How to Implement IEC 62443 in Your Control Systems
In the interconnected world of industrial automation, the security of your control systems is not just an IT issue; it’s a fundamental pillar of safety, reliability, and operational continuity. As our factories and critical infrastructure become smarter and more connected, they also become more vulnerable to cyber threats. The IEC 62443 series of standards provides a comprehensive framework for securing Industrial Automation and Control Systems (IACS). This blog post will guide you through the practical implementation of IEC 62443, complete with block diagrams to demystify the process and help you build a resilient fortress around your operations.
The “Why” Behind IEC 62443: More Than Just a Standard
Before diving into the “how,” it’s crucial to understand the “why.” A cyber incident in an operational technology (OT) environment can have catastrophic consequences, leading to production downtime, equipment damage, environmental incidents, and even risks to human life. IEC 62443 is not a one-size-fits-all solution but a flexible framework that helps organizations systematically manage and reduce cybersecurity risks in their IACS. It’s a globally recognized standard that provides a common language and a structured approach for all stakeholders, from asset owners and system integrators to product suppliers.
The Foundational Pillars of IEC 62443
At its core, IEC 62443 is built upon a set of foundational requirements (FRs) that form the bedrock of a secure IACS environment. These are:
Identification and Authentication Control (IAC): Ensuring that only authorized individuals and devices can access the system.
Use Control (UC): Restricting the actions that authenticated users can perform based on their roles and responsibilities.
System Integrity (SI): Protecting the integrity of the IACS from unauthorized modifications.
Data Confidentiality (DC): Preventing the unauthorized disclosure of information.
Restricted Data Flow (RDF): Controlling the flow of data between different parts of the system.
Timely Response to Events (TRE): Detecting and responding to security events in a timely manner.
Resource Availability (RA): Ensuring that the IACS is resilient to attacks and that critical functions remain available.
Understanding these foundational requirements is the first step toward building a robust cybersecurity posture for your control systems.
Your Roadmap to Implementation: A Step-by-Step Guide
Implementing IEC 62443 is a journey, not a destination. It’s a cyclical process of assessment, implementation, and continuous improvement. Here’s a breakdown of the key phases:
Phase 1: The Cybersecurity Risk Assessment – Know Your Vulnerabilities
The starting point of any effective cybersecurity strategy is a thorough understanding of your risks. The IEC 62443-3-2 standard outlines a two-part risk assessment process designed to identify and prioritize vulnerabilities in your IACS.
1. High-Level Risk Assessment: This initial phase aims to identify the highest-risk areas within your control systems. It involves: * Identifying the System Under Consideration (SuC): Clearly defining the scope of the assessment. * Grouping Assets: Logically grouping assets based on their function and criticality. * Initial Consequence Assessment: Determining the potential impact of a security breach on each asset group.
2. Detailed-Level Risk Assessment: Once the high-risk areas are identified, a more in-depth analysis is performed. This involves: * Threat Identification: Identifying potential threats to the system, both internal and external. * Vulnerability Analysis: Identifying weaknesses in the system that could be exploited by threats. * Likelihood and Impact Analysis: Assessing the likelihood of a threat exploiting a vulnerability and the potential impact of such an event. * Risk Determination: Combining the likelihood and impact to determine the overall level of risk.
The output of this phase is a prioritized list of risks that need to be addressed.
Block Diagram: The IEC 62443 Risk Assessment Process

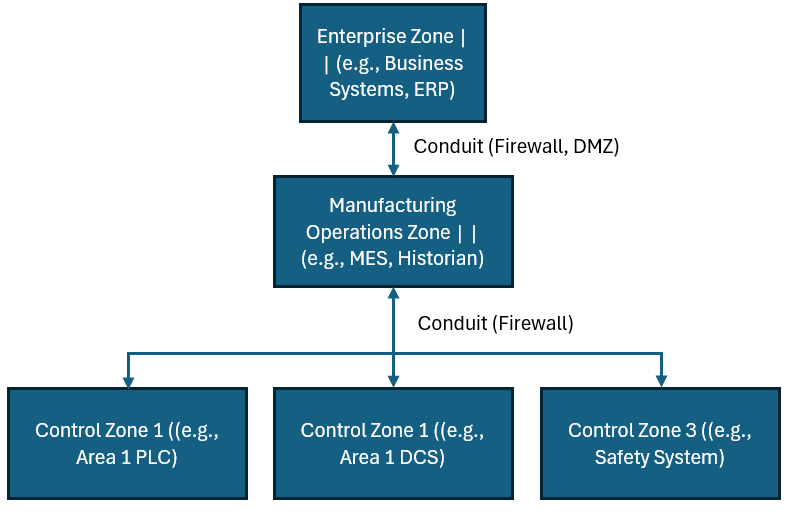
Phase 2: Segmentation is Key – Introducing Zones and Conduits
One of the most powerful concepts in IEC 62443 is the segmentation of the IACS into zones and conduits. This “divide and conquer” approach helps to contain security incidents and prevent them from spreading across your entire network.
Zones: A zone is a logical or physical grouping of assets that share common security requirements. For example, all the programmable logic controllers (PLCs) in a specific manufacturing line could be grouped into a single zone.
Conduits: A conduit is the communication channel that connects two or more zones. All communication between zones must pass through a conduit, which acts as a security gateway where you can enforce security policies.
By segmenting your network into zones and conduits, you can apply targeted security controls where they are needed most, creating a more manageable and defensible architecture.
Block Diagram: A Segmented IACS Architecture with Zones and Conduits
Phase 3: Defining Your Target – Security Levels (SLs)
Not all systems require the same level of security. IEC 62443 introduces the concept of Security Levels (SLs) to define the required level of protection for each zone and conduit. There are five security levels:
SL 0: No specific security requirements.
SL 1: Protection against casual or coincidental violations.
SL 2: Protection against intentional violation by simple means with low resources, generic skills, and low motivation.
SL 3: Protection against intentional violation by sophisticated means with moderate resources, IACS-specific skills, and moderate motivation.
SL 4: Protection against intentional violation by sophisticated means with extended resources, IACS-specific skills, and high motivation.
During the risk assessment, you will determine the Target Security Level (SL-T) for each zone and conduit. This is the level of security you aim to achieve. You will then assess your current security posture to determine the Achieved Security Level (SL-A). The gap between SL-T and SL-A will drive your security implementation and improvement efforts.
Phase 4: The Implementation Lifecycle – A Continuous Journey
Implementing the necessary security controls to bridge the gap between your achieved and target security levels is an ongoing process. The IEC 62443 implementation lifecycle provides a structured approach to this continuous improvement journey.
Block Diagram: The IEC 62443 Implementation Lifecycle
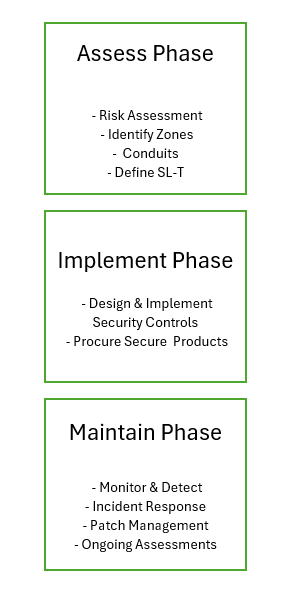
This lifecycle emphasizes that cybersecurity is not a one-time project but a continuous program that requires ongoing attention and resources.
The Human Element: Culture and Training
Technology alone cannot secure your control systems. A strong cybersecurity culture is paramount. This includes:
Security Awareness Training: Educating all employees, from operators to engineers, about cybersecurity risks and their roles in protecting the IACS.
Clear Roles and Responsibilities: Defining who is responsible for what when it comes to cybersecurity.
Management Buy-in: Ensuring that senior management understands the importance of OT cybersecurity and provides the necessary resources and support.
Conclusion: Building a Resilient Future
Implementing IEC 62443 is a strategic imperative for any organization that relies on industrial automation and control systems. By taking a structured, risk-based approach, you can move from a reactive to a proactive cybersecurity posture. The journey may seem daunting, but by breaking it down into manageable phases – from risk assessment and segmentation to defining security levels and embracing a continuous improvement lifecycle – you can build a formidable defense for your critical operations. Remember, in the world of industrial cybersecurity, the best offense is a good, well-implemented defense. Start your IEC 62443 journey today and secure the future of your operations.
