Decoding Cyber Risk in Industrial Environments: A Deep Dive into IEC 62443 Risk Assessment
In the intricate and interconnected world of industrial automation and control systems (IACS), the specter of cyber threats looms larger than ever. A successful attack on these critical systems, which form the backbone of manufacturing, energy, transportation, and other essential sectors, can lead to catastrophic consequences, including production downtime, equipment damage, environmental incidents, and even loss of life. To navigate this high-stakes landscape, organizations are increasingly turning to the internationally recognized IEC 62443 standard for a structured and comprehensive approach to cybersecurity. At the heart of this standard lies a robust framework for conducting a thorough cybersecurity risk assessment, a fundamental process for identifying, analyzing, and mitigating cyber risks in industrial systems.
This blog post will provide an in-depth exploration of the cybersecurity risk assessment process as defined by IEC 62443, offering a roadmap for asset owners, system integrators, and product suppliers to bolster their defenses against the evolving threat landscape. We will delve into the core concepts of the standard, including the pivotal role of zones and conduits, the determination of security levels, and the cyclical nature of risk management.
The Imperative of a Specialized Approach: Why IT-Centric Risk Assessments Fall Short in OT
For decades, Information Technology (IT) professionals have honed their skills in conducting risk assessments for enterprise networks. However, the unique characteristics of Operational Technology (OT) environments, where IACS reside, demand a tailored approach. Unlike the IT world, where confidentiality and data integrity often take precedence, the paramount concerns in OT are availability, safety, and reliability. A halted production line or a malfunctioning safety instrumented system carries far greater immediate consequences than a compromised email server.
The IEC 62443 series of standards acknowledges this fundamental distinction. It provides a common language and a structured methodology that bridges the gap between the IT and OT domains, fostering a holistic and collaborative approach to cybersecurity. The standard emphasizes a lifecycle approach, recognizing that cybersecurity is not a one-time project but an ongoing process of assessment, implementation, and continuous improvement.
The Foundation of IEC 62443 Risk Assessment: A Phased Approach
The cybersecurity risk assessment process outlined in IEC 62443-3-2, “Security for industrial automation and control systems – Part 3-2: Security risk assessment for system design,” provides a systematic methodology for understanding and managing cyber risks. The process can be broken down into several key phases, each building upon the last to create a comprehensive security posture.
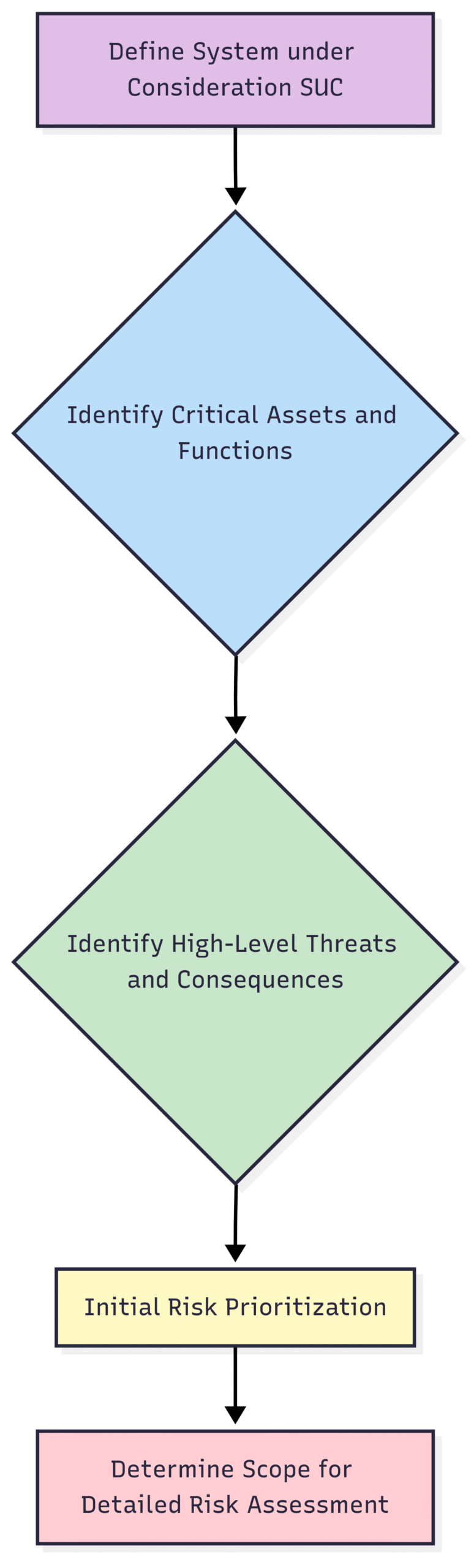
Phase 1: System Under Consideration (SuC) Definition and High-Level Risk Assessment
The initial step is to clearly define the System under Consideration (SuC). This involves identifying the boundaries of the IACS that will be assessed. It could be an entire plant, a specific production line, or even a single critical control system. Once the SuC is defined, a high-level risk assessment is performed. This initial analysis aims to identify the most critical assets and potential high-level threats without delving into granular detail. It serves as a preliminary screening to prioritize resources and focus subsequent efforts on the areas of greatest concern.
Block Diagram: High-Level Risk Assessment Process
Phase 2: Partitioning the System into Zones and Conduits
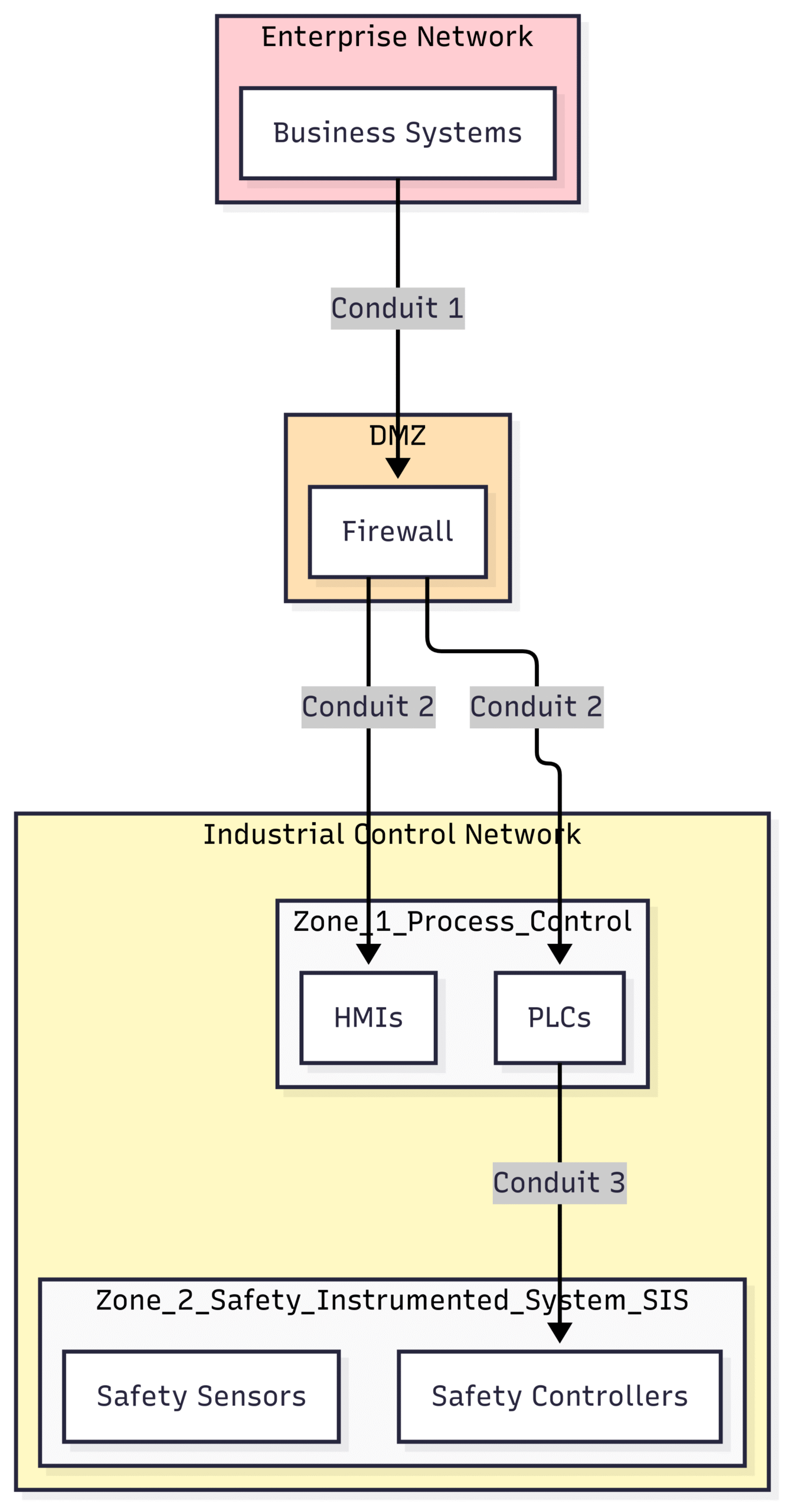
A cornerstone of the IEC 62443 approach is the concept of zones and conduits. This powerful technique involves segmenting the IACS into logical groupings of assets that share common security requirements.
Zones: A zone is a grouping of physical or logical assets that share a common set of security requirements. For example, all the controllers and HMI stations for a specific manufacturing cell could be grouped into a single zone. The principle is to create boundaries where security policies can be enforced.
Conduits: A conduit is a communication channel that connects two or more zones. It represents the pathway for data flow between different parts of the system. By identifying and securing these conduits, organizations can control and monitor the information exchange between zones, preventing unauthorized access and lateral movement by attackers.
Block Diagram: Zone and Conduit Model
In this simplified diagram, the Enterprise Network and the Industrial Control Network are separated by a Demilitarized Zone (DMZ) containing a firewall. The Industrial Control Network is further segmented into a Process Control Zone and a more critical Safety Instrumented System (SIS) Zone. Conduits represent the controlled communication paths between these zones.
This segmentation is not arbitrary. The grouping of assets into zones is based on factors such as:
Criticality: Assets that are essential for the primary function of the IACS are grouped together.
Consequences of Compromise: Assets whose compromise would lead to similar consequences are placed in the same zone.
Trust Levels: Assets that have similar levels of trust are grouped together.
Communication Patterns: Assets that frequently communicate with each other are logical candidates for being in the same zone.
By partitioning the system into zones and conduits, organizations can move away from a monolithic, perimeter-focused security model to a more granular and resilient defense-in-depth strategy.
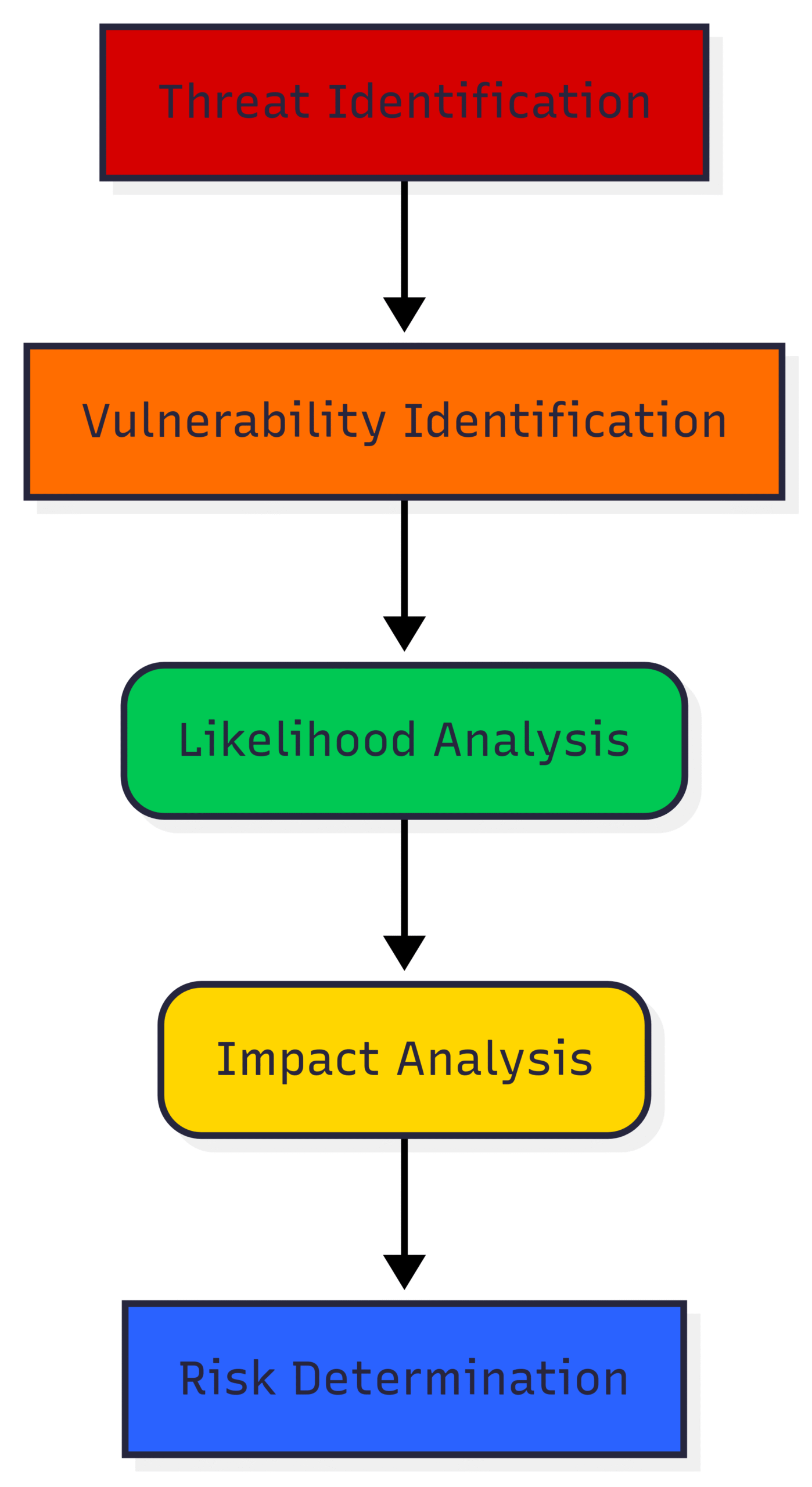
Phase 3: Detailed Risk Assessment
With the system logically segmented, the next phase is to conduct a detailed risk assessment for each zone and conduit. This is a more in-depth analysis that involves several key steps:
Threat Identification: This step involves brainstorming and identifying potential threats to the assets within each zone. Threats can be categorized as adversarial (e.g., hackers, malicious insiders) or non-adversarial (e.g., human error, equipment failure). Methodologies like STRIDE (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege) can be used to systematically identify a wide range of threats.
Vulnerability Identification: For each identified threat, the next step is to identify vulnerabilities in the system that could be exploited. This could include unpatched software, weak configurations, insecure network protocols, or a lack of physical security controls.
Likelihood and Impact Analysis: Once threats and vulnerabilities are identified, the likelihood of a successful attack and the potential impact of that attack are assessed.
Likelihood is the probability that a vulnerability will be exploited by a specific threat. This is often a qualitative assessment (e.g., high, medium, low) based on factors like the attacker’s motivation and capability, and the ease of exploitation.
Impact refers to the consequences of a successful attack. In the context of IACS, this is measured in terms of its effect on safety, operational availability, and financial loss.
Risk Determination: The level of risk is a function of the likelihood and impact of a potential security incident. It is often calculated using a risk matrix that combines these two factors.
Block Diagram: Detailed Risk Assessment Cycle
Phase 4: Determining the Target Security Level (SL-T)
A key output of the detailed risk assessment is the determination of the Target Security Level (SL-T) for each zone and conduit. The IEC 62443 standard defines four Security Levels (SLs), ranging from SL 1 (protection against casual or coincidental violation) to SL 4 (protection against sophisticated attacks with significant resources).
Security Level (SL) | Protection Against |
SL 1 | Casual or coincidental violation |
SL 2 | Intentional violation using simple means |
SL 3 | Intentional violation using sophisticated means |
SL 4 | Intentional violation using sophisticated means with significant resources |
The SL-T for a particular zone is determined by the highest risk identified within that zone. For example, if the compromise of a specific controller could lead to a significant safety incident (high impact), and there is a credible threat with the capability to exploit a known vulnerability (medium to high likelihood), a higher SL-T (e.g., SL 3 or SL 4) would be assigned to that zone.
It’s important to note that the Security Level is not a single value but a vector that addresses seven Foundational Requirements (FRs) defined in the standard:
FR 1: Identification and Authentication Control (IAC)
FR 2: Use Control (UC)
FR 3: System Integrity (SI)
FR 4: Data Confidentiality (DC)
FR 5: Restricted Data Flow (RDF)
FR 6: Timely Response to Events (TRE)
FR 7: Resource Availability (RA)
Therefore, the SL-T for a zone is a set of seven values, one for each FR, reflecting the required level of security for each of these fundamental aspects.
Phase 5: Gap Analysis and Determining the Achieved Security Level (SL-A)
Once the Target Security Level (SL-T) has been established for each zone and conduit, the next step is to assess the existing security controls to determine the Achieved Security Level (SL-A). This involves a detailed review of the current security measures in place, including technical controls (e.g., firewalls, intrusion detection systems), administrative controls (e.g., policies and procedures), and physical controls.
The comparison of the SL-T and the SL-A constitutes the gap analysis. This analysis highlights the areas where the current security posture falls short of the desired level of protection.
Phase 6: Risk Mitigation and Countermeasure Implementation
The final phase of the risk assessment process is to develop and implement a plan to close the identified gaps and reduce the overall risk to an acceptable level. This involves selecting and implementing appropriate countermeasures to raise the SL-A to meet or exceed the SL-T. The choice of countermeasures should be based on a cost-benefit analysis, prioritizing those that provide the greatest risk reduction for the investment.
The IEC 62443 standard provides a comprehensive catalog of security requirements that can be used to select appropriate countermeasures. These requirements are mapped to the seven Foundational Requirements and the four Security Levels, providing a clear and structured approach to security control implementation.
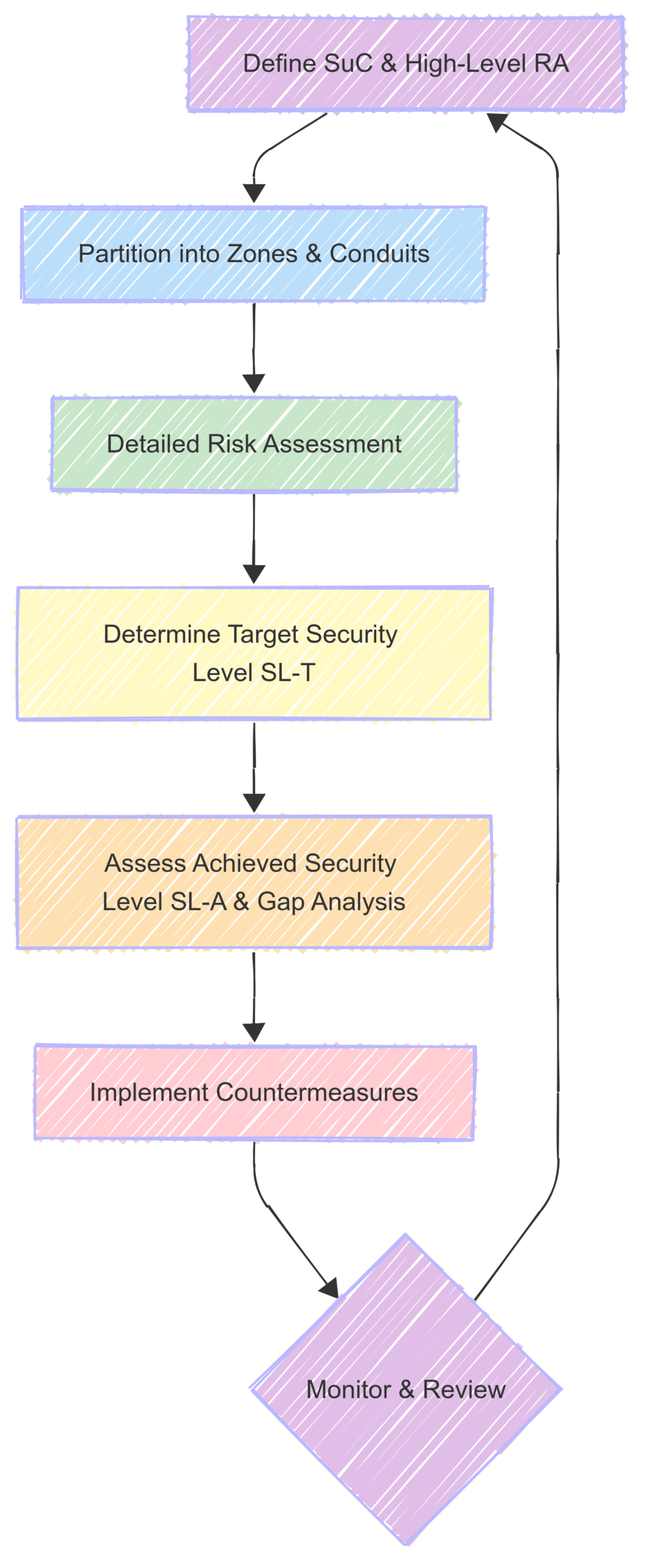
The Cyclical Nature of Risk Assessment: A Continuous Journey
It is crucial to understand that a cybersecurity risk assessment is not a one-time event. The threat landscape is constantly evolving, new vulnerabilities are discovered regularly, and changes to the IACS can introduce new risks. Therefore, the risk assessment process must be a continuous cycle of monitoring, reviewing, and updating.
Block Diagram: The Continuous IEC 62443 Risk Management Lifecycle
Regular reviews of the risk assessment should be scheduled to account for:
Changes in the threat landscape: New attack vectors and threat actors emerge constantly.
Discovery of new vulnerabilities: Software and hardware vulnerabilities are continuously being identified.
Changes to the IACS: Modifications to the control system, including the addition of new devices or changes to the network architecture, can introduce new risks.
Changes in business objectives: New business requirements may impact the criticality of certain assets and processes.
The Tangible Benefits of Embracing IEC 62443
Adopting the IEC 62443 framework for cybersecurity risk assessment offers a multitude of benefits for organizations operating industrial systems:
Improved Security Posture: By systematically identifying and mitigating risks, organizations can significantly reduce their attack surface and enhance the resilience of their IACS.
Enhanced Safety and Reliability: A robust cybersecurity program helps to protect against cyber incidents that could lead to safety hazards and operational disruptions.
Regulatory Compliance: In many industries, adherence to standards like IEC 62443 is becoming a regulatory requirement.
Informed Decision-Making: The risk assessment process provides valuable data to support informed decision-making regarding security investments.
Common Language and Framework: The standard provides a common language and a structured framework that facilitates communication and collaboration between all stakeholders, including asset owners, system integrators, and product suppliers.
Competitive Advantage: Demonstrating a commitment to cybersecurity through compliance with internationally recognized standards can be a significant competitive differentiator.
In conclusion, the cybersecurity risk assessment process as defined by IEC 62443 provides a comprehensive and defensible methodology for managing cyber risks in industrial environments. By embracing this structured approach, organizations can move beyond a reactive, compliance-driven mindset to a proactive, risk-based strategy that will fortify their critical systems against the ever-present and evolving cyber threats of the modern industrial landscape. The journey towards a secure and resilient IACS begins with a thorough and ongoing commitment to understanding and mitigating cyber risk.