Case Studies: IEC 62443 Implementation in Industrial Plants
In the intricate and interconnected world of industrial automation and control systems (IACS), cybersecurity is no longer a mere IT concern—it’s a critical operational imperative. As industrial plants increasingly embrace digitalization to enhance efficiency and productivity, they also expose their operational technology (OT) to a growing landscape of cyber threats. The IEC 62443 series of standards has emerged as the leading framework for securing IACS environments, providing a comprehensive and risk-based approach to mitigating cyber risks. This blog explores the practical application of IEC 62443 through a series of case studies, illustrating how industrial plants across different sectors have successfully implemented the standard to bolster their cyber defenses.
The Imperative for OT Cybersecurity: Why IEC 62443?
Before delving into the case studies, it’s essential to understand the significance of IEC 62443. Unlike traditional IT cybersecurity frameworks, IEC 62443 is specifically tailored to the unique requirements and challenges of industrial environments. It recognizes that in the OT world, availability and safety are paramount. A cyber incident in an industrial plant can lead to production downtime, equipment damage, environmental hazards, and even loss of life.
The standard adopts a holistic “defense-in-depth” strategy, creating multiple layers of security to protect critical assets. One of the core concepts of IEC 62443 is the establishment of zones and conduits. Zones are logical or physical groupings of assets with similar security requirements, while conduits are the communication channels that connect these zones. By segmenting the network into zones and controlling the data flow through secure conduits, plants can contain the impact of a cyberattack and prevent it from spreading across the entire facility.
Another key aspect of IEC 62443 is the principle of shared responsibility. Cybersecurity is not solely the responsibility of the asset owner; it’s a collaborative effort that involves system integrators, product suppliers, and service providers. Each stakeholder has a role to play in ensuring the overall security of the IACS.
Case Study 1: Automotive Manufacturing – Securing the Production Line
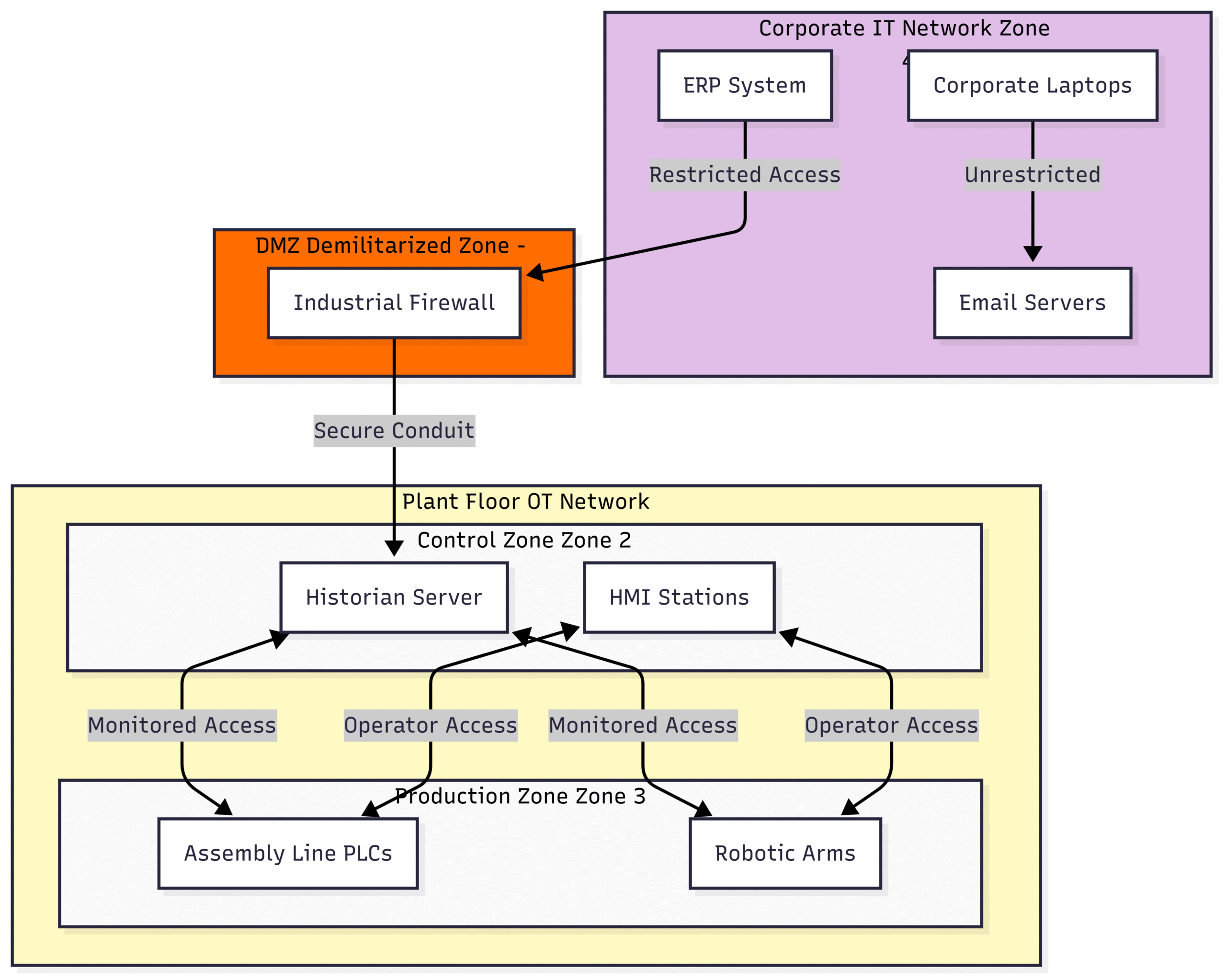
The Challenge: A major automotive manufacturer was facing increasing pressure to secure its highly automated production facilities. Their plant network was largely flat, meaning there was no segmentation between the corporate IT network and the critical OT systems controlling the assembly line. This lack of segmentation posed a significant risk, as a malware infection on a corporate laptop could potentially propagate to the plant floor, causing costly production stoppages. The manufacturer needed a robust cybersecurity framework to protect its just-in-time production model and ensure the integrity of its manufacturing processes.
The “Before” State: A Flat and Vulnerable Network
The initial state of the automotive plant’s network was a common scenario in many industrial facilities. The IT and OT networks were interconnected without adequate security controls. This meant that a security breach on the business side of the house could easily spill over into the production environment.
Block Diagram: Before IEC 62443 Implementation
The Implementation Journey: A Phased Approach to IEC 62443
The manufacturer embarked on a multi-phased implementation of IEC 62443, starting with a comprehensive risk assessment to identify the most critical assets and vulnerabilities. The following steps were taken:

Risk Assessment and Zoning: The first step was to conduct a thorough risk assessment in line with IEC 62443-3-2. This involved identifying all the assets on the plant floor, from PLCs and robots to HMIs and network switches. Based on their criticality and security requirements, these assets were grouped into logical zones. For example, the robotic welding cells were designated as a high-security zone, while the paint shop’s control system formed another.
Network Segmentation and Conduit Creation: With the zones defined, the next step was to segment the network using industrial firewalls. These firewalls acted as secure conduits, controlling the traffic flowing between the zones. The principle of “least privilege” was applied, meaning that only the necessary communication was allowed. For instance, the ERP system in the corporate network was only permitted to send production orders to the assembly line PLCs, and all other traffic was blocked.
Implementing Security Controls: A range of security controls, as outlined in IEC 62443-3-3, were implemented within each zone. This included:
Access Control: Implementing role-based access control (RBAC) to ensure that only authorized personnel could access and modify the control systems.
Hardening of Devices: Disabling unused ports and services on PLCs, HMIs, and network devices to reduce the attack surface.
Patch Management: Establishing a process for testing and deploying security patches for OT systems in a controlled manner to avoid disrupting production.
Network Monitoring: Deploying an intrusion detection system (IDS) to monitor network traffic for any suspicious activity.
The “After” State: A Resilient and Secure Production Environment
The implementation of IEC 62443 transformed the plant’s cybersecurity posture. The segmented network with clearly defined zones and conduits significantly reduced the risk of a cyber incident spreading across the facility.
Block Diagram: After IEC 62443 Implementation
The Results: Following the implementation of IEC 62443, the automotive manufacturer achieved a significant improvement in its cybersecurity resilience. While specific metrics are often confidential, the qualitative benefits were clear:
Reduced Risk of Production Downtime: The segmented network contained potential threats, preventing them from impacting critical production assets.
Improved Security Posture: The implementation of multiple security controls made it much more difficult for attackers to compromise the IACS.
Enhanced Compliance: The manufacturer was able to demonstrate compliance with industry best practices and regulatory requirements.
Case Study 2: Water Utility – Safeguarding Critical Infrastructure
The Challenge: A regional water utility, responsible for providing clean drinking water to millions of people, recognized the urgent need to enhance the cybersecurity of its water treatment and distribution facilities. The utility’s SCADA (Supervisory Control and Data Acquisition) system was aging, and many of its components were running on legacy operating systems that were no longer supported by the vendors. This made them highly vulnerable to cyberattacks. A successful attack on the water utility could have devastating consequences, including the contamination of the water supply and disruption of services.
The “Before” State: A Legacy System with Open Doors
The water utility’s network was a patchwork of old and new technologies. The SCADA system was connected to the internet to allow for remote monitoring, but the connection was not adequately secured. This created a direct pathway for attackers to potentially gain access to the critical control systems.
The Implementation Journey: A Focus on Foundational Controls
The water utility’s IEC 62443 implementation focused on establishing foundational cybersecurity controls and modernizing its legacy systems. Key steps included:
Asset Inventory and Vulnerability Assessment: The first priority was to create a comprehensive inventory of all the assets in the SCADA system and identify their vulnerabilities. This was a challenging task, as many of the devices were located in remote and hard-to-reach locations.
Securing Remote Access: The utility implemented a secure remote access solution that required multi-factor authentication for all users connecting to the SCADA system. All remote connections were routed through a secure gateway in a demilitarized zone (DMZ) that separated the SCADA network from the internet.
Upgrading Legacy Systems: A phased approach was taken to upgrade the legacy systems to modern, more secure platforms. Where immediate upgrades were not feasible, compensating controls were put in place, such as isolating the vulnerable devices in a dedicated security zone.
Implementing a Cybersecurity Management System (CSMS): The utility established a CSMS based on IEC 62443-2-1. This involved defining cybersecurity policies and procedures, assigning roles and responsibilities, and establishing a security awareness program for all employees.
The “After” State: A Modern and Defensible SCADA System
The implementation of IEC 62443 resulted in a much more secure and resilient SCADA system. The modernized infrastructure, coupled with robust security controls, provided the utility with the confidence that its critical operations were well-protected.
The Results: The water utility’s investment in IEC 62443 paid significant dividends:
Protection of Public Health and Safety: The enhanced cybersecurity measures safeguarded the integrity of the water supply, protecting public health.
Increased Operational Resilience: The modernized and secure SCADA system was less susceptible to disruptions, ensuring the continuous supply of clean water.
Demonstrable Due Diligence: The utility was able to demonstrate to regulators and the public that it was taking a proactive approach to cybersecurity. This was particularly important following a government mandate in Qatar for all water and electricity utilities to comply with IEC 62443.
Case Study 3: Oil and Gas – Protecting High-Stakes Operations
The Challenge: A multinational oil and gas company with offshore and onshore facilities faced the dual challenge of protecting its valuable intellectual property and ensuring the safety of its high-risk operations. A cyberattack on an oil and gas facility could lead to catastrophic consequences, including explosions, oil spills, and significant financial losses. The company needed a globally consistent cybersecurity framework to protect its diverse and geographically dispersed assets.
The “Before” State: A Complex and Interconnected Environment
The oil and gas company’s operational environment was incredibly complex, with a vast network of sensors, controllers, and safety instrumented systems (SIS). These systems were often integrated with the corporate network to facilitate data analysis and decision-making. This interconnectivity, while beneficial for operational efficiency, also created a large attack surface.
The Implementation Journey: A Risk-Based and Holistic Approach
The oil and gas company adopted a comprehensive and risk-based approach to implementing IEC 62443 across its global operations. The implementation was driven by a central cybersecurity team that worked closely with the local engineering and operations teams at each facility.
Defining Corporate Standards: The company developed a set of corporate cybersecurity standards based on IEC 62443. These standards provided a consistent framework for all facilities to follow, while still allowing for flexibility to address local risks and requirements.
Security Level Targeting: For each zone, the company defined a target security level (SL-T) based on a detailed risk assessment. This allowed them to prioritize their security investments and focus on protecting the most critical assets. For example, the SIS, which is responsible for shutting down the plant in an emergency, was assigned the highest security level.
Supply Chain Security: The company recognized that cybersecurity is a shared responsibility and worked closely with its vendors to ensure that all new products and systems complied with the relevant parts of IEC 62443, such as IEC 62443-4-1 for secure product development.
Continuous Monitoring and Improvement: The company implemented a continuous monitoring program to detect and respond to cyber threats in real time. Regular security audits and assessments were conducted to identify new vulnerabilities and ensure that the security controls remained effective.
The “After” State: A Culture of Cybersecurity
The implementation of IEC 62443 helped to foster a strong culture of cybersecurity throughout the organization. Cybersecurity was no longer seen as a purely technical issue but as a core business enabler.
The Results: The oil and gas company’s commitment to IEC 62443 yielded significant benefits:
Improved Safety and Reliability: The enhanced cybersecurity measures reduced the risk of cyberattacks that could compromise the safety and reliability of its operations.
Protection of Intellectual Property: The segmented network and access controls helped to protect the company’s valuable intellectual property from theft.
Enhanced Global Consistency: The corporate cybersecurity standards ensured a consistent and high level of security across all its facilities worldwide.
Conclusion: A Roadmap to Industrial Cybersecurity Resilience
These case studies demonstrate that IEC 62443 provides a practical and effective framework for securing industrial plants in a variety of sectors. By adopting a risk-based approach, segmenting networks into zones and conduits, and implementing a defense-in-depth strategy, industrial organizations can significantly enhance their cybersecurity posture and protect their critical operations from the ever-evolving threat landscape. The journey to IEC 62443 compliance is not a one-time project but a continuous process of assessment, improvement, and vigilance. As industrial plants become more connected and automated, the principles of IEC 62443 will become even more critical in ensuring a safe, reliable, and secure industrial future.