The Future of Industrial Cybersecurity: How IEC 62443 is Evolving to Meet Tomorrow’s Threats
The convergence of Information Technology (IT) and Operational Technology (OT) is revolutionizing the industrial landscape. While this integration unlocks unprecedented efficiency and innovation, it also exposes critical infrastructure to a new and evolving wave of cyber threats. In this high-stakes environment, the International Electrotechnical Commission (IEC) 62443 series of standards has emerged as the global benchmark for securing Industrial Automation and Control Systems (IACS). This comprehensive framework provides a risk-based approach to cybersecurity, guiding asset owners, system integrators, and product suppliers in safeguarding their OT environments.
However, the relentless pace of technological advancement and the increasing sophistication of cyber adversaries mean that the standards themselves must constantly evolve. This blog post delves into the future trends shaping industrial cybersecurity and explores how the IEC 62443 standard is adapting to meet these challenges head-on. We’ll examine the impact of the Industrial Internet of Things (IIoT), Artificial Intelligence (AI), and cloud computing on OT security, and how upcoming changes to IEC 62443 will help organizations build a more resilient and secure industrial future.
The Shifting Landscape of Industrial Cybersecurity: Key Future Trends
The industrial sector is at a critical juncture, where the benefits of digital transformation are undeniable, but the associated cyber risks are equally significant. Several key trends are defining the future of industrial cybersecurity:
The Proliferation of the Industrial Internet of Things (IIoT)
The IIoT is connecting a vast and diverse array of sensors, actuators, and industrial devices to the internet. This hyper-connectivity enables real-time data collection, remote monitoring, and predictive maintenance, driving significant operational improvements. However, each connected device also represents a potential entry point for attackers. Many IIoT devices lack robust built-in security features, making them vulnerable to hijacking, data breaches, and manipulation that can have direct physical consequences. Securing these sprawling and heterogeneous networks is a primary challenge for the future of industrial cybersecurity.
The Rise of Artificial Intelligence and Machine Learning in Attack and Defense
Artificial Intelligence (AI) and Machine Learning (ML) are double-edged swords in the context of cybersecurity. On one hand, AI-powered tools are becoming indispensable for threat detection and response. They can analyze vast amounts of data from industrial networks to identify subtle anomalies and patterns that may indicate a sophisticated attack, enabling a more proactive and automated defense. On the other hand, adversaries are also leveraging AI to develop more intelligent and evasive malware, automate reconnaissance, and launch highly targeted attacks. The future of industrial cybersecurity will be characterized by an ongoing arms race between AI-driven attack and defense mechanisms.
The Convergence of IT and OT: A Double-Edged Sword
The historical air gap between IT and OT networks is rapidly disappearing. This convergence allows for seamless data exchange and integrated business and industrial processes. However, it also exposes OT systems, which were often designed with a focus on safety and reliability rather than security, to threats originating from the IT environment. Malware that infects a corporate network can now potentially propagate to the factory floor, with devastating consequences. Managing the security of these interconnected environments requires a holistic approach that bridges the cultural and technical divides between IT and OT security teams.
The Growing Sophistication of Cyber Threats and Threat Actors
The threat landscape for industrial organizations is becoming more complex and dangerous. Nation-state actors, organized cybercrime groups, and hacktivists are increasingly targeting critical infrastructure for espionage, sabotage, and financial gain. These threat actors are employing sophisticated tactics, techniques, and procedures (TTPs), including zero-day exploits, advanced persistent threats (APTs), and customized malware designed to manipulate industrial processes. The potential for physical damage, production downtime, and safety incidents makes these threats particularly concerning.
The Adoption of Cloud Computing in OT
Cloud platforms offer industrial organizations significant benefits, including scalability, cost-effectiveness, and advanced data analytics capabilities. However, migrating OT data and applications to the cloud introduces new security challenges. Organizations must ensure the secure transmission and storage of sensitive operational data, manage access controls effectively in a hybrid environment, and address compliance and data sovereignty requirements. Securing the connection between on-premises IACS and cloud services is crucial to prevent unauthorized access and data breaches.
The Evolution of IEC 62443: Adapting to the Future
The IEC 62443 standard is not a static document; it is a living framework that is continuously updated to address the evolving challenges of industrial cybersecurity. The committees responsible for the standard are actively working to incorporate guidance and requirements that help organizations navigate the trends discussed above. Here’s how IEC 62443 is evolving:
A Stronger Focus on the Entire Lifecycle and Supply Chain Security
Recent and upcoming updates to the IEC 62443 series place a greater emphasis on a holistic, lifecycle approach to security. This begins with the secure design and development of IACS products and extends through integration, operation, maintenance, and decommissioning.
A key development in this area is the increased focus on supply chain security. The standard now advocates for the use of a Software Bill of Materials (SBOM), which provides a detailed inventory of all software components within a product. This transparency is critical for identifying and mitigating vulnerabilities in third-party and open-source software, a common attack vector. IEC 62443-4-1 (Secure product development lifecycle requirements) and IEC 62443-4-2 (Technical security requirements for IACS components) are central to this effort, pushing manufacturers to build security in from the start.
Enhanced Guidance for IT/OT Convergence and Network Segmentation
Recognizing the risks associated with IT/OT convergence, IEC 62443 provides a robust framework for network segmentation based on the concept of zones and conduits. This model involves grouping assets with similar security requirements into zones and controlling the communication between these zones through defined conduits. This layered approach helps to contain threats and prevent them from spreading across the industrial network.
Upcoming revisions to the standard are expected to provide even more granular guidance on micro-segmentation and the implementation of Zero Trust principles within OT environments. This means moving away from a perimeter-based security model to one where every user and device must be authenticated and authorized before accessing any resource, regardless of their location on the network.
Block Diagram 1: Layered Security with Zones and Conduits in IEC 62443
Integrating IIoT Security within the IEC 62443 Framework
While the IEC 62443 series was initially developed before the widespread adoption of IIoT, its principles are highly applicable to securing these connected environments. The standard’s risk-based approach allows organizations to assess the vulnerabilities of their IIoT devices and implement appropriate security controls.
Future developments in the standard are likely to include more specific guidance on securing IIoT devices, protocols, and data. This may involve recommendations for secure device onboarding, over-the-air updates, and the use of lightweight cryptographic algorithms suitable for resource-constrained devices. The goal is to provide a clear roadmap for extending the proven security concepts of IEC 62443 to the unique challenges of the Industrial Internet of Things.
Block Diagram 2: Secure IIoT Architecture based on IEC 62443
Embracing Automation and AI for Enhanced Defense
The IEC 62443 framework encourages the use of advanced security technologies to protect industrial environments. As AI and ML become more integral to cybersecurity, the standard will likely evolve to provide guidance on their effective and secure implementation.
This could include recommendations for:
AI-powered anomaly detection systems that can identify malicious activity in real-time.
Automated incident response playbooks that can be triggered by AI-driven alerts.
Security Orchestration, Automation, and Response (SOAR) platforms that can help to streamline security operations in OT environments.
The key will be to leverage the power of automation and AI to augment the capabilities of human security professionals, enabling them to respond more quickly and effectively to threats.
Block Diagram 3: AI in Industrial Threat Detection
Refining Risk Management and Introducing Maturity Models
A cornerstone of the IEC 62443 series is its emphasis on a risk-based approach. IEC 62443-3-2 (Security risk assessment for system design) provides a detailed methodology for identifying, analyzing, and evaluating risks to the IACS.
Recent updates, particularly to IEC 62443-2-1, have introduced the concept of Security Program Elements (SPEs) and maturity levels. This evolution provides a more structured and measurable way for asset owners to implement and assess the effectiveness of their cybersecurity management systems. The maturity model allows organizations to benchmark their security posture and identify areas for continuous improvement, moving from an ad-hoc approach to a more optimized and resilient security program.
Block Diagram 4: Evolution of Industrial Security Posture with IEC 62443
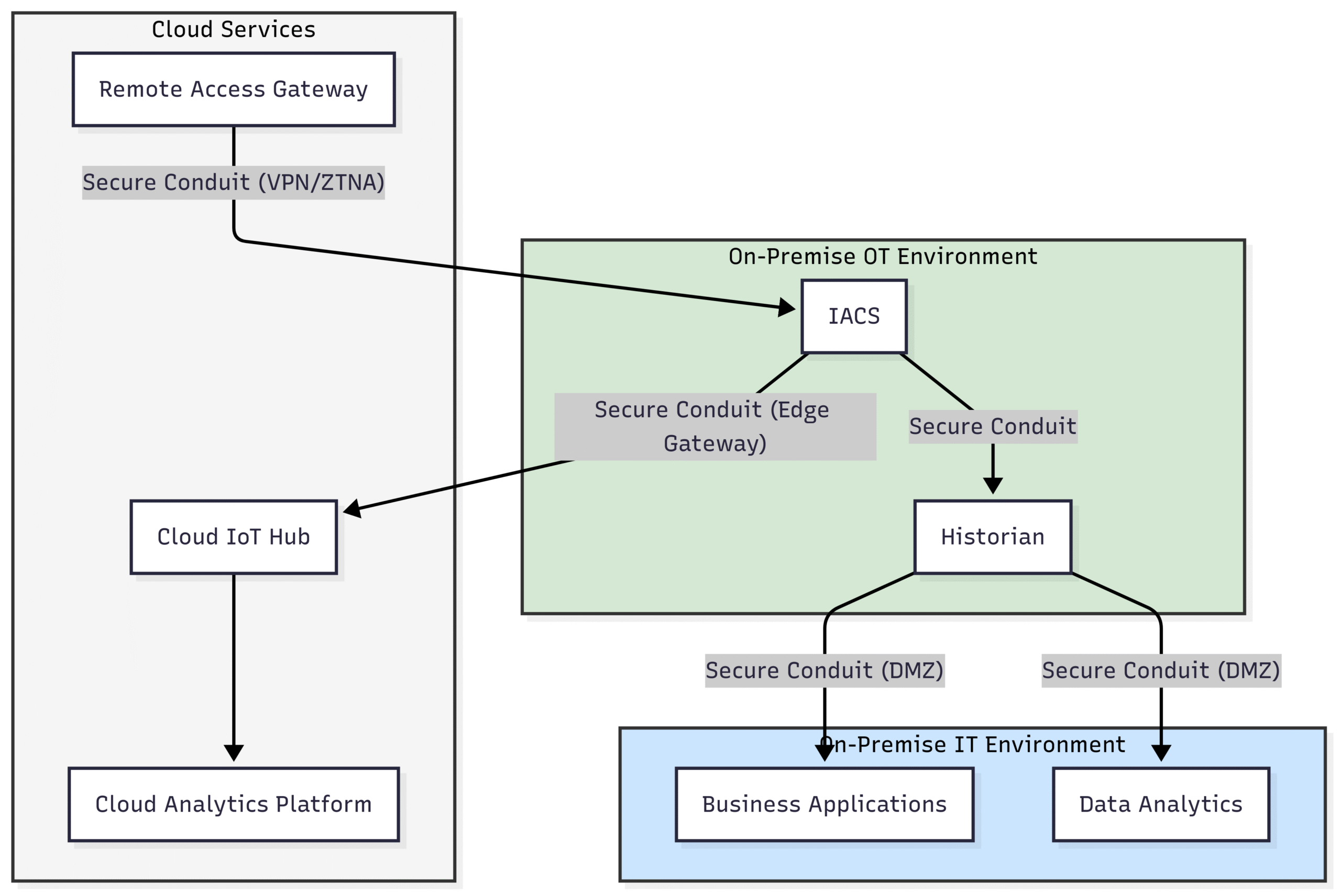
Addressing the Security of Cloud-Connected OT
As industrial organizations increasingly leverage cloud services, the IEC 62443 standard is adapting to provide guidance on securing these hybrid environments. While the standard doesn’t explicitly detail cloud security controls, its fundamental principles of risk assessment, access control, and data protection are directly applicable.
Future iterations of the standard will likely incorporate more specific recommendations for:
Securely connecting OT networks to the cloud.
Managing identity and access in hybrid cloud environments.
Protecting OT data both in transit and at rest in the cloud.
Ensuring compliance with relevant regulations and data privacy laws.
The goal is to provide a comprehensive framework that enables organizations to take advantage of the benefits of the cloud without compromising the security and integrity of their industrial operations.
Block Diagram 5: Secure IT/OT and Cloud Integration
The Path Forward: Embracing a Proactive and Evolving Security Posture
The future of industrial cybersecurity is one of constant change and adaptation. The trends of IIoT, AI, IT/OT convergence, and cloud computing will continue to reshape the industrial landscape, introducing new opportunities and new risks. The IEC 62443 standard is evolving in lockstep with these changes, providing a robust and flexible framework for securing the critical infrastructure that underpins our modern world.
For industrial organizations, the key to a secure future lies in embracing a proactive and risk-based approach to cybersecurity. This means moving beyond a compliance-only mindset and embedding security into the culture, processes, and technologies of the organization. By leveraging the guidance of the IEC 62443 standard and staying abreast of its evolution, asset owners, system integrators, and product suppliers can build a resilient and secure industrial ecosystem that is prepared to meet the challenges of tomorrow. The journey to industrial cybersecurity is a continuous one, and the IEC 62443 standard provides an essential roadmap for navigating the path ahead.