than the SL-T for all parts of the system.
Block Diagram: Security Levels in an Instrumentation Loop
This block diagram illustrates how different security levels can be applied to various components and communication paths within a single instrumentation loop.
Practical Implementation: Policies and Procedures for Your Instrumentation Projects
Having a deep understanding of the IEC 62443 framework is essential, but the real challenge lies in its practical implementation. This requires the development and enforcement of clear policies and procedures that govern all aspects of cybersecurity for your instrumentation projects.
Here are some key policies and procedures that you should consider implementing:
Cybersecurity Management System (CSMS): As per IEC 62443-2-1, establish a formal CSMS that defines your organization’s commitment to cybersecurity. This should include a clear security policy, defined roles and responsibilities, and a process for continuous improvement.
Secure Development Lifecycle (SDL) for Instrumentation Components: If you are a product supplier, you need to implement a secure development lifecycle for your instrumentation devices, as outlined in IEC 62443-4-1. This ensures that security is built into your products from the ground up, rather than being bolted on as an afterthought.
Secure System Integration: System integrators play a crucial role in ensuring that instrumentation projects are implemented securely. IEC 62443-2-4 provides requirements for IACS service providers, including the need for secure engineering practices, configuration management, and testing.
Patch Management: Develop a robust patch management program to ensure that all your instrumentation devices and control systems are kept up-to-date with the latest security patches. This is a critical defense against known vulnerabilities.
Access Control: Implement strong access control measures to restrict access to your instrumentation systems to authorized personnel only. This includes both physical access to devices and logical access to networks and applications.
Incident Response Plan: Despite your best efforts, security incidents can still occur. It is crucial to have a well-defined incident response plan in place to ensure that you can detect, respond to, and recover from security breaches in a timely and effective manner.
Security Awareness and Training: The human element is often the weakest link in the cybersecurity chain. It is essential to provide regular security awareness and training to all personnel who interact with your instrumentation systems.
By implementing these policies and procedures, you can create a strong and sustainable cybersecurity program that will protect your instrumentation projects from the ever-evolving threat landscape.
Conclusion: Building a Secure Future for Industrial Automation
The IEC 62443 standards provide a comprehensive and internationally recognized framework for securing industrial automation and control systems. For organizations involved in instrumentation projects, embracing these standards is not just a matter of compliance; it is a fundamental requirement for ensuring the safety, reliability, and resilience of their operations.
By adopting a risk-based approach, implementing the concepts of zones and conduits, and defining appropriate security levels, you can build a robust defense-in-depth strategy that will protect your critical instrumentation assets. Furthermore, by establishing clear policies and procedures and fostering a culture of security awareness, you can ensure that your cybersecurity program is both effective and sustainable.
The journey to full IEC 62443 compliance may seem daunting, but it is a journey worth taking. By investing in the security of your instrumentation projects today, you are not only protecting your business from current threats but also building a secure foundation for the future of industrial automation.
Ready to take the next step in securing your instrumentation projects? Contact our team of certified cybersecurity experts to learn more about how we can help you implement the IEC 62443 standards and build a resilient cybersecurity posture for your organization.