IEC 62443 Certification for Your Process Plant: What You Need to Know
In the intricate and often hazardous environment of a process plant, the seamless and secure operation of Industrial Automation and Control Systems (IACS) is not just a matter of efficiency, but of paramount safety. As these systems become increasingly interconnected with broader enterprise networks and the Industrial Internet of Things (IIoT), their vulnerability to cyber threats grows exponentially. This is where the IEC 62443 series of standards emerges as a critical framework for safeguarding your operational technology (OT). This comprehensive guide will walk you through everything you need to know about achieving IEC 62443 certification for your process plant, from understanding its core principles to the practical steps for implementation and the tangible benefits it delivers.
What is IEC 62443? A Blueprint for Industrial Cybersecurity
At its core, IEC 62443 is an international series of standards that provides a systematic and risk-based approach to cybersecurity for IACS. Developed by a global community of experts from the International Electrotechnical Commission (IEC) and the International Society of Automation (ISA), it addresses the security of the entire industrial ecosystem, encompassing people, processes, and technology. Unlike general IT security standards, IEC 62443 is specifically tailored to the unique requirements and challenges of the OT environment, where system availability and safety are the foremost priorities.
The standard is structured into four main categories, each addressing a different aspect of industrial cybersecurity:
General: This section lays the groundwork, defining fundamental concepts, terminology, and models.
Policies and Procedures: Here, the focus is on the human element and organizational aspects, including the establishment of a robust Cybersecurity Management System (CSMS).
System: This part provides detailed guidance on the design and implementation of secure IACS architectures, including the crucial concepts of zones and conduits.
Components: This final section specifies the security requirements for the individual products and components that make up the IACS, such as PLCs, sensors, and network devices.
By adopting this holistic approach, IEC 62443 provides a comprehensive framework for mitigating cyber risks throughout the entire lifecycle of a process plant, from initial design and commissioning to ongoing operation and maintenance.
The Tangible Benefits of IEC 62443 Certification for Your Process Plant
Pursuing and achieving IEC 62443 certification is a significant undertaking, but the return on investment extends far beyond a mere certificate on the wall. For process plants, the benefits are both immediate and long-term, impacting safety, efficiency, and market reputation.
Enhanced Safety and Reduced Risk: This is arguably the most critical benefit. By implementing the robust security controls mandated by IEC 62443, you significantly reduce the likelihood of a cyber incident that could lead to a process upset, an environmental release, or even a catastrophic failure. A secure plant is a safe plant.
Improved Operational Resilience: Cyberattacks can bring production to a grinding halt, resulting in substantial financial losses. IEC 62443 helps you build a more resilient IACS that can better withstand and recover from cyber incidents, ensuring operational continuity.
Regulatory Compliance and Due Diligence: In an era of increasing regulatory scrutiny, demonstrating a commitment to cybersecurity is essential. IEC 62443 certification provides tangible proof that you are adhering to internationally recognized best practices, which can be invaluable in the event of an audit or incident.
Stronger Supply Chain Security: The standard doesn’t just focus on your plant; it also addresses the security of the products and services you procure. By requiring your vendors to adhere to IEC 62443, you can build a more secure and trustworthy supply chain.
Increased Stakeholder Confidence: Certification sends a powerful message to your customers, investors, insurers, and the public that you take cybersecurity seriously. This can enhance your brand reputation and provide a competitive advantage in the marketplace.
A Common Language for Cybersecurity: IEC 62443 establishes a standardized language and framework for discussing and managing industrial cybersecurity. This facilitates better communication and collaboration between your internal teams (OT and IT), as well as with external partners and vendors.
Your Roadmap to IEC 62443 Certification: A Step-by-Step Guide
Embarking on the journey to IEC 62443 certification requires a structured and methodical approach. Here’s a step-by-step guide to help you navigate the process:
Step 1: Scoping and Gap Analysis
The first step is to clearly define the scope of your certification effort. This involves identifying the specific IACS or “System Under Consideration” (SuC) that will be assessed. Once the scope is defined, a thorough gap analysis should be conducted to compare your current cybersecurity posture against the requirements of the relevant IEC 62443 standards. This will highlight areas of non-compliance and help you prioritize your remediation efforts.
Step 2: Risk Assessment
A cornerstone of IEC 62443 is the concept of a risk-based approach. You will need to conduct a detailed risk assessment to identify and analyze the potential cyber threats to your IACS. This involves:
Identifying critical assets: Determine which systems and components are most critical to the safety and operation of your plant.
Analyzing vulnerabilities: Identify weaknesses in your systems, networks, and procedures that could be exploited by an attacker.
Evaluating potential impacts: Assess the potential consequences of a successful cyberattack, including safety, environmental, financial, and reputational impacts.
The results of this risk assessment will inform the selection of appropriate security controls and the determination of target Security Levels.
Step 3: Implementation of Security Controls
Based on the findings of your gap analysis and risk assessment, you will need to implement a range of technical and procedural security controls. These may include:
Network Segmentation: Dividing your IACS into distinct zones and controlling the flow of data between them using conduits.
Access Control: Implementing strong authentication and authorization mechanisms to ensure that only authorized personnel can access critical systems.
System Hardening: Disabling unnecessary services and ports, and configuring systems to be more resilient to attack.
Patch Management: Establishing a process for testing and deploying security patches in a timely manner.
Incident Response Planning: Developing a comprehensive plan for detecting, responding to, and recovering from a cyber incident.
Step 4: Development of a Cybersecurity Management System (CSMS)
IEC 62443-2-1 requires the establishment of a formal Cybersecurity Management System (CSMS). This is a set of policies, procedures, and processes for managing cybersecurity on an ongoing basis. Your CSMS should address key areas such as:
Cybersecurity policy and governance
Risk management
Security awareness training
Change management
Backup and recovery
Step 5: Internal and External Audits
Once you have implemented the necessary security controls and established your CSMS, you will need to conduct internal audits to verify their effectiveness. Following a successful internal audit, you can engage an accredited third-party certification body to conduct the formal certification audit.
Step 6: Certification and Continuous Improvement
If the certification body determines that your IACS and CSMS meet the requirements of the IEC 62443 standard, you will be awarded certification. However, the journey doesn’t end there. Cybersecurity is an ongoing process, and you will need to continuously monitor your systems, review your risks, and improve your security controls to maintain your certification and stay ahead of evolving threats.
Visualizing Security: Block Diagrams for Your Process Plant
Block diagrams are an invaluable tool for understanding and implementing the concepts of IEC 62443. Here are two illustrative diagrams for a typical process plant:
Block Diagram 1: The Purdue Model and IEC 62443 Zoning
This diagram shows how the Purdue Model for control hierarchy can be mapped to the zoning concepts of IEC 62443. This provides a clear framework for segmenting your IACS and controlling data flows between different levels of the plant architecture.
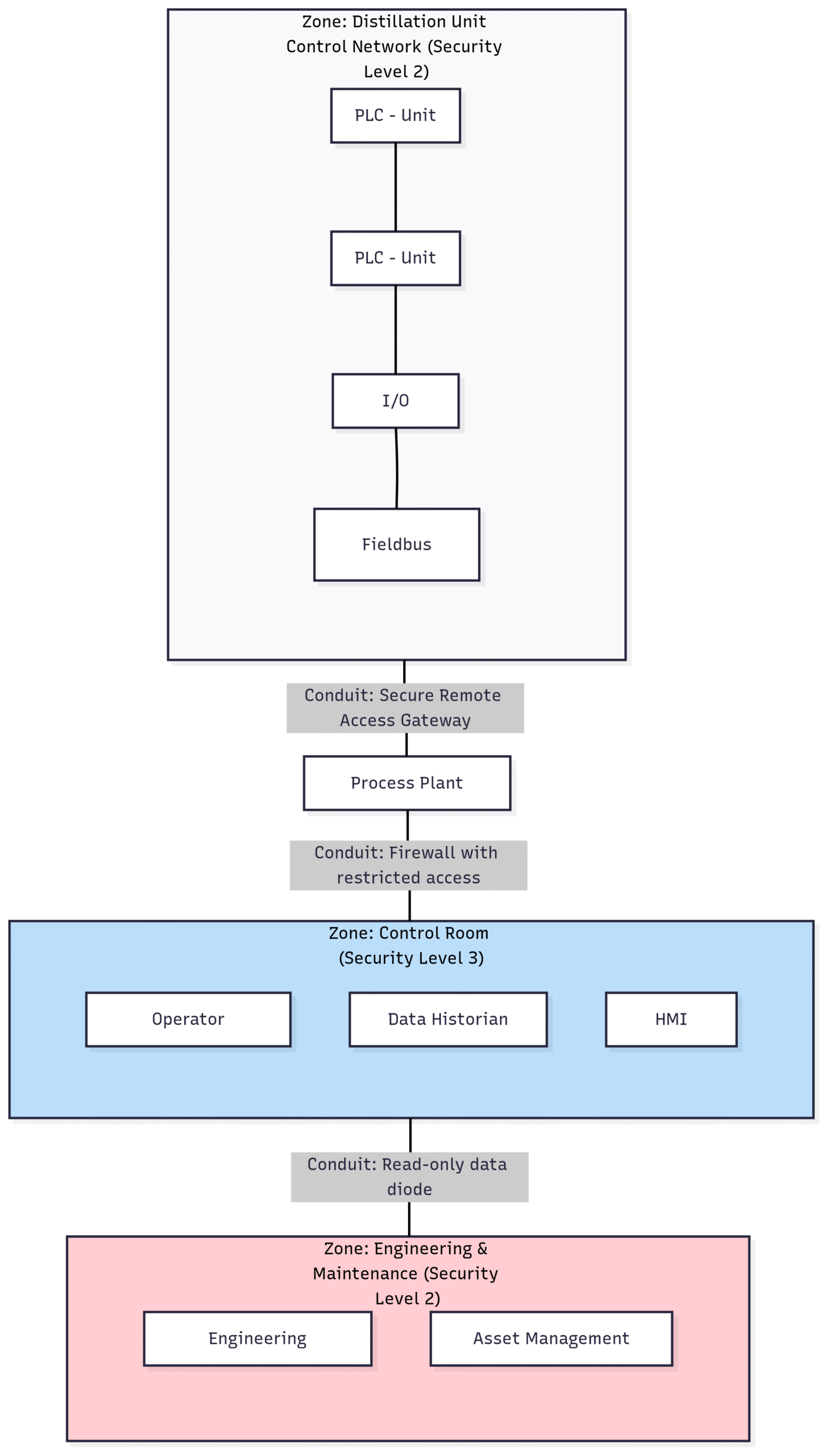
Block Diagram 2: A Deeper Dive into Zones and Conduits
This diagram provides a more detailed view of how zones and conduits can be implemented within a specific area of a process plant, such as a distillation unit.
Demystifying the Costs of IEC 62443 Certification
The cost of achieving IEC 62443 certification can vary significantly depending on a number of factors. It’s not a one-size-fits-all price tag. Here are the key elements that will influence your investment:
Scope and Complexity of the IACS: A large, complex, and highly interconnected process plant will naturally require a more extensive and therefore more costly certification effort than a smaller, more isolated system.
Current Cybersecurity Maturity: If you already have a mature cybersecurity program in place, the cost of achieving certification will be lower than if you are starting from scratch. The results of your initial gap analysis will be a key indicator of the level of investment required.
Chosen Certification Body: The fees charged by accredited certification bodies can vary. It’s essential to obtain quotes from several reputable organizations and compare their experience, expertise, and pricing.
Internal Resources: The extent to which you can leverage your internal resources will also impact the cost. If you have in-house expertise in OT cybersecurity, you may be able to reduce your reliance on external consultants.
Technology and Infrastructure Upgrades: The certification process may identify the need for new or upgraded security technologies, such as firewalls, intrusion detection systems, or secure remote access solutions. These capital expenditures should be factored into your overall budget.
Training and Awareness: Investing in cybersecurity training for your OT and IT staff is a critical component of IEC 62443 compliance. The cost of this training will depend on the number of employees and the depth of the curriculum.
While the initial investment may seem substantial, it’s important to view it as a long-term investment in the safety, reliability, and resilience of your process plant. The cost of a major cyber incident far outweighs the cost of proactive cybersecurity measures.
Choosing the Right Certification Body
Selecting the right certification body is a critical decision that can significantly impact the success of your IEC 62443 certification journey. Here are some key factors to consider when making your choice:
Accreditation: Ensure that the certification body is accredited by a recognized national or international accreditation body to perform IEC 62443 audits. This provides assurance that they have the necessary competence and impartiality.
Experience in the Process Industry: Look for a certification body with a proven track record of working with process plants and a deep understanding of the unique challenges of the OT environment.
Expertise of the Auditors: The auditors who will be assessing your systems should have extensive experience in both cybersecurity and industrial automation.
Reputation and Recognition: Choose a certification body with a strong reputation and whose certificates are widely recognized in the industry.
Collaborative Approach: Look for a partner who will work with you collaboratively throughout the certification process, providing guidance and support to help you achieve your goals.
By carefully evaluating these factors, you can select a certification body that is the right fit for your organization and will help you navigate the path to IEC 62443 certification with confidence.
In conclusion, IEC 62443 certification is no longer a “nice to have” for process plants; it’s a fundamental necessity for ensuring the safety, security, and reliability of your critical operations. By embracing this comprehensive framework, you can build a robust and resilient defense against the ever-evolving landscape of cyber threats, protecting your people, your plant, and your bottom line. The journey to certification may be challenging, but the rewards are immeasurable, providing a solid foundation for a secure and prosperous future.