
Cyber Security: All About Firewall Requirements and Design
In the vast, interconnected digital landscape, your network is your fortress. At the gate of this fortress stands a critical sentinel: the firewall. For decades, firewalls have been the bedrock of network security, the first line of defense against a relentless barrage of cyber threats. But simply having a firewall isn’t enough. An improperly configured or poorly designed firewall is like a gate left unlocked—it provides a false sense of security while leaving you vulnerable.
To build a truly resilient cybersecurity posture, you need a deep understanding of firewall requirements and a meticulous approach to its design. This comprehensive guide will walk you through everything you need to know, from foundational concepts to advanced architectural principles. We’ll explore how to define what you need, design a robust solution, and implement a firewall that genuinely protects your digital assets. 🛡️
What is a Firewall, Really?
At its core, a firewall is a network security device—either hardware or software-based—that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Think of it as a digital bouncer for your network. It inspects every piece of data (called a packet) trying to enter or leave and decides whether to allow it or block it based on a set of rules, known as the firewall policy.
The primary goal is to establish a barrier between your trusted internal network and untrusted external networks, such as the internet, preventing unauthorized access while permitting legitimate communications.
Core Functions
A firewall’s functionality has evolved, but its core responsibilities include:
Packet Filtering: The most basic function. It examines the header of each packet, which contains information like source and destination IP addresses, port numbers, and the protocol being used (e.g., TCP, UDP, ICMP). It then decides to allow or deny the packet based on these simple criteria.
Stateful Inspection: A more intelligent approach. A stateful firewall tracks the state of active connections. It knows which packets belong to a legitimate, ongoing conversation. If an incoming packet doesn’t match an existing connection initiated from inside the network, it’s dropped. This prevents many types of attacks that exploit connection protocols.
Proxy Service (Application Gateway): This is the most secure, but also the most resource-intensive, method. An application-level gateway, or proxy firewall, acts as an intermediary for specific applications. It breaks the connection between the client and the server, establishing two separate connections—one from the client to the firewall and one from the firewall to the server. This allows it to inspect the actual content of the traffic, providing granular control and deep-level security.
Types of Firewalls: Choosing Your Guardian
Firewalls are not a one-size-fits-all solution. They come in various forms, each offering different levels of protection, performance, and complexity. Understanding these types is the first step in selecting the right one for your needs.
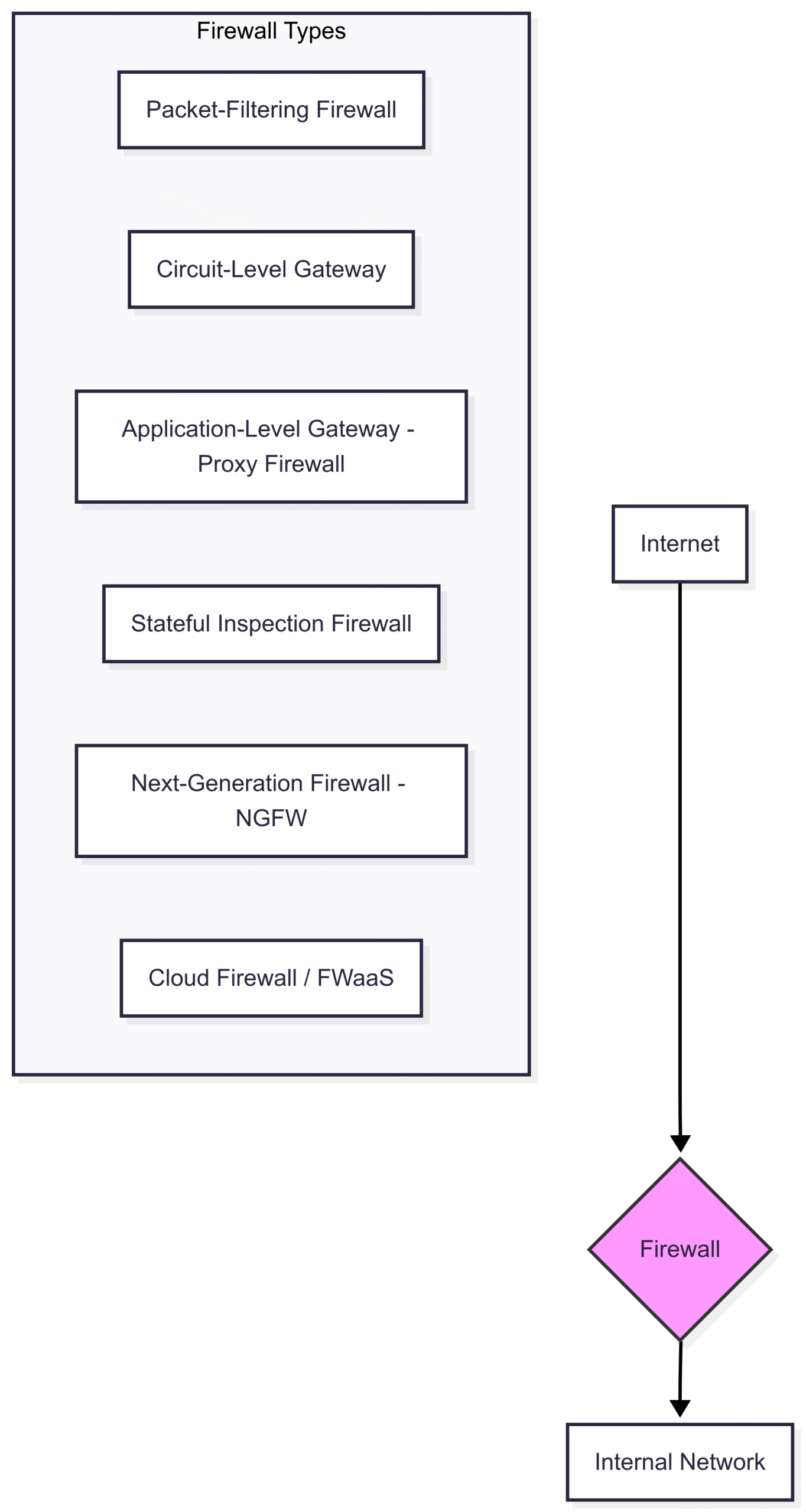
Packet-Filtering Firewalls: The first generation. They operate at the network layer (Layer 3) of the OSI model. They are fast and efficient but lack context, as they don’t inspect packet content or track connection states.
Circuit-Level Gateways: These operate at the session layer (Layer 5). They monitor TCP handshakes to ensure that a requested session is legitimate. Once the session is established, they don’t inspect the traffic content, making them relatively fast.
Application-Level Gateways (Proxy Firewalls): Operating at the application layer (Layer 7), these are the security purists. They can filter traffic for specific services or applications (e.g., HTTP, FTP), inspecting the payload of the packets. This provides robust security but can introduce latency.
Stateful Inspection Firewalls: The most common type of firewall today. They combine the speed of packet filtering with the security of tracking connection states, offering a balanced approach to performance and protection.
Next-Generation Firewalls (NGFW): This is the modern evolution. An NGFW combines traditional firewall functionalities with a suite of advanced security services. Key features include:
Deep Packet Inspection (DPI): Goes beyond headers to inspect the actual data content.
Intrusion Prevention Systems (IPS): Actively detects and blocks threats based on signatures and anomalies.
Application Awareness and Control: Identifies and controls traffic based on the specific application (e.g., block Facebook but allow Salesforce), regardless of the port being used.
Threat Intelligence Integration: Uses real-time feeds to block known malicious IP addresses, domains, and malware.
Cloud Firewalls (Firewall-as-a-Service – FWaaS): A cloud-hosted solution that delivers firewall capabilities as a service. This is ideal for protecting cloud infrastructure and distributed workforces, offering scalability and simplified management.
Step 1: Defining Your Firewall Requirements
Before you can design a firewall architecture, you must first understand what you need to protect and what you’re trying to achieve. This requirements-gathering phase is the most critical part of the process. Rushing this step often leads to a solution that is either inadequate or overly complex and expensive.
Business Needs Analysis
Security should enable the business, not hinder it. Start by asking fundamental questions:
What are the critical assets we need to protect? (e.g., customer data, intellectual property, financial records)
Who needs access to these assets, and from where? (e.g., internal employees, remote workers, third-party vendors)
What are the business-critical applications and services? What are their availability requirements?
What is the business’s tolerance for risk?
What is the budget for both initial acquisition and ongoing operational costs?
Threat Modeling
You can’t defend against threats you don’t understand. Threat modeling is a structured process for identifying potential threats and vulnerabilities.
Identify Attackers: Who might attack you? (e.g., script kiddies, organized crime, state-sponsored actors, malicious insiders)
Identify Attack Vectors: How might they attack you? (e.g., malware, phishing, Denial-of-Service (DoS) attacks, SQL injection)
Assess Vulnerabilities: What are your weak points? (e.g., unpatched systems, weak access controls, lack of user awareness)
Performance and Scalability
A firewall that can’t keep up with your network traffic is a bottleneck that can cripple business operations. Key performance metrics include:
Throughput: The amount of data that can pass through the firewall, measured in gigabits per second (Gbps). You need to consider raw firewall throughput, as well as throughput with advanced features like IPS and DPI enabled (often called “threat protection throughput”).
Connections Per Second (CPS): The number of new connections the firewall can establish per second.
Concurrent Connections: The total number of active connections the firewall can handle at once.
Latency: The delay the firewall introduces to network traffic.
Scalability: Will the solution grow with your business? Consider future increases in bandwidth usage, number of users, and encrypted traffic (SSL/TLS).
Compliance and Regulatory Needs
Many industries are subject to strict regulations that dictate security controls. Your firewall design must meet these requirements.
PCI DSS (Payment Card Industry Data Security Standard): Requires a firewall to protect cardholder data.
HIPAA (Health Insurance Portability and Accountability Act): Mandates the protection of patient health information.
GDPR (General Data Protection Regulation): Requires strong security measures to protect the data of EU citizens.
SOX (Sarbanes-Oxley Act): Imposes requirements for data integrity and access controls in financial reporting.
Management and Reporting
A firewall is only as good as its management.
Ease of Use: How intuitive is the management interface? A complex interface can lead to misconfigurations.
Logging and Auditing: The firewall must generate detailed, easy-to-understand logs. This is crucial for troubleshooting, incident response, and compliance audits.
Reporting and Analytics: Can the firewall provide dashboards and reports that give you clear insights into network traffic, security events, and policy effectiveness?
Step 2: Firewall Design Principles and Architecture
With your requirements clearly defined, you can now move on to the design phase. A well-thought-out firewall architecture is built on proven security principles that create a robust, multi-layered defense.
Principle 1: Defense-in-Depth
Relying on a single line of defense is a recipe for disaster. Defense-in-depth is a strategy that involves layering multiple security controls. If one layer fails, another is there to stop the attack. Firewalls are a key part of this strategy, often used at different points in the network.
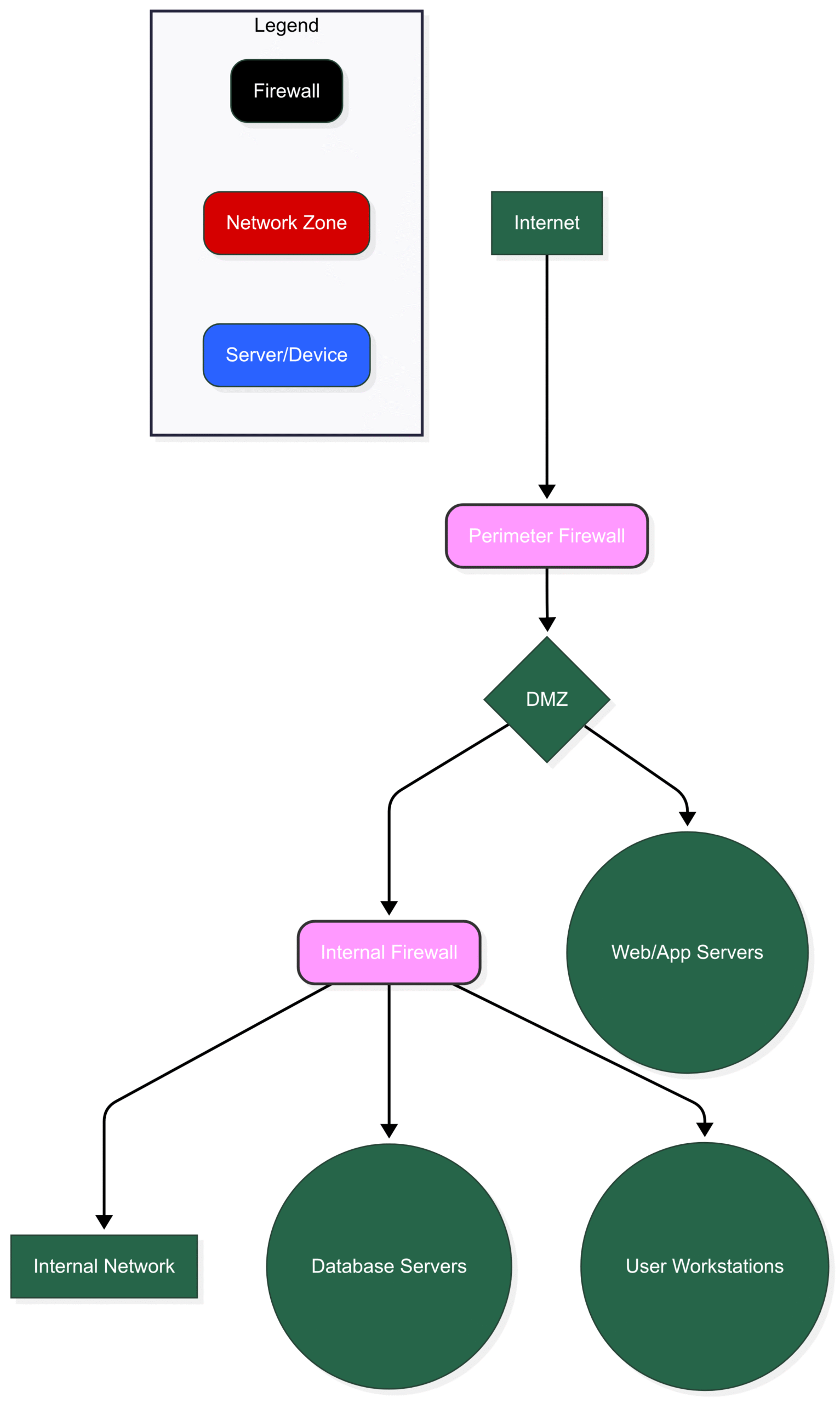
In this model, the Perimeter Firewall protects the entire network from the external world, while the Internal Firewall adds another layer of protection, segmenting critical assets like database servers from the rest of the internal network.
Principle 2: The Principle of Least Privilege
This is the golden rule of security. By default, deny everything and only permit the specific traffic that is explicitly required for business functions. A firewall policy should be built on a deny-all rule that is placed at the very end of the rulebase. Every rule you create above it should be a specific exception to this default.
A simple rule might look like this: Allow [Source IP] to access [Destination IP] on [Port/Service]. Anything not explicitly allowed is blocked.
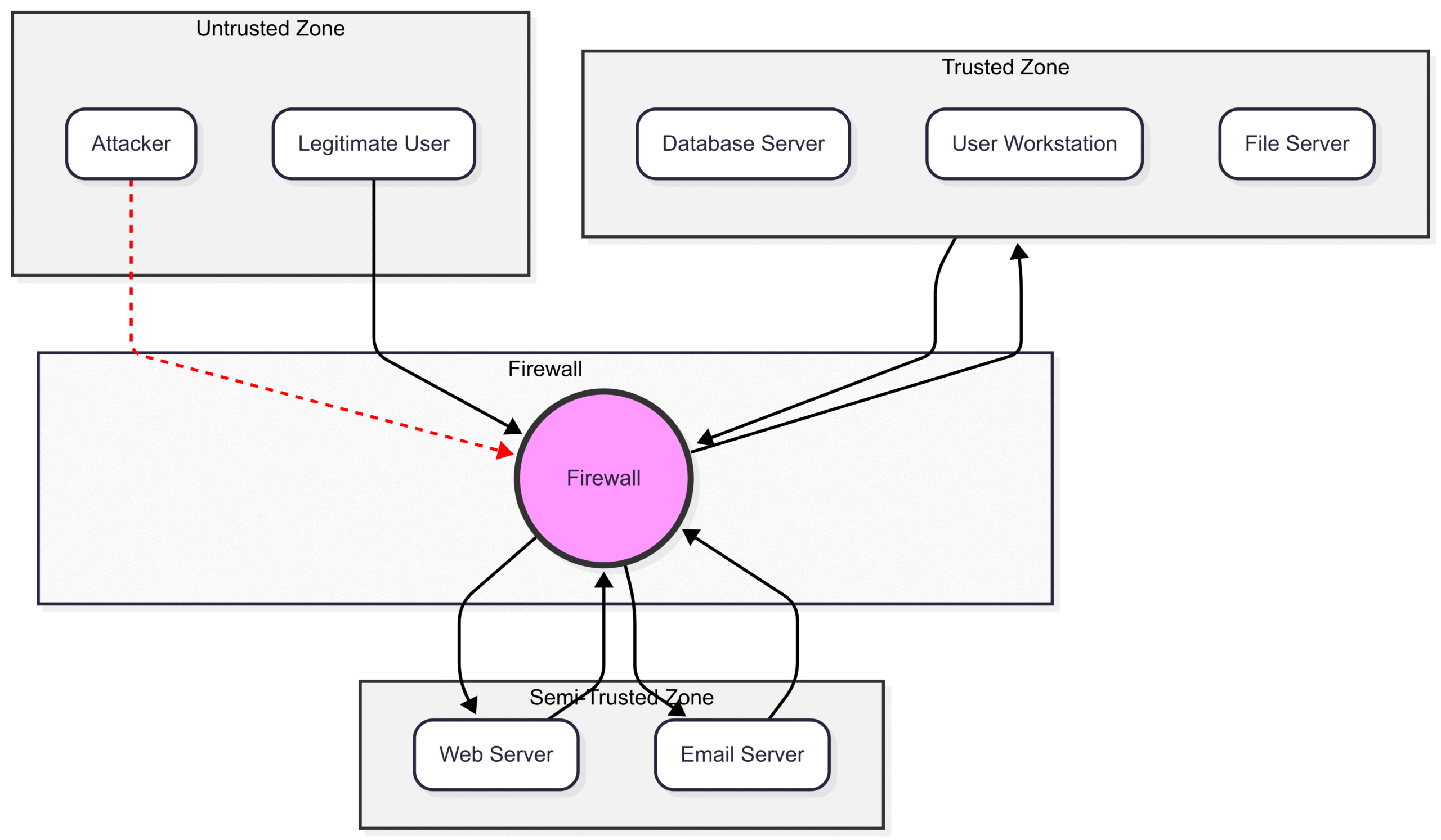
Principle 3: Network Segmentation
Flat networks, where every device can communicate with every other device, are a major security risk. If one machine is compromised, the attacker can move laterally across the entire network. Network segmentation is the practice of dividing a network into smaller, isolated zones or segments using a firewall. This contains breaches and limits the “blast radius” of an attack.
A common and highly effective segmentation design involves creating a Demilitarized Zone (DMZ).
How it works:
Internet (Untrusted): The outside world. No trust here.
DMZ (Demilitarized Zone): A buffer zone that houses servers that need to be accessible from the internet, such as web servers and email servers. If a server in the DMZ is compromised, the attacker is still firewalled off from the critical internal network.
Internal Network (Trusted): The most secure zone, containing critical assets like database servers, file servers, and employee workstations.
Key Traffic Flow Rules:
Internet users can access servers in the DMZ (e.g., on ports 80/443 for a web server).
Traffic from the Internet is never allowed to initiate connections directly to the Internal Network.
Servers in the DMZ can initiate limited, specific connections to the Internal Network (e.g., the web server needs to query the database server).
The Internal Network can generally initiate connections to both the DMZ and the Internet.
Principle 4: High Availability (HA) and Redundancy
A firewall is a single point of failure. If it goes down, your entire network loses its protection and potentially its connectivity. A High Availability (HA) design ensures continuous operation by using a redundant pair of firewalls.
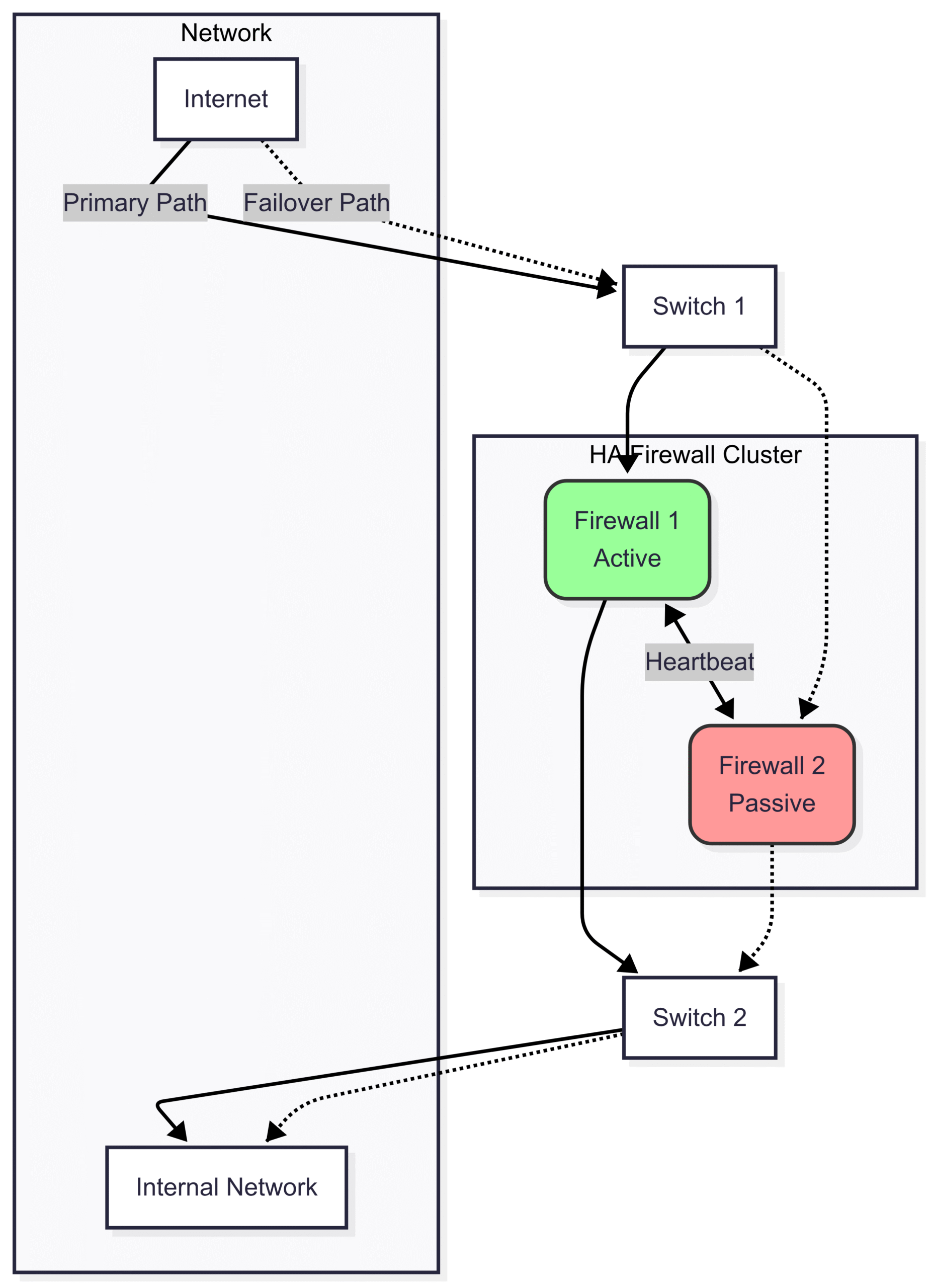
How it works:
Two identical firewalls are configured as a cluster. One is Active, handling all traffic, while the other is Passive (or Standby).
The two firewalls are connected by a “heartbeat” link. The Active firewall constantly sends status signals to the Passive one.
If the Passive firewall stops receiving the heartbeat signal (indicating the Active one has failed), it automatically takes over all firewall duties. This failover process is typically seamless and happens within seconds, ensuring minimal disruption.
Step 3: The Design and Implementation Process
Translating principles into practice requires a structured workflow.
1. Revisit Requirements and Select a Vendor
Armed with your detailed requirements, you can now evaluate vendors and specific firewall models. Create a scorecard to compare solutions based on:
Performance metrics (throughput, CPS).
NGFW feature set (IPS, Application Control, etc.).
Management interface and logging capabilities.
Support for High Availability and scalability.
Third-party reviews and lab tests (e.g., Gartner, NSS Labs).
Total Cost of Ownership (TCO), including hardware, subscriptions, and support.
2. Create the Architectural Design
This is where you diagram your network. Use the principles of segmentation and defense-in-depth to map out your network zones (Internal, DMZ, Guest Wi-Fi, etc.) and the placement of your firewall(s). Your design should show traffic flows and how the firewall will enforce boundaries between these zones.
3. Develop the Firewall Policy and Rulebase
This is the most time-consuming and critical configuration step.
Start with a Default Deny: Your last rule should always be
ANY ANY ANY DENY LOG.Be Specific: Avoid using “ANY” in your source, destination, or service fields whenever possible. The more specific a rule, the more secure it is.
Rule Order Matters: Firewalls process rules from top to bottom. The first rule that matches the traffic is applied. Place more specific rules at the top and more general rules towards the bottom.
Stealth Rule: Implement a rule near the top that drops any traffic directed at the firewall itself from untrusted networks. This prevents attackers from probing the firewall directly.
Clean and Document: Regularly review your rulebase to remove old or unused rules. Add comments to every rule explaining its business purpose. This is invaluable for auditing and troubleshooting.
4. Implement and Test
Deploy the firewall in a controlled environment first.
Lab Testing: If possible, build a small-scale replica of your production network to test the firewall configuration and policy.
Phased Rollout: Introduce the firewall in a non-disruptive way, perhaps in transparent or “monitor-only” mode first. This allows you to see what traffic the firewall would block without actually blocking it, helping you refine your policy.
Validation: Once deployed, test that legitimate traffic flows as expected and that forbidden traffic is blocked. Use tools like
nmapfor port scanning and vulnerability scanners to test the firewall’s effectiveness from an attacker’s perspective.
5. Audit and Optimize
A firewall is not a “set it and forget it” device. Security is a continuous process.
Regular Audits: Periodically review the firewall configuration, rulebase, and logs. This should be done at least quarterly.
Performance Monitoring: Keep an eye on CPU and memory utilization. High usage can indicate that the firewall is undersized or that it’s under attack (e.g., a DoS attack).
Stay Updated: Keep the firewall’s firmware and software patched. Update threat intelligence, IPS signatures, and application definitions regularly.
Conclusion: The Cornerstone of Your Cyber Defense
In the complex world of cybersecurity, the firewall remains an indispensable tool. It is the primary enforcer of your network security policy and the gatekeeper for all your digital assets. However, its effectiveness hinges entirely on a thoughtful and meticulous approach to its requirements and design.
By thoroughly analyzing your business needs, understanding the threat landscape, and applying proven design principles like defense-in-depth, network segmentation, and least privilege, you can build a firewall architecture that is not just a device, but a powerful and resilient defense system. Investing the time and effort in proper design and ongoing management will pay dividends, transforming your firewall from a simple network component into the true cornerstone of your cybersecurity strategy. ✨
