Cyber Security: A Deep Dive into OPC Server Requirements and Design
In the world of Industrial Control Systems (ICS) and automation, data is the lifeblood that keeps operations running. From manufacturing floors to critical infrastructure, the seamless flow of information between devices, applications, and enterprise systems is paramount. For decades, the Open Platform Communications (OPC) standard has been the backbone of this data exchange. However, as industrial networks become increasingly connected to IT systems and the internet, the cyber security of these communication channels has shifted from an afterthought to a critical business imperative.
An unsecured OPC server is a glaring vulnerability, an open door for malicious actors to disrupt production, compromise safety, steal intellectual property, or even cause physical damage. This comprehensive guide will explore the essential cyber security requirements for OPC servers, delve into secure design principles for both legacy and modern systems, and provide practical, actionable advice for hardening your industrial communication architecture. We’ll cover everything from the fundamentals of OPC to the advanced security features of OPC Unified Architecture (OPC UA), complete with diagrams to illustrate secure network designs.
What is an OPC Server?
At its core, an OPC server is a software application that acts as a standardized translator or intermediary. Industrial hardware, such as Programmable Logic Controllers (PLCs), Distributed Control Systems (DCS), and sensors, often communicate using proprietary protocols. On the other side, software applications like Human-Machine Interfaces (HMIs), Supervisory Control and Data Acquisition (SCADA) systems, and Manufacturing Execution Systems (MES) need to consume this data.
The OPC server bridges this gap. It communicates with the hardware using its native protocol and then exposes that data in a standardized OPC format. This allows any OPC-compliant client application to access the data without needing to understand the specific communication protocol of every single device on the plant floor. This plug-and-play interoperability revolutionized industrial automation.
The Evolution: OPC Classic vs. OPC UA
The OPC standard has evolved significantly over the years, leading to two distinct families: OPC Classic and OPC Unified Architecture (OPC UA). Understanding their differences is fundamental to discussing their security.
OPC Classic: This is the original suite of specifications, including OPC Data Access (DA), Alarms & Events (A&E), and Historical Data Access (HDA). Its primary drawback is its reliance on Microsoft’s Distributed Component Object Model (DCOM) technology. DCOM was designed for trusted, isolated local area networks and is notoriously difficult to configure, troubleshoot, and, most importantly, secure across firewalls and different network domains. It lacks built-in security features like user authentication and encryption, making it a significant liability in modern connected environments.
OPC UA (Unified Architecture): Released in 2008, OPC UA was a ground-up redesign to address the shortcomings of OPC Classic. It’s a platform-independent, service-oriented architecture that moves beyond the confines of DCOM. Crucially, OPC UA was built with security in its DNA. It incorporates a sophisticated, multi-layered security model that includes authentication, authorization, encryption, and data integrity checks right out of the box. It is the modern, secure standard for industrial data exchange.
Why Cyber Security is Critical for OPC Servers
In the age of Industry 4.0 and the Industrial Internet of Things (IIoT), the air gap that once isolated operational technology (OT) from information technology (IT) has all but vanished. This convergence, while unlocking huge efficiencies, exposes sensitive industrial systems to a new world of threats.
An OPC server, as a central data hub, is a high-value target for cyber attacks. The consequences of a compromised OPC server can be catastrophic:
Production Halts: An attacker could send malicious commands to PLCs, stopping machinery and causing costly downtime.
Data Manipulation: False data sent to an HMI or SCADA system could mislead operators into taking incorrect and dangerous actions. Imagine a tank level being reported as normal when it’s about to overflow.
Intellectual Property Theft: Sensitive process data, formulas, and production metrics can be exfiltrated by attackers.
Safety Incidents: Manipulating control parameters can lead to equipment damage, environmental spills, and, in the worst-case scenario, injury or loss of life.
Ransomware Attacks: Industrial systems are increasingly targeted by ransomware, where attackers encrypt systems and halt operations until a ransom is paid.
Securing your OPC infrastructure isn’t just an IT task; it’s a fundamental requirement for safe, reliable, and resilient operations.
Core Security Requirements for OPC Servers
A robust OPC security strategy is built on several foundational pillars, often referred to as a “defense-in-depth” approach. This means implementing multiple layers of security controls so that if one fails, others are in place to stop an attack.
1. Authentication: Who Are You?
Authentication is the process of verifying the identity of a client application or user attempting to connect to the OPC server. It ensures that only legitimate entities can establish a connection.
For OPC Classic: Authentication is handled by Windows User Accounts and DCOM settings. It’s rudimentary and often relies on shared accounts, which is a poor security practice.
For OPC UA: This is far more advanced. OPC UA uses X.509 certificates for application authentication. Both the client and the server must present a valid certificate, and each must trust the other’s certificate for the connection to be established. It also supports user authentication via username/password credentials or integration with systems like LDAP or Active Directory.
2. Authorization: What Are You Allowed to Do?
Once a user or application is authenticated, authorization determines what they are permitted to do. This adheres to the Principle of Least Privilege, where entities are only given the minimum access rights necessary to perform their function.
Can this user only read data, or can they also write values to the PLC?
Is this HMI application allowed to access data from all production lines, or just Line 3?
Can an operator acknowledge alarms, or is that reserved for a supervisor?
OPC UA provides fine-grained control over authorization, allowing administrators to define specific read/write permissions for different users or groups on a per-node (or per-tag) basis.
3. Encryption: Can Anyone Eavesdrop?
Encryption scrambles the data as it travels between the OPC client and server, making it unreadable to anyone who might intercept the network traffic.
OPC Classic: Has no built-in encryption. The data is sent in clear text, making it vulnerable to eavesdropping. Securing it requires a third-party tool like a VPN or an OPC Tunneller.
OPC UA: Provides robust, built-in encryption. Administrators can choose from various security policies that define the strength of the encryption and signing algorithms (e.g.,
Basic256Sha256,Aes128_Sha256_RsaOaep).
4. Data Integrity: Has the Data Been Tampered With?
Data integrity ensures that the data received is exactly what was sent and has not been altered in transit. This is typically achieved through digital signatures.
OPC Classic: Offers no data integrity mechanisms.
OPC UA: Uses cryptographic signatures to sign messages. The receiving application verifies the signature to ensure the message hasn’t been modified. This is a critical feature to prevent man-in-the-middle attacks where an attacker could intercept and alter control commands.
5. Auditing: Who Did What, and When?
Auditing involves creating a secure, tamper-proof log of all significant activities. This is crucial for forensic analysis after a security incident and for demonstrating regulatory compliance. Logs should track events such as:
Client connection attempts (successful and failed).
User session creations.
Write operations, including the old value, new value, user, and timestamp.
Security configuration changes.
Designing a Secure OPC Architecture
Architectural design is the first and most important line of defense. A flat, unsegmented network is a recipe for disaster. The goal is to create zones and conduits with strict access controls, isolating critical systems.
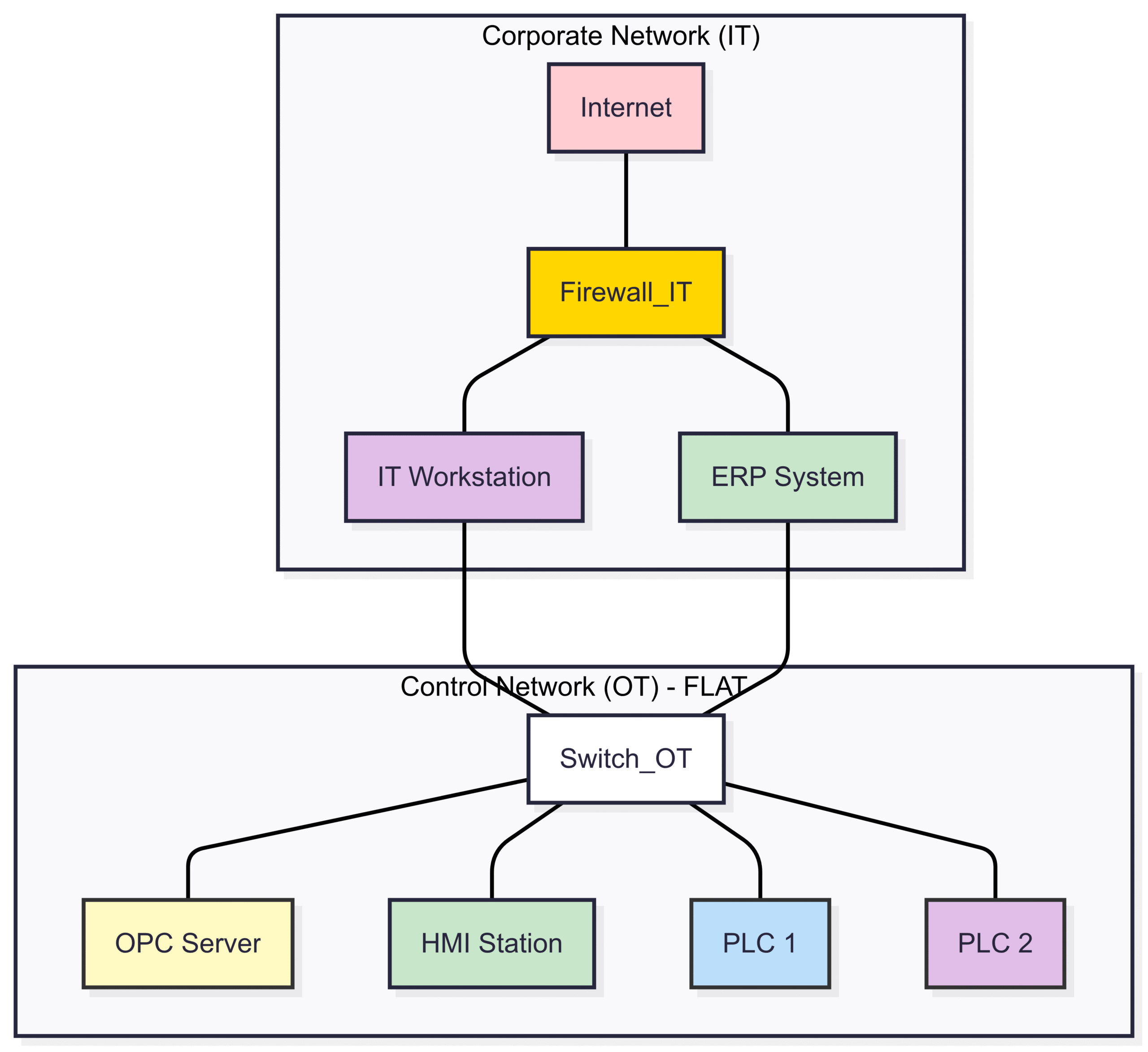
The Vulnerable Flat Network
Many older industrial networks are “flat,” meaning every device can communicate with every other device. In this architecture, if an attacker compromises a single, low-security asset (like a maintenance laptop), they can easily move laterally to attack critical systems like the OPC server and PLCs.
Diagram 1: Vulnerable Flat Network. In this dangerous design, IT systems have direct access to the OT network, and all OT devices reside on the same segment. The OPC Server and PLCs are directly exposed.
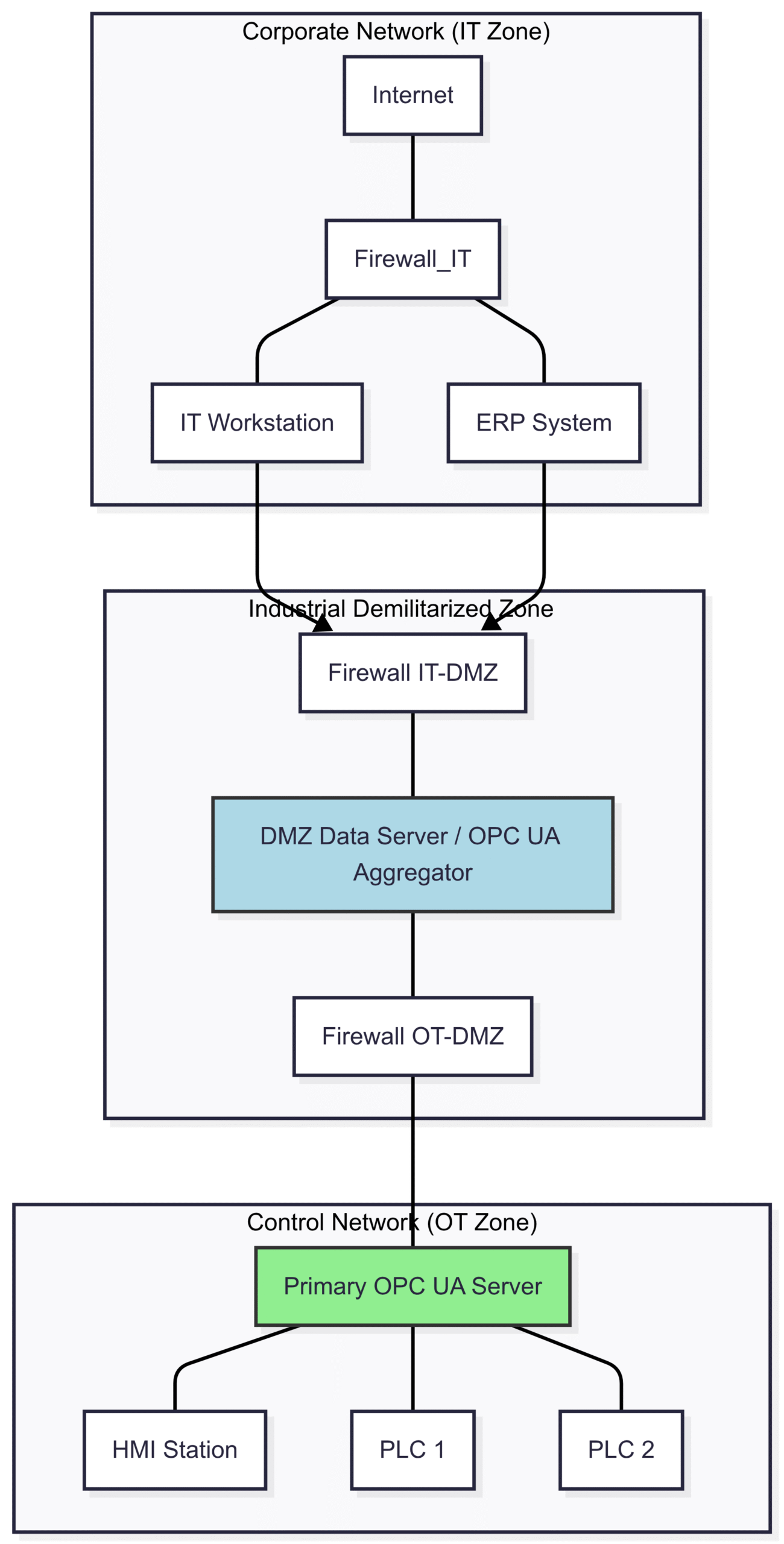
The Secure Segmented Network with a DMZ
A much more secure approach follows the Purdue Model for ICS security, which involves creating a Demilitarized Zone (DMZ) between the IT and OT networks. The DMZ acts as a buffer zone, tightly controlling the flow of traffic.
In this model, no direct communication is allowed between the corporate IT network and the control network. A designated server in the DMZ, often a secondary OPC server or a data broker, aggregates data. This server is the only machine that the control network OPC server communicates with, and it’s the only machine the corporate network can access for industrial data.
Diagram 2: Secure Segmented Architecture with DMZ. Here, firewalls strictly enforce traffic rules. The OT network is isolated. The Primary OPC UA Server only communicates outbound to the DMZ Server. The IT network can only query the DMZ Server, never the primary server, providing robust isolation.
Practical Hardening and Implementation
Beyond architecture, specific configuration steps are required to secure your OPC servers.
Hardening Legacy OPC Classic (DCOM)
If you are stuck with OPC Classic, you must take steps to harden it. This is complex and often brittle, but necessary.
DCOM Configuration (
dcomcnfg):Access Permissions: Restrict which Windows users/groups can launch and access the OPC server application. Be as specific as possible. Avoid using the “Everyone” or “Anonymous” groups.
Launch and Activation Permissions: Specify which users/groups can launch the server if it’s not already running.
Endpoints: Configure DCOM to use a limited range of TCP ports instead of its default dynamic range (135 + 1024-65535). This allows you to create much stricter firewall rules. For example, limit it to ports 10000-10010.
Firewall Rules:
Lock down the firewall to only allow traffic on the specific ports you defined in the DCOM settings.
Only allow connections from the specific IP addresses of the OPC client machines. Deny all other traffic by default.
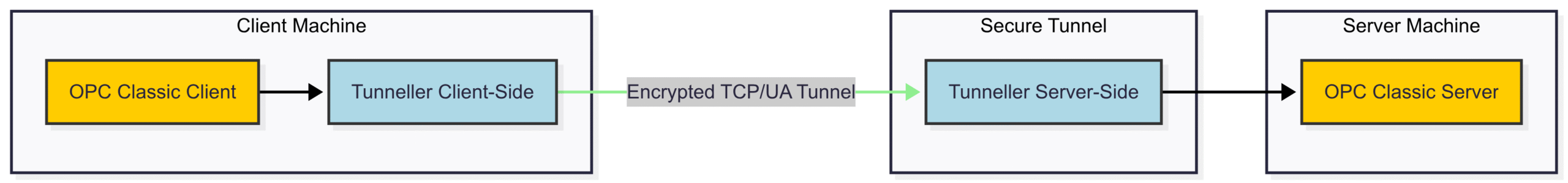
Use an OPC Tunneller: This is the highly recommended method for securing OPC Classic. An OPC Tunneller consists of two software components. One part sits on the client machine and the other on the server machine. The Tunneller encapsulates the insecure DCOM traffic within a secure, encrypted tunnel (often using OPC UA or a proprietary protocol). This completely bypasses the need for DCOM configuration across a firewall.
Diagram 3: OPC Tunneller Architecture. The Tunneller wraps insecure OPC Classic DCOM calls in a secure, firewall-friendly tunnel, eliminating DCOM issues and adding encryption.
Implementing OPC UA Security: By Design
OPC UA makes security far more straightforward because it’s an integral part of the specification.
Certificate Management: This is the foundation of OPC UA security.
Both the client and server applications need an X.509 Application Instance Certificate.
The server maintains a trust list. It will only accept connections from clients whose certificates are in this list.
The client maintains its own trust list. It will only connect to servers whose certificates are in its list.
This mutual trust establishment prevents unauthorized applications from connecting.
Choose the Right Security Policy: OPC UA offers different levels of security, defined by a “Security Policy URI”. You must select one on both the client and server.
None: Disables all security. Should only be used in completely isolated and trusted networks during initial testing. Never in production.Sign: Provides message integrity. All messages are digitally signed to prevent tampering.SignAndEncrypt: The highest level of security. All messages are signed for integrity and encrypted for confidentiality. This should be the default choice for any production system.
Configure User Access: Implement role-based access control (RBAC).
Integrate with Active Directory/LDAP for centralized user management.
Define user roles (e.g., Operator, Engineer, Supervisor).
Map these roles to specific access rights on the OPC UA server’s address space. An operator might only be able to read process values, while an engineer can also write new setpoints.
Security Best Practices Checklist
Whether you’re using OPC Classic or OPC UA, follow these universal best practices to create a resilient system.
✅ Network Segmentation: Implement a DMZ. Isolate your OT network from IT.
✅ Firewall Control: Use firewalls to enforce strict inbound and outbound traffic rules. Deny by default.
✅ Principle of Least Privilege: Give users and applications the minimum level of access they need.
✅ Upgrade to OPC UA: Plan a migration strategy to move away from OPC Classic wherever possible. The security benefits are immense.
✅ Use OPC Tunnellers: If you must use OPC Classic, use a tunneller to secure communications across the network.
✅ Patch Management: Keep the operating systems, OPC server software, and all related applications patched and up-to-date. Have a tested plan for applying patches in an OT environment.
✅ Physical Security: Control physical access to server rooms and control cabinets. An attacker with physical access can bypass many network security controls.
✅ Disable Unused Ports/Services: Harden the server’s operating system by disabling any software, services, or network ports that are not strictly necessary.
✅ Regular Audits: Periodically review security logs, firewall rules, and user access lists. Conduct penetration testing to proactively identify vulnerabilities.
✅ Backup and Recovery: Maintain regular, tested backups of your OPC server configuration and have a disaster recovery plan in place.
Conclusion: Security as a Continuous Process
In the interconnected landscape of modern industry, securing your OPC servers is not a one-time project; it’s a continuous process of vigilance, maintenance, and improvement. The design phase is the most critical opportunity to build security into the foundation of your architecture. By embracing network segmentation, adopting the robust security framework of OPC UA, and applying hardening best practices, you can transform your OPC infrastructure from a potential liability into a secure and resilient cornerstone of your operations.
Don’t wait for a security incident to expose your weaknesses. Take a proactive approach to assess your current OPC design, identify risks, and implement the layered security controls necessary to protect your data, your processes, and your people.