Mastering the Industrial Fortress: A Deep Dive into the Level 3.5 DMZ for ICCS Cybersecurity with IEC 62443
In the world of Industrial Control and Communication Systems (ICCS), the convergence of Information Technology (IT) and Operational Technology (OT) has unlocked unprecedented efficiency and connectivity. However, this integration has also opened a new front in the battle for cybersecurity. The very systems that manage our critical infrastructure—power grids, water treatment plants, and manufacturing facilities—are now more exposed than ever to sophisticated cyber threats. The key to defending these vital assets lies in robust network architecture, and at the heart of this defense is the Level 3.5 Industrial Demilitarized Zone (DMZ), a concept guided by the foundational IEC 62443 standard.
This comprehensive guide will explore the critical role of the Level 3.5 DMZ in securing industrial networks. We will dissect its architecture, understand its function within the Purdue Model, and align its implementation with the globally recognized IEC 62443 framework. Whether you are an OT manager, a cybersecurity professional, or an industrial engineer, understanding the Level 3.5 DMZ is no longer optional—it’s essential for operational resilience and national security.
The Foundation: Understanding the Purdue Model for ICS Architecture
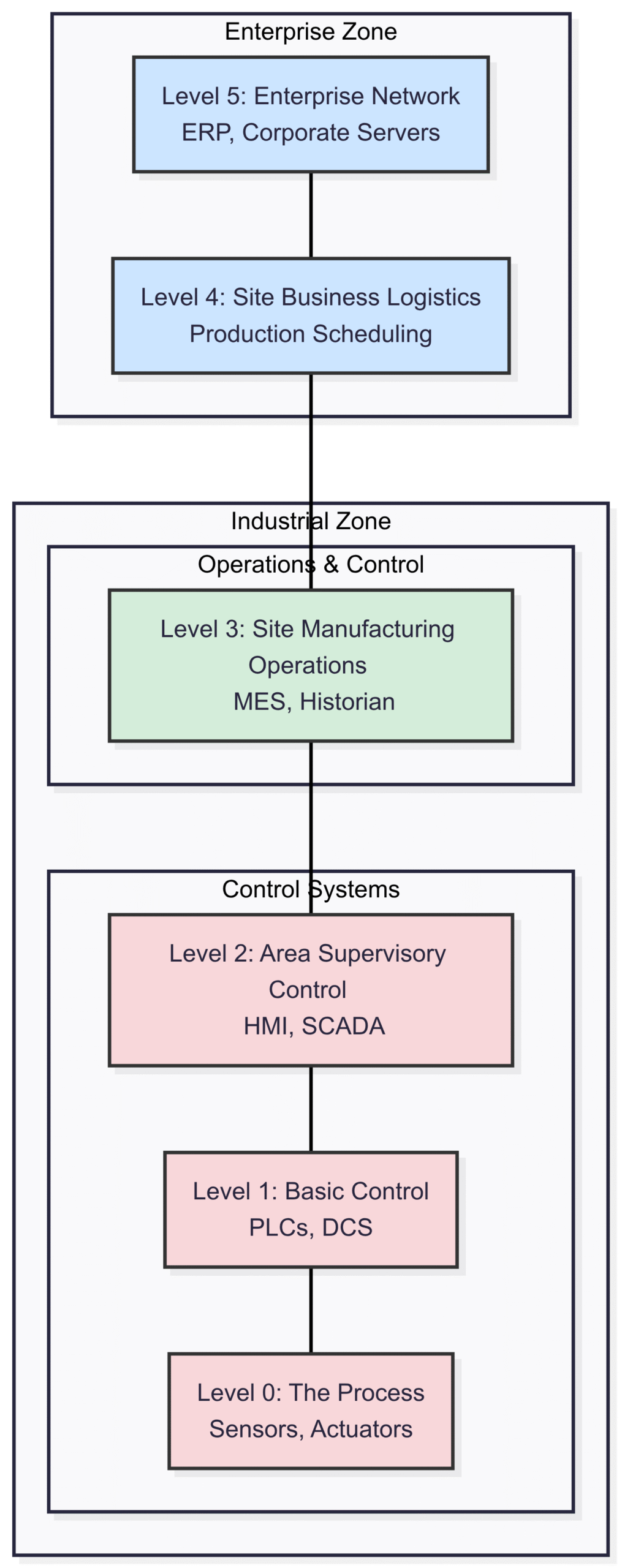
Before we can build our fortress, we must understand the landscape. The Purdue Model for Industrial Control Systems (ICS) provides a standardized framework for conceptualizing the different layers of an industrial network. It organizes the complex web of devices, systems, and applications into logical levels, each with a distinct function. This segmentation is the first step towards a defensible security posture.
Level 5: Enterprise Network – The corporate IT domain. This is where business systems like Enterprise Resource Planning (ERP), email servers, and internet access reside.
Level 4: Site Business Planning & Logistics – This level manages the day-to-day business operations of the site, including production scheduling and inventory management.
Level 3: Site Manufacturing Operations & Control – The supervisory level that manages the production workflow. Systems here include Manufacturing Execution Systems (MES), batch management, and data historians that collect and store operational data.
Level 2: Area Supervisory Control – This level contains the systems that directly supervise and control the physical process, such as Human-Machine Interfaces (HMIs) and SCADA supervisory systems.
Level 1: Basic Control – The domain of Programmable Logic Controllers (PLCs) and Distributed Control Systems (DCS) that execute the control logic for the industrial process.
Level 0: The Process – The physical world of sensors, actuators, motors, and other devices that directly interact with and control the industrial process.
Here’s a visual representation of the traditional Purdue Model.
The primary security challenge arises at the boundary between Level 3 and Level 4. The IT world (Levels 4/5) needs data from the OT world (Levels 0-3) for business decisions, and the OT world sometimes needs services from IT (like patch updates or remote support). Uncontrolled communication across this boundary is a direct path for malware and attackers to pivot from the less-secure IT environment into the highly sensitive OT network.
Introducing Level 3.5: The Industrial Demilitarized Zone (IDMZ)
A traditional IT DMZ is a perimeter network that protects an organization’s internal LAN from untrusted external networks. However, simply placing a standard DMZ between the IT and OT networks is insufficient and dangerous. OT protocols, systems, and security requirements are fundamentally different from those in IT.
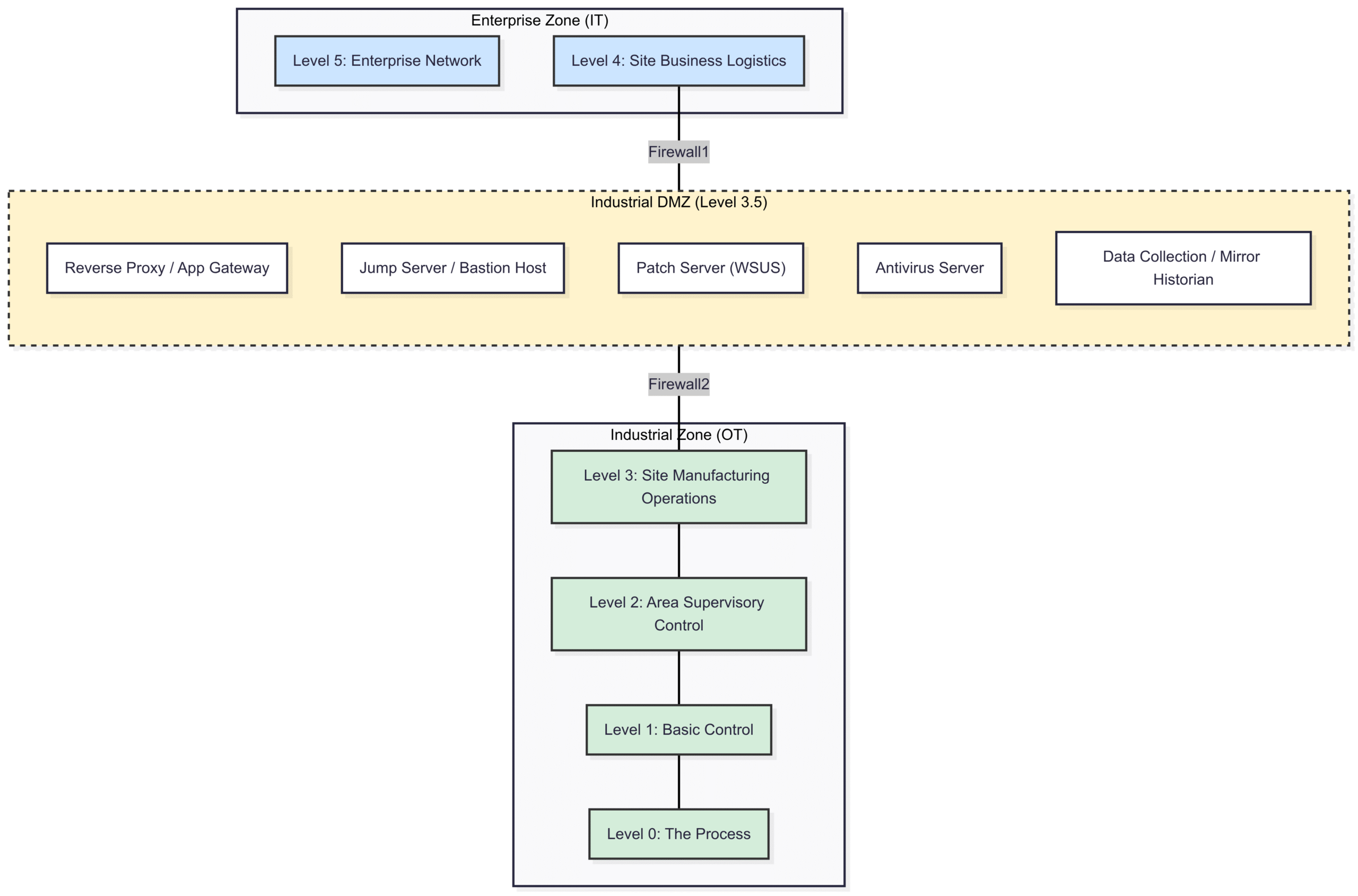
This is where Level 3.5, the Industrial DMZ (IDMZ), comes into play. It is not just another network segment; it is a purpose-built, security-hardened buffer zone specifically designed to broker and secure all communication between the Enterprise Zone (IT) and the Industrial Zone (OT).
The core principle of the Level 3.5 IDMZ is termination and initiation. No traffic ever passes directly through the IDMZ. Instead, a session from the IT network terminates at a server in the IDMZ, and a new, separate session is initiated from the IDMZ to the OT network. This breaks the direct communication path, providing a critical air gap for inspection and control.
Why Level 3.5 is Crucial for OT Security
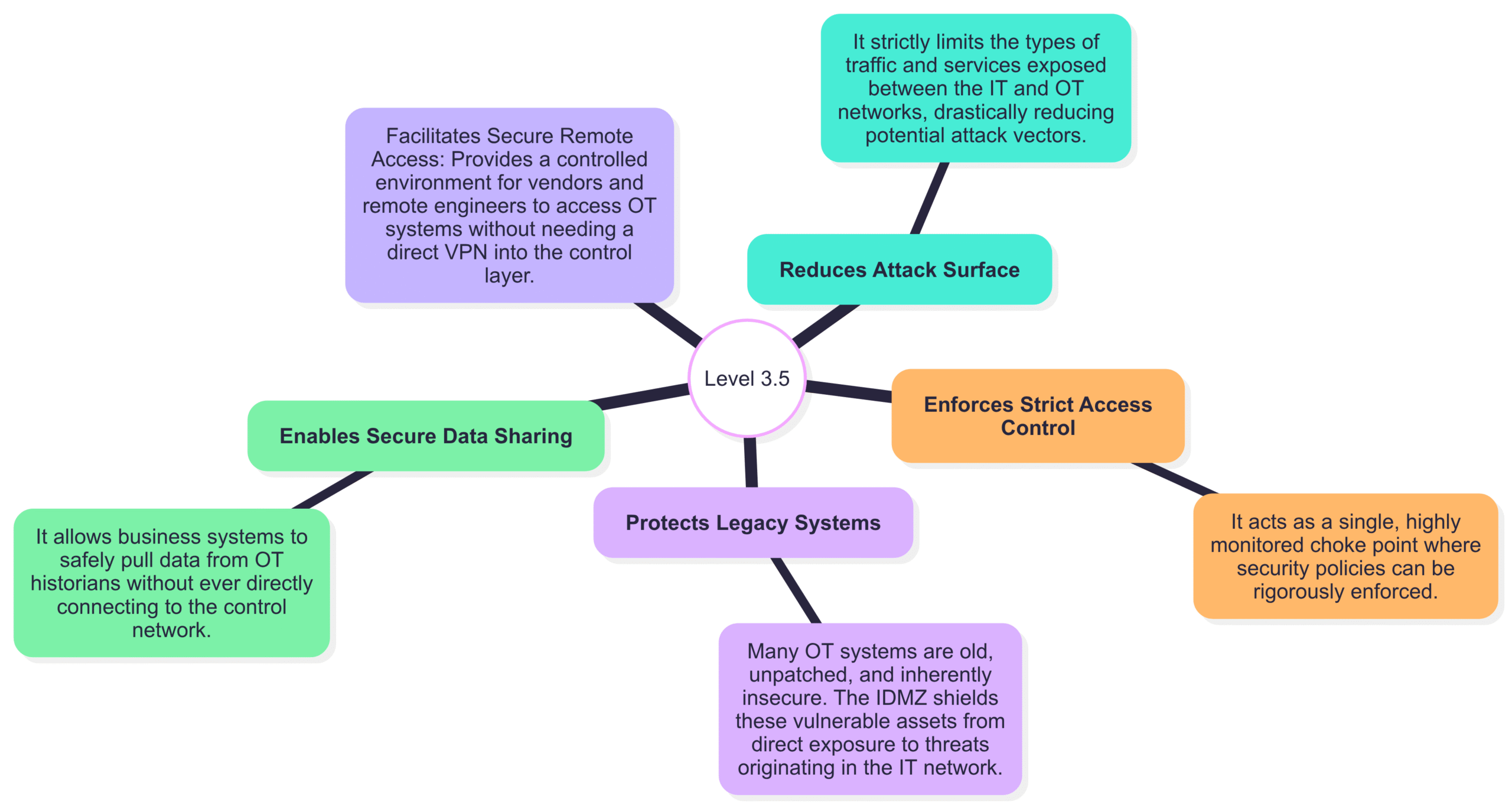
Reduces Attack Surface: It strictly limits the types of traffic and services exposed between the IT and OT networks, drastically reducing potential attack vectors.
Enforces Strict Access Control: It acts as a single, highly monitored choke point where security policies can be rigorously enforced.
Protects Legacy Systems: Many OT systems are old, unpatched, and inherently insecure. The IDMZ shields these vulnerable assets from direct exposure to threats originating in the IT network.
Enables Secure Data Sharing: It allows business systems to safely pull data from OT historians without ever directly connecting to the control network.
Facilitates Secure Remote Access: Provides a controlled environment for vendors and remote engineers to access OT systems without needing a direct VPN into the control layer.
The diagram below shows the strategic placement of the Level 3.5 IDMZ within the Purdue Model architecture.
Aligning with IEC 62443: A Standards-Based Approach to Security
Implementing a Level 3.5 IDMZ is not an ad-hoc process. The IEC 62443 series of standards provides a comprehensive, risk-based framework for securing Industrial Automation and Control Systems (IACS). This standard is the blueprint for designing, implementing, and maintaining a cyber-resilient OT environment.
Two key concepts from IEC 62443 are central to designing an IDMZ: Zones and Conduits.
Zone: A grouping of logical or physical assets that share common security requirements. In our model, the Enterprise Network is one zone, the Industrial Control Network is another, and the Level 3.5 IDMZ is a critical third zone.
Conduit: The communication path and security controls between two zones. The firewalls and other security services that connect the IT zone to the IDMZ, and the IDMZ to the OT zone, are conduits.
IEC 62443 requires a risk assessment to determine the target Security Level (SL) for each zone. The SLs range from SL-1 (protection against casual or coincidental violation) to SL-4 (protection against nation-state-level threats). The Level 3.5 IDMZ zone must have a target SL that is appropriate for the risk profile of the assets it is protecting in the OT zone.
By applying the Zones and Conduits model, we can systematically define the security requirements for our IDMZ:
Identify Assets: List all systems that will reside in the IDMZ (e.g., reverse proxies, patch servers, data collectors).
Define Boundaries: Clearly establish the network boundaries between the IT zone, the IDMZ zone, and the OT zone.
Segment Conduits: Treat the IT-to-IDMZ link and the IDMZ-to-OT link as two separate conduits with distinct security policies.
Define Security Requirements: For each conduit, define the required security controls. For example, the conduit between the IDMZ and the OT network will have much stricter rules and will likely only allow OT-native protocols initiated from the OT side.
Core Components and Technologies of a Robust Level 3.5 IDMZ
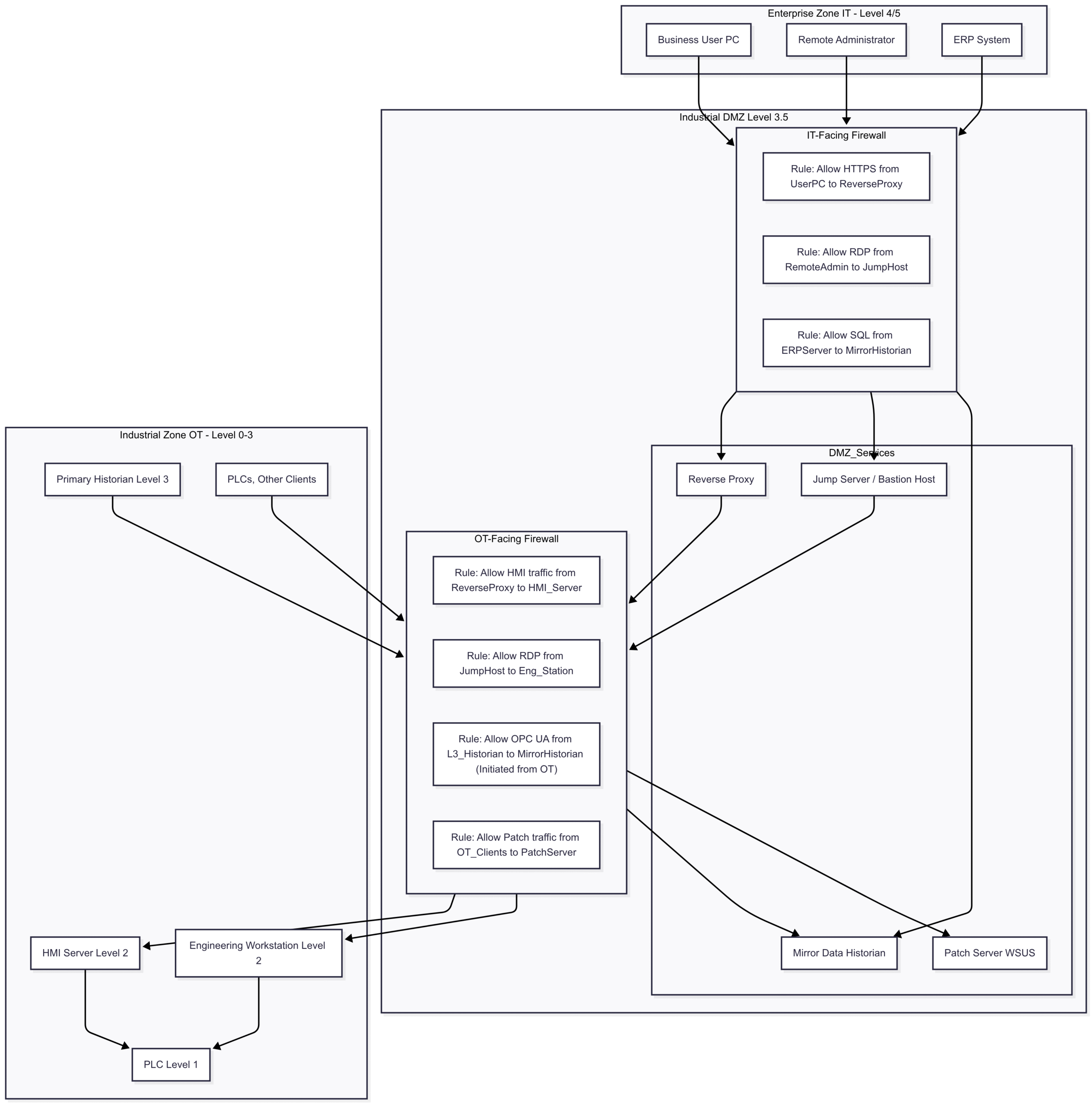
A truly effective Industrial DMZ is more than just a pair of firewalls. It’s an ecosystem of security technologies working in concert to enforce the “terminate and initiate” principle.
1. Industrial Firewalls (NGFWs)
The gatekeepers of the IDMZ are its firewalls. These cannot be standard IT firewalls. They must be Next-Generation Firewalls (NGFWs) with Deep Packet Inspection (DPI) capabilities for industrial protocols like Modbus/TCP, DNP3, OPC, and S7. This allows the firewall to not only check source and destination IP addresses but also to understand and validate the commands being sent. For example, a firewall can be configured to allow a read command (function code 03) but block a write command (function code 06) to a PLC.
2. Reverse Proxies and Application Gateways
These are the workhorses of the IDMZ. When a user in the IT network needs to access an application (like an HMI web interface) in the OT network, they don’t connect directly. They connect to the reverse proxy in the IDMZ. The proxy then establishes a new, separate connection to the HMI in the OT network. This shields the identity and characteristics of the internal OT server and ensures all traffic is brokered.
3. Jump Servers / Bastion Hosts
For remote administration by vendors or engineers, direct VPN access to the control network is a recipe for disaster. Instead, remote users authenticate to a hardened Jump Server or Bastion Host in the IDMZ. This server is heavily monitored and provides limited, role-based access to specific systems within the OT network. All sessions are logged and often recorded.
4. Patch and Antivirus Management Servers
Patching OT systems is a notoriously difficult task. Placing a Windows Server Update Services (WSUS) server or an antivirus update server in the IDMZ allows it to download patches and signature updates from the internet (IT Zone). Internal OT systems can then connect only to this server in the IDMZ to pull updates, without ever touching the internet directly.
5. Data Diodes
In high-security environments (like nuclear or power transmission), even the risk of a misconfigured firewall is unacceptable. A Data Diode is a hardware device that enforces a one-way data flow using fiber optics. It physically cannot transmit data in the reverse direction. This is the ultimate tool for ensuring that data can flow out of the OT network (e.g., from a historian to a corporate server) with zero risk of any traffic flowing back in.
6. Mirrored Data Historians
To satisfy the IT network’s thirst for data, a common practice is to place a primary data historian in Level 3 and a “mirror” or replica historian in the Level 3.5 IDMZ. The Level 3 historian initiates a connection and pushes data out to the IDMZ historian. Business users in the IT network can then query the mirror historian in the IDMZ, completely isolating them from the live control network.
Detailed Architecture of a Level 3.5 IDMZ
This diagram illustrates how these components work together to create a multi-layered defense.
Best Practices for Implementation and Operation
Building the IDMZ is only half the battle. Operating it securely requires continuous diligence.
Default Deny: The foundational rule for all firewalls in the IDMZ is “deny all, permit by exception.” Only explicitly defined and justified traffic should be allowed. Every rule should have a business owner and an expiration date.
No Direct Routing: Never configure the firewalls to route traffic directly between the IT and OT zones. All connections must terminate in the IDMZ.
Network Address Translation (NAT): Use NAT extensively on the IDMZ firewalls to hide the internal IP addressing scheme of the OT network. An attacker in the IT zone should have no visibility into the OT network structure.
Secure Protocols: Enforce the use of modern, secure, and encrypted protocols. For example, mandate OPC UA (which has built-in security) over the insecure, legacy OPC Classic (DCOM-based).
Continuous Monitoring: All traffic passing into, out of, and within the IDMZ must be logged and sent to a Security Information and Event Management (SIEM) system. Monitor for anomalous traffic patterns and failed connection attempts.
Change Management: Any change to a firewall rule, a server configuration, or an application within the IDMZ must go through a formal change management process that includes a security review.
Incident Response: Develop and practice an incident response plan specifically for a breach of the IDMZ. How do you disconnect it? How do you maintain operations? Who has the authority to make these decisions?
Conclusion: The Unsung Hero of Industrial Cybersecurity
The Level 3.5 Industrial DMZ is the unsung hero of modern OT cybersecurity. It is not merely a firewall rule; it’s a comprehensive architectural philosophy guided by the robust framework of IEC 62443. By creating a strictly controlled buffer zone that terminates and brokers all IT/OT communication, the IDMZ serves as the primary defense against threats pivoting from the corporate world into the critical control systems that run our world.
Implementing a well-designed IDMZ reduces the attack surface, protects vulnerable legacy systems, and enables necessary business connectivity without compromising operational safety and reliability. In an era of increasing cyber-physical threats, mastering the art and science of the Level 3.5 IDMZ is no longer a best practice—it’s a fundamental requirement for securing our critical industrial infrastructure for the future.