IEC 62443 Zones and Conduits: A Practical Approach to Segmentation
In the realm of Industrial Control Systems (ICS) and Operational Technology (OT), cybersecurity is no longer a niche concern but a critical business imperative. As industrial processes become increasingly interconnected, the attack surface for malicious actors expands, posing significant risks to safety, availability, and productivity. The IEC 62443 standard has emerged as the leading framework for securing these vital systems. At the heart of this standard lies the powerful concept of Zones and Conduits, a practical approach to network segmentation that can drastically improve the security posture of any industrial environment.
This in-depth guide will provide a comprehensive overview of IEC 62443 Zones and Conduits, moving beyond theoretical definitions to offer a practical, step-by-step approach to their implementation. We will explore the benefits, delve into the risk assessment process, and provide real-world examples and block diagrams to illustrate these critical concepts.
The Foundation: What Are Zones and Conduits?
Before diving into the practical application, it’s essential to have a solid understanding of the core components of this segmentation strategy.
Zones: Creating Logical Groupings of Assets
A Zone is a logical grouping of physical or logical assets that share common security requirements. Think of a zone as a designated neighborhood within your industrial network where all the “residents” (the assets) have similar security needs and trust levels. The assets within a zone can include:
Industrial Controllers: Programmable Logic Controllers (PLCs), Distributed Control Systems (DCS), and Remote Terminal Units (RTUs).
Human-Machine Interfaces (HMIs): The screens and panels operators use to interact with the control system.
Engineering Workstations: The computers used to program and maintain the control systems.
Historians: Servers that collect and store process data.
Servers and Applications: Any other computing resources that support the industrial process.
The primary goal of creating zones is to isolate critical assets from less critical ones and to group assets with similar security postures together. This follows the principle of “least privilege,” where assets only have the access and communication rights necessary for their function.
Key characteristics of a Zone include:
A clear boundary: This can be a physical boundary (e.g., a locked cabinet) or a logical boundary (e.g., a firewall rule set).
A defined set of assets: A comprehensive inventory of all hardware and software within the zone is crucial.
A specific Security Level (SL) target: Each zone is assigned a target Security Level based on a risk assessment.
Conduits: Securing the Pathways of Communication
A Conduit is a logical grouping of communication assets that connect two or more Zones and share the same security requirements. If Zones are the neighborhoods, Conduits are the secure highways that control the flow of traffic between them. They are not just passive data pipes; they are actively managed and secured communication channels.
A conduit can be a single network cable, a virtual local area network (VLAN), a wireless link, or a complex series of interconnected network devices. The critical aspect is that all communication passing through the conduit is subject to the same security policies.
Key characteristics of a Conduit include:
Defined endpoints: A conduit must connect specific zones.
A list of allowed communication protocols and services: Only authorized traffic should be permitted to traverse the conduit.
Security controls: These can include firewalls, VPNs, and other security mechanisms to protect the confidentiality, integrity, and availability of the data in transit.
A specific Security Level (SL) target: Like zones, conduits have their own security level targets determined by the security requirements of the zones they connect.
Visualizing Zones and Conduits: A Simple Block Diagram
To better understand the relationship between Zones and Conduits, let’s consider a simple block diagram:
Figure 1: A basic representation of Zones and Conduits.
In this diagram:
We have three distinct Zones: The “Corporate Network Zone,” the “DMZ (Demilitarized) Zone,” and the “Control Network Zone.” Each contains assets with different security requirements.
We have two Conduits that manage the communication between these zones.
Conduit_1controls the flow of information between the corporate and DMZ networks, whileConduit_2secures the connection between the DMZ and the critical control network.
The “Why”: Key Benefits of Implementing Zones and Conduits
Adopting a Zones and Conduits model is not just about compliance with a standard; it’s about fundamentally improving the resilience of your industrial operations. Here are some of the primary benefits:
Reduced Attack Surface: By segmenting the network, you limit the “blast radius” of a potential cyberattack. If one zone is compromised, the infection is less likely to spread to other, more critical zones.
Enhanced Security for Legacy Systems: Many industrial environments rely on older, legacy equipment that may not have modern security features. Placing these vulnerable assets in a protected zone with strict access controls can significantly mitigate their risk.
Improved Incident Response: In the event of a security incident, a well-defined zonal architecture allows for a more targeted and efficient response. You can quickly isolate the affected zone, preventing further damage while the rest of the plant continues to operate.
Clearer Security Policies: The process of defining Zones and Conduits forces you to think critically about your security requirements and to document them in a clear and understandable way. This leads to more consistent and effective security policies.
Simplified Compliance: For organizations subject to regulatory requirements, a segmented network based on IEC 62443 can make it much easier to demonstrate compliance with a variety of standards.
Facilitates a Defense-in-Depth Strategy: Zones and Conduits are a cornerstone of a defense-in-depth security strategy, creating multiple layers of defense that an attacker must overcome to reach critical assets.
The “How”: A Practical Step-by-Step Guide to Defining Zones and Conduits
Now, let’s move from the “what” and “why” to the “how.” Here is a practical, step-by-step approach to defining Zones and Conduits in your industrial environment.
Step 1: System Identification and Asset Inventory
You can’t protect what you don’t know you have. The first and most critical step is to conduct a thorough inventory of all the assets in your Industrial Automation and Control System (IACS). This includes:
Hardware: PLCs, RTUs, DCS controllers, HMIs, servers, workstations, network switches, firewalls, and any other physical devices.
Software: Firmware versions, operating systems, application software, and any custom scripts.
Network Information: IP addresses, MAC addresses, network protocols in use, and existing network diagrams.
This information can be gathered through a combination of physical inspections, network scanning tools (used with caution in an OT environment), and reviewing existing documentation.
Step 2: High-Level Risk Assessment
Once you have a comprehensive asset inventory, the next step is to perform a high-level risk assessment. The goal here is not to conduct an exhaustive analysis of every possible threat but to understand the general criticality of your assets and processes. For each system or area of your plant, ask questions like:
What is the impact of a failure or compromise of this system on safety, the environment, and production?
Are there any regulatory requirements associated with this system?
What is the likelihood of a security incident given the current controls (or lack thereof)?
This initial assessment will help you to identify the “crown jewels” of your industrial environment—the systems that require the highest level of protection.
Step 3: Grouping Assets into Initial Zones
Based on your asset inventory and high-level risk assessment, you can begin to group assets into initial zones. A good starting point is to consider the following logical groupings:
Functional Grouping: Group assets that perform a similar function together. For example, all the controllers and HMIs for a specific manufacturing line could form a zone.
Geographical Grouping: In some cases, it may make sense to create zones based on physical location, such as a specific building or area of the plant.
Security Level Grouping: Assets with similar security requirements should be placed in the same zone. For example, a zone for safety-instrumented systems (SIS) would have a very high security level.
Vendor Grouping: Sometimes, it’s practical to group assets from the same vendor, as they may share common vulnerabilities or management interfaces.
Step 4: Defining the Conduits
Once you have your initial zones, you need to identify the communication paths between them. For each connection between two zones, you will define a conduit. This involves:
Identifying the communication requirements: What data needs to be exchanged between these zones? What protocols are used?
Applying the principle of least privilege: Only allow the specific communication that is absolutely necessary for the process to function. Block all other traffic by default.
Specifying security controls: Determine what security measures need to be implemented within the conduit. This could include firewalls with specific rule sets, VPNs for encrypted communication, or data diodes for one-way data flow.
Step 5: Detailed Risk Assessment and Security Level (SL) Assignment
With your initial Zones and Conduits defined, you can now perform a more detailed risk assessment for each one. This process, as outlined in IEC 62443-3-2, involves:
Identifying threats and vulnerabilities specific to each zone and conduit.
Analyzing the potential impact of a successful attack.
Determining the required Security Level (SL) for each zone and conduit.
The IEC 62443 standard defines four Security Levels:
SL 1: Protection against casual or coincidental violation.
SL 2: Protection against intentional violation with low resources, generic skills, and low motivation.
SL 3: Protection against intentional violation with moderate resources, IACS-specific skills, and moderate motivation.
SL 4: Protection against intentional violation with extensive resources, IACS-specific skills, and high motivation.
The target SL for each zone and conduit will guide the selection and implementation of appropriate security controls.
Step 6: Implementation, Documentation, and Continuous Improvement
The final step is to implement the defined Zones and Conduits by configuring firewalls, network switches, and other security devices. It is crucial to thoroughly document your zonal architecture, including:
Detailed network diagrams showing the Zones and Conduits.
A complete asset inventory for each zone.
The security policies and rules for each conduit.
The assigned Security Levels for all Zones and Conduits.
Remember that cybersecurity is not a one-time project. Your industrial environment will change over time, and so will the threat landscape. Therefore, it’s essential to establish a process for regularly reviewing and updating your Zones and Conduits to ensure their continued effectiveness.
Real-World Examples and Block Diagrams
To bring these concepts to life, let’s explore some practical examples of how Zones and Conduits can be applied in different industrial settings.
Example 1: A Manufacturing Plant
Consider a typical manufacturing plant with an assembly line. We can segment this environment into the following Zones:
Figure 2: Zonal architecture for a manufacturing plant.
In this example:
The Corporate Network Zone (SL 2) contains the Enterprise Resource Planning (ERP) system, which has a lower security requirement than the plant floor systems.
The Plant DMZ Zone (SL 3) acts as a buffer between the corporate network and the control network. It houses the Manufacturing Execution System (MES) server, which needs to communicate with both environments.
The Assembly Line Zones (SL 3) are separated to contain any potential issues to a single line.
The Safety System Zone (SL 4) is the most critical and is highly isolated, with very strict communication controls.
The Conduits (A-E) enforce specific communication rules. For instance,
Conduit Amight only allow the MES server to pull production orders from the ERP system, whileConduits DandEwould only permit safety-related communication.
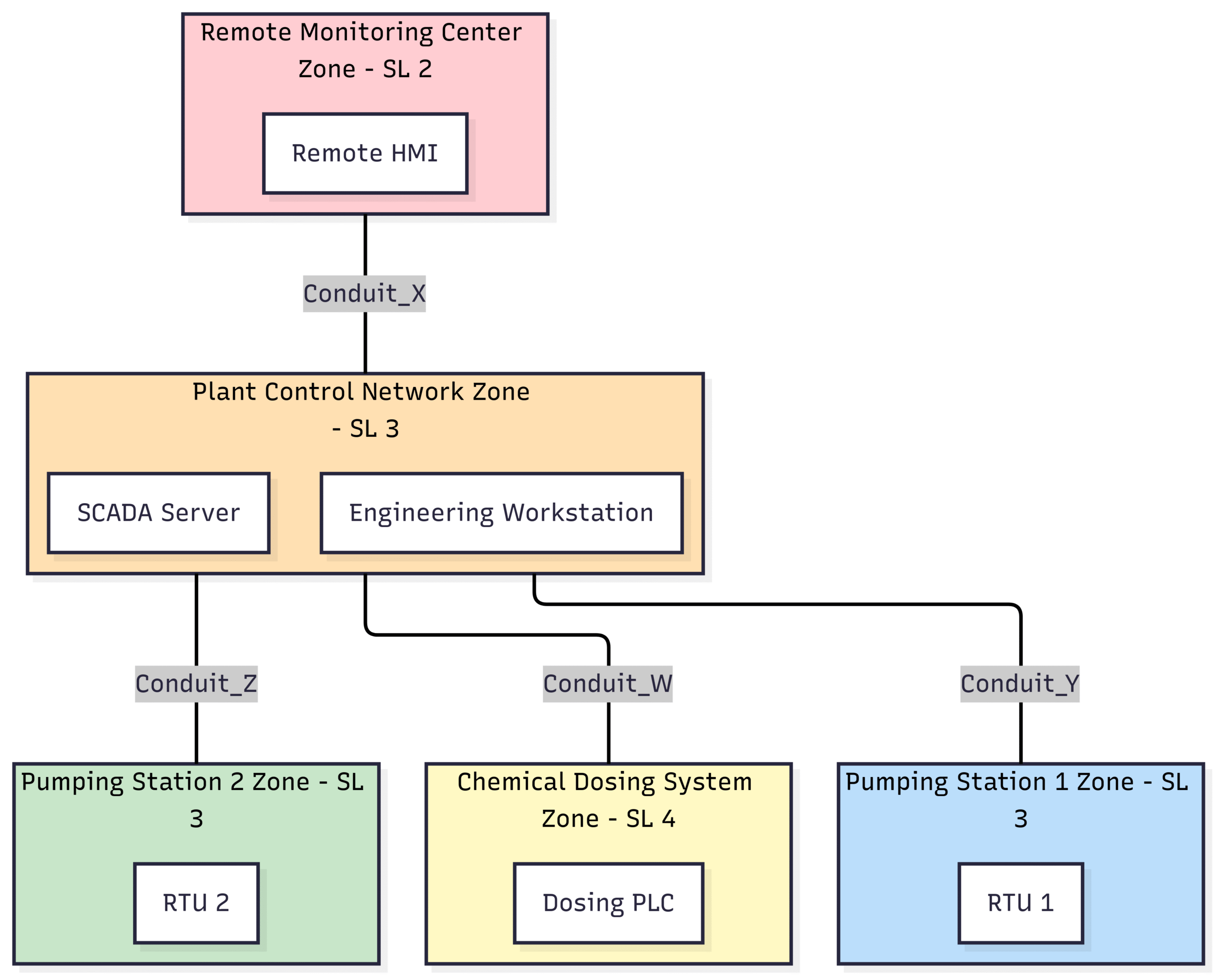
Example 2: A Water Treatment Facility
In a water treatment facility, the consequences of a cyberattack can be severe, making a robust zonal architecture essential.
Figure 3: Zonal architecture for a water treatment facility.
Here:
The Remote Monitoring Center Zone (SL 2) allows for off-site monitoring but with limited control capabilities.
The Plant Control Network Zone (SL 3) contains the central SCADA (Supervisory Control and Data Acquisition) system.
The Pumping Station Zones (SL 3) are segregated to prevent a single point of failure.
The Chemical Dosing System Zone (SL 4) is highly protected due to the critical nature of this process for water quality and public safety.
The Conduits (X, Y, Z, W) ensure that communication is strictly controlled. For example,
Conduit Xwould likely use a VPN to secure remote access, andConduit Wwould have very restrictive rules to prevent unauthorized changes to the chemical dosing process.
Modern Approaches: Microsegmentation and Software-Defined Networking
While traditional network segmentation using firewalls and VLANs is effective, modern approaches like microsegmentation and software-defined networking (SDN) can make implementing and managing Zones and Conduits even more efficient and granular.
Microsegmentation: Taking Granularity to the Next Level
Microsegmentation takes the concept of zones a step further by creating security segments around individual workloads or even individual assets. This allows for even finer-grained security policies and can be particularly useful in virtualized or cloud-based OT environments. With microsegmentation, you can create a “zone of one,” effectively isolating each critical asset.
Software-Defined Networking (SDN): Centralized Control and Automation
SDN decouples the network control plane from the data plane, allowing for centralized management and automation of network security policies. In the context of Zones and Conduits, SDN can:
Simplify policy management: Security policies can be defined and deployed from a central controller, rather than configuring individual firewalls and switches.
Enable dynamic segmentation: Security policies can be automatically updated in response to changes in the network or security events.
Improve visibility: SDN provides a centralized view of all network traffic, making it easier to monitor for and respond to threats.
Conclusion: A Journey, Not a Destination
Implementing a robust security architecture based on IEC 62443 Zones and Conduits is a journey, not a destination. It requires a commitment to a continuous process of risk assessment, implementation, and improvement. However, the benefits in terms of reduced risk, enhanced resilience, and improved operational stability are well worth the effort.
By taking a practical, step-by-step approach to defining and implementing Zones and Conduits, you can build a strong foundation for your OT cybersecurity program and protect your critical industrial processes from the ever-evolving landscape of cyber threats. Start today by taking the first step: understanding your assets and beginning the conversation about how to best segment your industrial network for a more secure and resilient future.