
Cyber Security: A Deep Dive into Gateway Requirements and Design
In the sprawling, interconnected digital landscape of today, your network’s perimeter is no longer a simple line in the sand. It’s a bustling, dynamic frontier, constantly besieged by a torrent of data, applications, and users—both friendly and malicious. Guarding this critical frontier is the cybersecurity gateway, the unsung hero of network defense. It’s your digital gatekeeper, your first line of defense, and the central checkpoint through which all traffic must pass.
But what makes a gateway truly effective? It’s not just about deploying a firewall and hoping for the best. A robust security posture demands a meticulously planned gateway architecture, built on a solid foundation of well-defined requirements and intelligent design. This comprehensive guide will explore everything you need to know about cybersecurity gateway requirements and design, empowering you to build a resilient and secure network fortress. We’ll break down the core components, explore modern architectural models, and provide actionable best practices.
What is a Cybersecurity Gateway? The First Line of Defense 🛡️
At its core, a security gateway is a network point that acts as an entrance to another network. It’s a choke point where you can enforce security policies, inspect traffic, and block threats before they can infiltrate your internal systems. Think of it as the highly-secured main entrance to a critical facility. Every person and package (data packet) must pass through a rigorous security checkpoint that scans for threats, verifies credentials, and ensures only authorized entities gain entry.
In the early days of the internet, this role was primarily filled by a firewall. A firewall’s job was simple: to allow or deny traffic based on a set of rules, typically looking at IP addresses and port numbers. While essential, this is no longer sufficient. Modern threats are sophisticated, often hiding within legitimate-looking traffic and applications.
This evolution gave rise to next-generation gateways, often called Next-Generation Firewalls (NGFWs) or Unified Threat Management (UTM) systems. These advanced gateways go far beyond simple port/protocol inspection. They provide a suite of integrated security functions, including:
Deep Packet Inspection (DPI): Looking inside the data packets to identify the application, user, and potential threats.
Intrusion Prevention Systems (IPS): Proactively identifying and blocking known attack patterns and exploits.
Antivirus and Anti-Malware: Scanning traffic for malicious code.
Application Control: Defining which specific applications (e.g., Facebook, Dropbox) are allowed or blocked, regardless of the port they use.
Web Filtering: Blocking access to malicious or inappropriate websites.
Essentially, the modern security gateway is the central nervous system of your network security, providing the visibility and control needed to defend against a complex and ever-changing threat landscape.
Core Requirements for a Secure Gateway: The Building Blocks 🧱
Before you can design an effective gateway architecture, you must first define your requirements. These requirements are the fundamental capabilities your gateway must possess to protect your organization adequately. Rushing this step is like building a house without a blueprint—the result will be unstable and insecure.
Performance and Scalability
A security gateway is an inline device, meaning all network traffic must pass through it. This makes performance a non-negotiable requirement. A slow gateway becomes a network bottleneck, frustrating users and impeding business operations.
Throughput: This is the primary metric. You need to calculate the maximum amount of traffic your gateway can handle. Critically, you must consider the “threat protection throughput,” not just the basic firewall throughput. Enabling advanced security features like IPS and DPI consumes significant processing power and can reduce a gateway’s stated throughput by 50-80% or more. Always look for real-world performance metrics with all security features turned on.
Connection Capacity: How many concurrent sessions can the gateway handle? This is crucial for environments with many users or devices connecting simultaneously.
Scalability: Your business will grow, and so will your network traffic. Your chosen gateway solution should be able to scale to meet future demands. This could mean having the ability to upgrade hardware, add more processing power, or cluster multiple gateways together for increased capacity and redundancy.
Threat Prevention and Detection
The primary function of a security gateway is to stop attacks. Its threat prevention capabilities are its most important feature set.
Stateful Firewall: The foundation of any gateway. It tracks the state of active connections and makes decisions based on the context of the traffic, not just individual packets.
Intrusion Prevention System (IPS): An IPS actively scans network traffic for known vulnerability exploits and attack signatures. Upon detection, it can automatically block the malicious traffic. A good IPS is backed by a world-class threat intelligence feed that is updated continuously.
Sandboxing: Advanced threats, especially zero-day malware, are designed to evade signature-based detection. A sandbox is a secure, isolated virtual environment where the gateway can “detonate” suspicious files to observe their behavior. If the file attempts to perform malicious actions (e.g., encrypting files, contacting a command-and-control server), it is blocked.
Antivirus/Anti-Malware: This engine scans all types of traffic (web, email, file transfers) for known viruses, worms, trojans, and other malware.
Threat Intelligence Integration: The gateway should be able to consume real-time threat intelligence feeds. This allows it to block traffic to and from known malicious IP addresses, domains, and URLs associated with botnets, phishing campaigns, and other threats.
Access Control and Authentication
You need to control not only what comes into your network but also who. Robust access control ensures that only legitimate users and devices can connect to your resources.
Virtual Private Network (VPN): A gateway must provide secure remote access for employees, partners, and contractors. This includes both IPsec VPNs for site-to-site connections and SSL VPNs for individual remote users, ensuring all data transmitted over the public internet is encrypted.
Identity Awareness: Modern gateways integrate with directory services like Active Directory or Azure AD. This allows you to create security policies based on user identity or group membership, not just IP addresses. For example, you can create a rule that allows the engineering team to access specific servers while blocking the marketing team.
Multi-Factor Authentication (MFA): For high-security access, especially for remote users and administrators, the gateway should enforce MFA. This requires users to provide a second form of verification (like a code from a mobile app) in addition to their password.
Content Filtering and Data Loss Prevention (DLP)
A gateway’s job isn’t just about stopping threats from coming in; it’s also about preventing sensitive data from going out.
URL/Web Filtering: This allows you to control which websites your users can access, based on categories (e.g., gambling, social media, malware) and custom blacklists/whitelists. This protects against drive-by downloads from malicious sites and enforces acceptable use policies.
Application Control: With thousands of web-based applications available, you need granular control. Application control identifies and controls application traffic, even if it’s trying to evade detection by hopping ports or using encryption. You can block high-risk applications like peer-to-peer file sharing or throttle bandwidth for non-essential ones.
Data Loss Prevention (DLP): An integrated DLP function inspects outbound traffic (email, web uploads) for sensitive data patterns, such as credit card numbers, social security numbers, or specific keywords related to intellectual property. If a match is found, the gateway can block the transmission and alert an administrator, preventing costly data breaches.
Logging, Monitoring, and Reporting
You can’t protect what you can’t see. Comprehensive visibility is a critical requirement for effective security management, incident response, and compliance.
Centralized Logging: The gateway must generate detailed logs for all traffic, security events, and administrative changes. These logs should be sent to a centralized Security Information and Event Management (SIEM) system for correlation and analysis.
Real-Time Monitoring: Dashboards should provide a real-time view of network health, security threats, and traffic patterns.
Reporting: The ability to generate comprehensive reports is essential for compliance audits (e.g., PCI DSS, HIPAA) and for communicating security posture to management. Reports should cover threat trends, application usage, user activity, and policy effectiveness.
Designing a Robust Security Gateway Architecture 🏗️
With your requirements defined, you can now move on to the design phase. The right architecture depends on your organization’s size, complexity, risk tolerance, and budget. Let’s explore three common design models.
The Unified Threat Management (UTM) Model
The UTM model is an “all-in-one” approach, consolidating multiple security functions into a single appliance. This is a popular choice for small to medium-sized businesses (SMBs) due to its simplicity and lower initial cost.
Description: A single hardware or virtual appliance is placed at the network edge. It performs the duties of a firewall, IPS, antivirus, web filter, and VPN concentrator.
Pros:
Simplicity: Easier to deploy and manage than multiple separate devices.
Cost-Effective: Lower upfront capital and operational expenditure.
Single Vendor: Simplified support and a single management console.
Cons:
Single Point of Failure: If the UTM appliance fails, the entire network loses connectivity and protection.
Performance Bottlenecks: Enabling all security features simultaneously can overwhelm the processor on lower-end models, creating a significant performance bottleneck.
Jack of all trades, master of none: The individual security functions may not be as robust or effective as best-of-breed, standalone solutions.
Here is a diagram illustrating a simple UTM deployment:

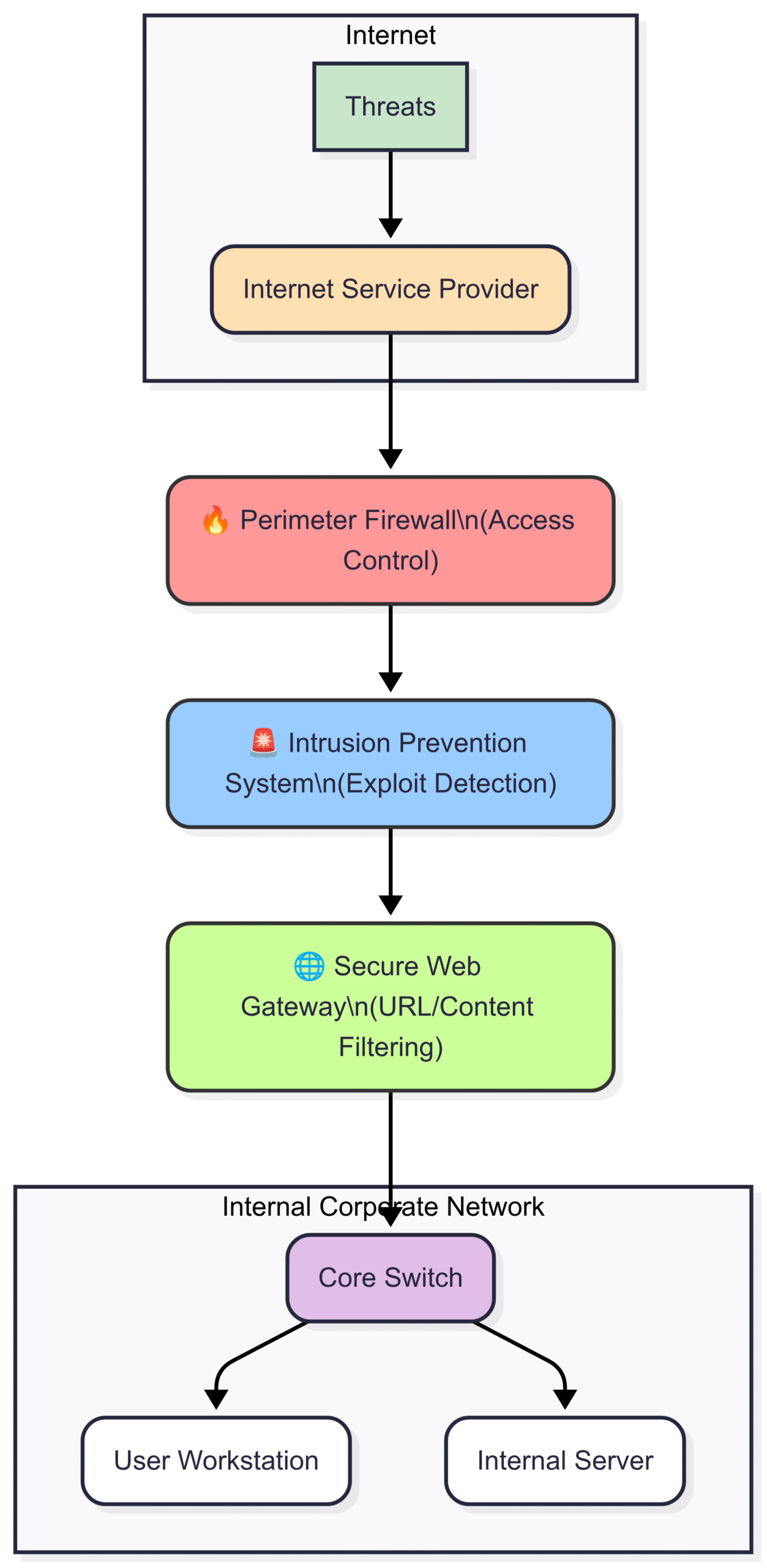
The Layered Security (Defense-in-Depth) Model
For larger enterprises or organizations with a lower risk tolerance, a layered security model is often preferred. This “defense-in-depth” strategy uses multiple, specialized security devices from potentially different vendors, creating a series of security checkpoints.
Description: Traffic entering the network first passes through a high-performance perimeter firewall. It is then passed to a dedicated IPS/IDS device for deeper inspection. From there, it might go to a secure web gateway (SWG) for URL filtering and malware scanning, and a separate email security gateway for spam and phishing protection.
Pros:
Best-of-Breed Security: You can choose the best available product for each specific security function.
High Performance: Dedicated appliances are optimized for their specific task, leading to better overall performance and less of a bottleneck.
Resilience: The failure of one component (e.g., the IPS) does not necessarily bring down the entire network, as the firewall can still provide basic protection.
No Vendor Lock-in: You are not tied to a single vendor’s ecosystem.
Cons:
Complexity: More complex to design, deploy, and manage. Requires expertise in multiple products.
Higher Cost: Higher capital and operational costs due to multiple devices and licenses.
Integration Challenges: Ensuring all the different components work together seamlessly can be difficult. It requires a robust SIEM and SOAR platform for unified visibility and response.
Here is a diagram illustrating a layered security architecture:
The Cloud-Native Gateway Model (SASE/SSE)
The rise of cloud computing and a mobile workforce has rendered the traditional network perimeter obsolete. When your users and applications are everywhere, routing all traffic back to a central gateway is inefficient and slow. The Secure Access Service Edge (SASE) model addresses this by moving the security gateway to the cloud.
Description: SASE converges networking (like SD-WAN) and security functions into a single, cloud-delivered service. Its security component is often called Security Service Edge (SSE). Instead of connecting to a corporate data center, users and branch offices connect to a nearby SASE point of presence (PoP). This PoP enforces all the necessary security policies—firewalling, IPS, web filtering, DLP, and Zero Trust Network Access (ZTNA)—before forwarding the traffic to its destination, whether it’s a SaaS application or the corporate data center.
Pros:
Optimized Performance: Users connect to the nearest cloud PoP, reducing latency for cloud and SaaS applications.
Consistent Security: The same security policies are applied to all users, regardless of their location (office, home, or on the road).
Scalability and Elasticity: The cloud-native platform can scale automatically to handle traffic demands.
Reduced Complexity: Simplifies branch office infrastructure by replacing multiple appliances with a single cloud service.
Enables Zero Trust: ZTNA is a core component, granting access based on verified user and device identity, not network location.
Cons:
Vendor Dependence: You are heavily reliant on your chosen SASE provider’s infrastructure, performance, and security capabilities.
Data Privacy Concerns: Your traffic is being inspected by a third-party cloud provider, which may be a concern for some industries.
Migration Complexity: Transitioning from a traditional appliance-based architecture to a SASE model can be a complex project.
Here is a diagram illustrating a SASE architecture:

Key Considerations and Best Practices for Implementation ✅
Designing the architecture is only half the battle. Successful implementation and ongoing management are what truly determine the effectiveness of your security gateway.
Know Your Traffic: Before you can write effective security policies, you need a baseline of what normal network traffic looks like. Use the gateway’s monitoring tools to understand which applications are used, who the top talkers are, and where your data is going.
Start with a Default Deny Policy: The most secure posture is to block everything by default and only explicitly allow the traffic that is necessary for business operations. This “principle of least privilege” dramatically reduces your attack surface.
Regular Policy Review and Optimization: Security policies are not “set and forget.” They must be reviewed regularly (at least quarterly) to remove old or unused rules, optimize performance, and adapt to new business needs and emerging threats. Unused rules can create security holes and bloat the policy, impacting gateway performance.
Embrace Automation: Modern security gateways and their management platforms offer powerful automation capabilities. Use automation to provision policies, respond to low-level threats, and integrate with other security tools in your ecosystem, such as a SOAR (Security Orchestration, Automation, and Response) platform.
Consistent Patch Management: Your security gateway is a high-value target for attackers. It’s critical to have a strict patch management process to ensure that the gateway’s software and underlying operating system are always up to date with the latest security patches.
Test Your Defenses: Don’t assume your gateway is working perfectly. Regularly conduct penetration testing and use Breach and Attack Simulation (BAS) tools to validate that your security policies are configured correctly and can effectively block real-world attack techniques.
The Gateway to a Secure Future
The cybersecurity gateway is more than just a piece of hardware or software; it’s a strategic control point that is fundamental to the integrity, confidentiality, and availability of your digital assets. By starting with a comprehensive set of requirements—spanning performance, threat prevention, access control, and visibility—you lay the groundwork for a resilient defense.
Choosing the right design—whether it’s a simple UTM, a layered best-of-breed architecture, or a forward-looking cloud-native SASE model—depends on your unique environment. But regardless of the model you choose, the principles remain the same: build for resilience, demand visibility, enforce least privilege, and never stop adapting. In the relentless battle against cyber threats, a well-designed and properly managed gateway is not just a requirement; it’s your gateway to a more secure and confident digital future.
