IEC 62443 vs ISO 27001: Which Standard Should You Follow?
In today’s interconnected industrial landscape, cybersecurity is no longer a niche concern but a critical business imperative. As operational technology (OT) and information technology (IT) converge, industrial control systems have become increasingly vulnerable to cyber threats. To navigate this complex terrain, organizations rely on established standards to guide their cybersecurity efforts. Two of the most prominent standards in this domain are IEC 62443 and ISO 27001. While both aim to enhance security, they cater to different environments and serve distinct, albeit sometimes overlapping, purposes. This blog post will delve into a detailed comparison of IEC 62443 and ISO 27001, helping you determine which standard is the right fit for your organization.
Understanding the Fundamentals: A Tale of Two Standards
Before we pit these two standards against each other, it’s crucial to understand their individual scopes and objectives.
ISO 27001: The Guardian of Information
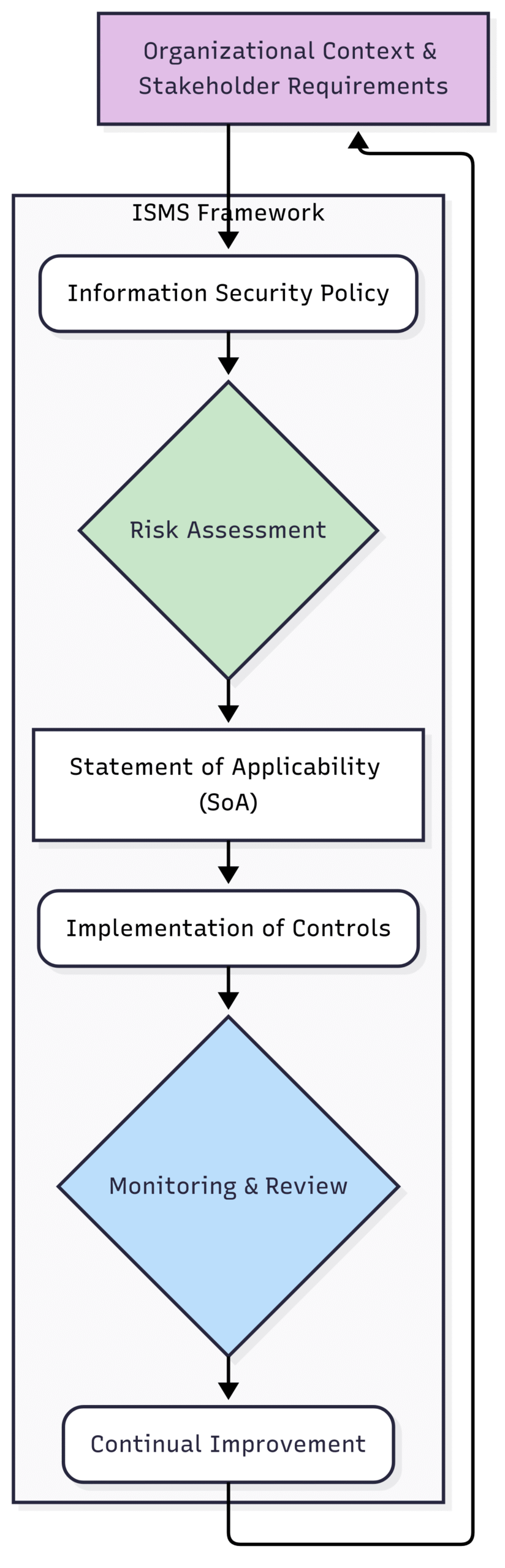
ISO/IEC 27001 is the international standard for an Information Security Management System (ISMS). Think of it as a comprehensive framework that provides a systematic approach to managing an organization’s information security risks. The primary goal of ISO 27001 is to protect the confidentiality, integrity, and availability (CIA) of information assets.
Key Characteristics of ISO 27001:
Broad Applicability: It’s a generic standard applicable to organizations of all sizes and in any industry.
Top-Down, Risk-Based Approach: It mandates a risk assessment process to identify and evaluate threats to information assets, followed by the implementation of appropriate controls to mitigate those risks.
Focus on the ISMS: The emphasis is on establishing, implementing, maintaining, and continually improving a documented ISMS.
Annex A Controls: It provides a list of 114 security controls in 14 domains that can be selected and implemented based on the organization’s risk assessment.
A Conceptual Look at ISO 27001:
A simplified block diagram illustrating the cyclical nature of the ISO 27001 ISMS.
IEC 62443: The Protector of Industrial Systems
The IEC 62443 series of standards is specifically designed for the security of Industrial Automation and Control Systems (IACS). This domain, often referred to as Operational Technology (OT), includes systems that monitor and control physical processes, such as those found in manufacturing plants, power grids, and water treatment facilities. The primary concern in OT environments is ensuring the safety, reliability, and availability of these critical processes.
Key Characteristics of IEC 62443:
Industry-Specific Focus: It is tailored to the unique requirements and risks of IACS environments.
Lifecycle Approach: The standard addresses security throughout the entire lifecycle of an IACS, from design and implementation to operation and maintenance.
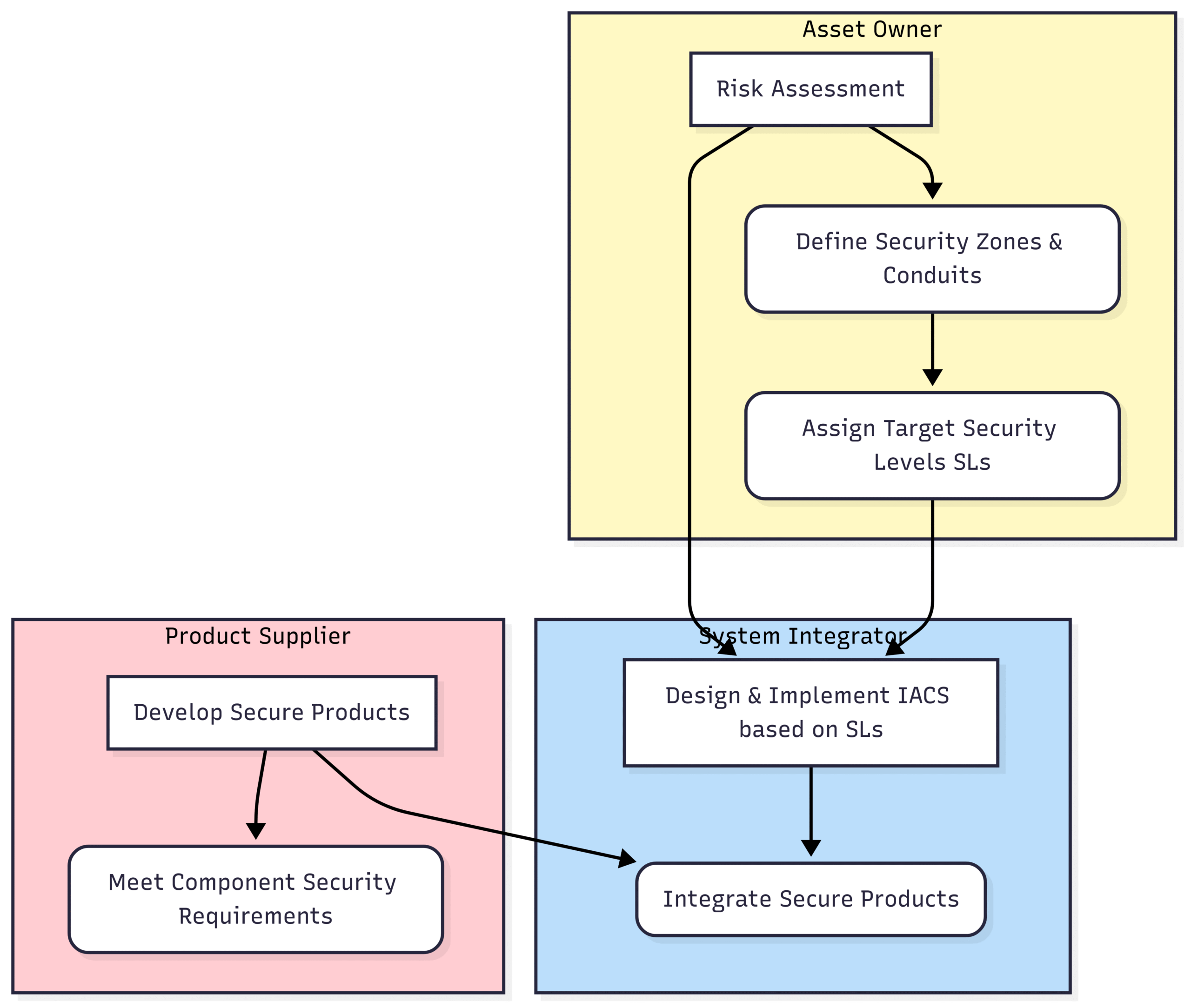
Role-Based Structure: It defines responsibilities for different stakeholders, including asset owners, system integrators, and product suppliers.
Zones and Conduits: A core concept is the segmentation of the IACS into zones with similar security requirements and the protection of communications between these zones through conduits.
Security Levels (SLs): IEC 62443 defines four security levels (SL 1 to SL 4) to specify the required security robustness for different zones based on risk.
A Conceptual Look at IEC 62443:
A simplified block diagram showing the role-based approach of IEC 62443 in securing an IACS.
Head-to-Head Comparison: ISO 27001 vs. IEC 62443
Now that we have a foundational understanding of both standards, let’s compare them directly across several key aspects.
Feature | ISO/IEC 27001 | IEC 62443 |
Primary Focus | Information Security (Confidentiality, Integrity, Availability) | Industrial Control System Security (Safety, Reliability, Availability) |
Scope | Generic and applicable to any organization’s IT environment. | Specific to Industrial Automation and Control Systems (IACS) in OT. |
Approach | Top-down, risk-based management system. | Lifecycle-based, with specific technical and process requirements. |
Key Concepts | Information Security Management System (ISMS), Statement of Applicability (SoA). | Zones, Conduits, Security Levels (SLs). |
Target Audience | Any organization managing information assets. | Asset Owners, System Integrators, Product Suppliers in industrial sectors. |
Priorities | Protecting data and information assets. | Ensuring the safe and continuous operation of physical processes. |
The Devil is in the Details: Key Differentiators
Risk Perspective: While both standards are risk-based, their perspectives differ significantly. ISO 27001’s risk assessment is geared towards the impact of a breach on the confidentiality, integrity, and availability of information. A data leak is a major incident. In contrast, IEC 62443’s risk assessment prioritizes the potential impact on physical safety, environmental damage, and the availability of the industrial process. A plant shutdown is the critical incident.
System Lifecycle: IEC 62443 places a strong emphasis on the entire lifecycle of the IACS, from initial design and procurement to decommissioning. It provides specific security requirements for product development and system integration. ISO 27001, while promoting continual improvement, does not delve into the specific lifecycle stages of the systems it protects in the same level of detail.
Prescriptiveness: ISO 27001 is more of a management framework, providing a set of controls in Annex A that an organization can choose from based on its risk assessment. It is less prescriptive about how to implement these controls. IEC 62443, particularly in its later parts, is more prescriptive, defining detailed technical requirements for IACS components and systems to achieve specific security levels.
Which Standard Should You Follow? The “It Depends” Answer
The answer to this crucial question is not a simple “one or the other.” In most modern industrial enterprises, the reality is that you will likely need both. The convergence of IT and OT means that a security incident in the corporate IT network can potentially cascade into the OT environment, and vice versa.
Here’s a guide to help you decide on the right approach for your organization:
When to Prioritize ISO 27001:
If your primary concern is the protection of sensitive corporate data, intellectual property, financial records, and customer information residing on your IT networks, then ISO 27001 is your starting point. It will help you establish a robust ISMS to manage these risks effectively. For many organizations, achieving ISO 27001 certification is also a key business enabler, demonstrating a commitment to information security to customers and partners.
When to Champion IEC 62443:
If your organization operates critical infrastructure, manufacturing facilities, or any environment where IACS are used to control physical processes, then IEC 62443 is non-negotiable. This standard provides the specific guidance needed to protect your OT environment from threats that could lead to production downtime, safety incidents, or environmental damage.
The Power of Integration: Using Both Standards Together
For a truly comprehensive and resilient cybersecurity posture, the most effective approach is to integrate ISO 27001 and IEC 62443. Here’s how they complement each other:
ISO 27001 as the Foundation: You can use ISO 27001 to establish a corporate-wide ISMS that governs all aspects of information security, including policies, procedures, and risk management. This provides a solid foundation and a common language for security across the organization.
IEC 62443 for the OT-Specifics: You can then leverage the specific requirements of IEC 62443 to address the unique challenges of your OT environment. The zones and conduits model of IEC 62443 can be integrated into your overall risk assessment, and the security levels can inform the technical controls you implement in your industrial networks.
A Unified Approach:
A simplified block diagram showing how ISO 27001 and IEC 62443 can be integrated for a holistic cybersecurity strategy.
By using ISO 27001 as the overarching framework and IEC 62443 to drill down into the specifics of your industrial control systems, you can create a defense-in-depth strategy that protects your entire enterprise, from the front office to the factory floor.
Conclusion: A Symbiotic Relationship for a Secure Future
In the ever-evolving landscape of industrial cybersecurity, the debate should not be “IEC 62443 vs. ISO 27001,” but rather “How can we best leverage both?” These two standards are not competitors; they are partners in the fight against cyber threats. ISO 27001 provides the strategic, high-level governance for information security, while IEC 62443 offers the tactical, in-depth guidance needed to secure the critical systems that underpin our modern industrial world. By understanding their individual strengths and their synergistic potential, organizations can build a robust, resilient, and future-proof cybersecurity program that protects both their information and their operations.