Industrial Control System (ICS) Cybersecurity: A Deep Dive into the IEC 62443 Standard
The convergence of Information Technology (IT) and Operational Technology (OT) has ushered in an era of unprecedented efficiency and connectivity for industrial processes. However, this integration has also exposed critical infrastructure to a new and evolving landscape of cyber threats. In this high-stakes environment, a reactive approach to cybersecurity is no longer sufficient. Proactive, comprehensive, and standardized measures are essential to safeguard the Industrial Control Systems (ICS) that form the backbone of modern industry. This is where the ISA/IEC 62443 series of standards emerges as the definitive global benchmark for securing Industrial Automation and Control Systems (IACS).
This blog post will provide an in-depth exploration of the IEC 62443 standard, offering a blueprint for organizations to establish a robust cybersecurity posture. We will delve into the foundational principles, core concepts like zones and conduits, the risk assessment process, and the philosophy of defense-in-depth, all illustrated with conceptual block diagrams to enhance understanding.
The Imperative for ICS Cybersecurity: Why a Specialized Approach is Crucial
Unlike traditional IT systems where confidentiality is often the primary concern, ICS environments prioritize availability and integrity. A cyber incident in an ICS can have far-reaching consequences, ranging from production downtime and financial losses to environmental damage and even loss of life. The unique characteristics of OT, such as legacy systems, proprietary protocols, and the paramount importance of real-time operation, necessitate a tailored cybersecurity framework.
The IEC 62443 standard was specifically developed to address these unique challenges. It provides a flexible and risk-based framework that can be applied across various industrial sectors, including manufacturing, energy, transportation, and water treatment. By adopting IEC 62443, organizations can move from a fragmented and often ad-hoc security approach to a structured and internationally recognized methodology.
Deconstructing IEC 62443: A Multi-Layered Framework
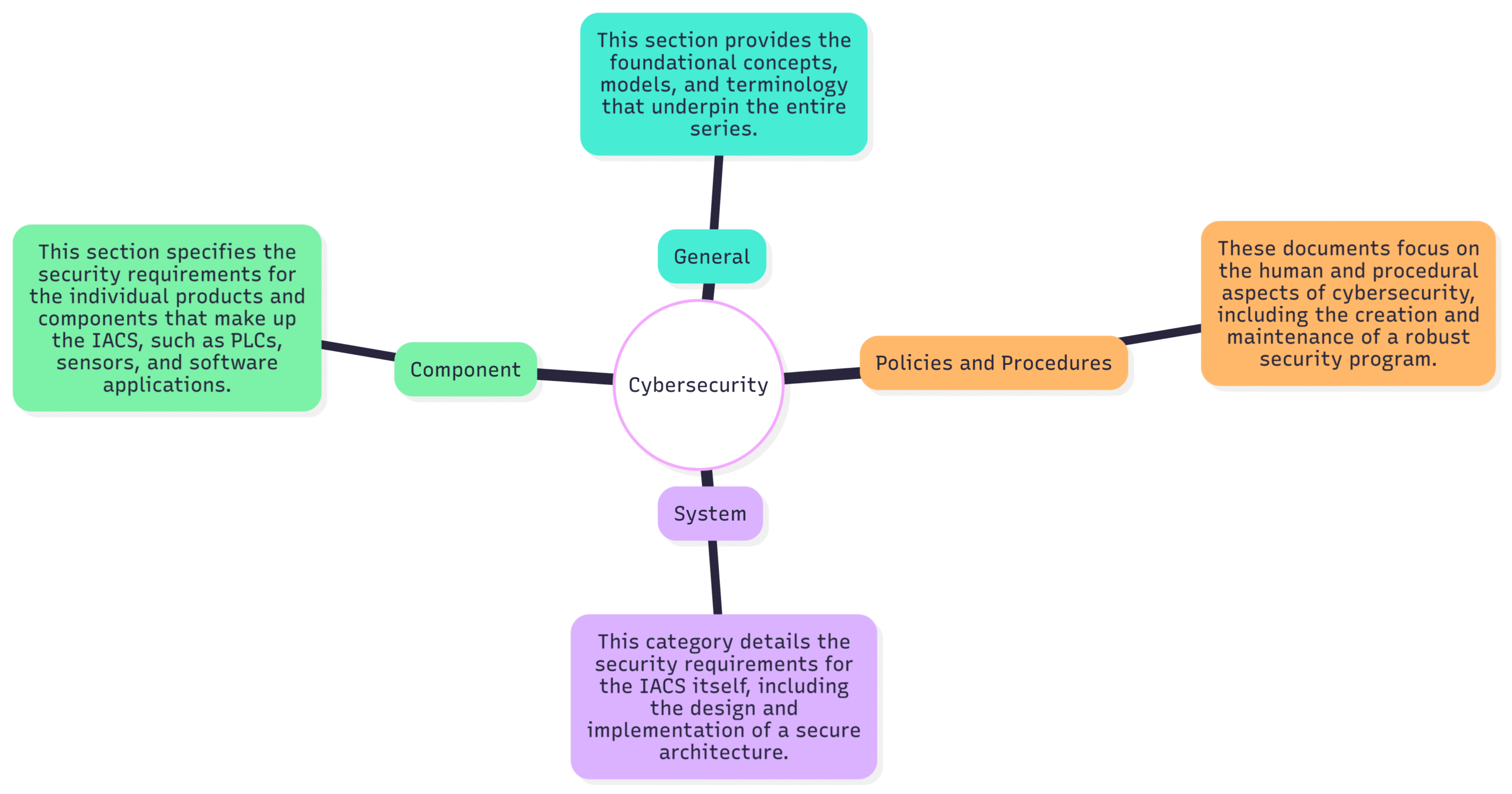
The IEC 62443 series is not a single document but a collection of standards organized into four main categories:
General: This section provides the foundational concepts, models, and terminology that underpin the entire series.
Policies and Procedures: These documents focus on the human and procedural aspects of cybersecurity, including the creation and maintenance of a robust security program.
System: This category details the security requirements for the IACS itself, including the design and implementation of a secure architecture.
Component: This section specifies the security requirements for the individual products and components that make up the IACS, such as PLCs, sensors, and software applications.
At the heart of the standard are seven Foundational Requirements (FRs) that provide a comprehensive framework for securing an IACS:
Identification and Authentication Control (IAC): Ensuring that all users and devices are uniquely identified and authenticated before being granted access to the system.
Use Control (UC): Enforcing the principle of least privilege, where users and devices are only granted the permissions necessary to perform their authorized functions.
System Integrity (SI): Protecting the integrity of the IACS from unauthorized modifications and ensuring that the system operates as intended.
Data Confidentiality (DC): Preventing the unauthorized disclosure of sensitive information, both at rest and in transit.
Restricted Data Flow (RDF): Controlling the flow of data between different parts of the IACS and with external networks.
Timely Response to Events (TRE): Detecting and responding to security incidents in a timely manner to minimize their impact.
Resource Availability (RA): Ensuring that the IACS and its resources are available when needed and can withstand denial-of-service attacks.
The Core Concepts: Zones, Conduits, and Security Levels
Two of the most critical concepts introduced by IEC 62443 for architecting a secure ICS environment are Zones and Conduits. This approach is fundamental to implementing a defense-in-depth strategy.
Zones: Creating Islands of Security
A zone is a logical or physical grouping of assets that share common security requirements. By segmenting the IACS into zones, organizations can isolate critical processes and apply targeted security controls. For example, a safety-instrumented system (SIS) would reside in a highly restricted zone with stringent access controls, while a less critical monitoring system might be in a separate zone with different security policies.
Block Diagram: Conceptual Representation of Zones and Conduits
Imagine a manufacturing plant network. A block diagram would depict different zones as distinct, enclosed areas:
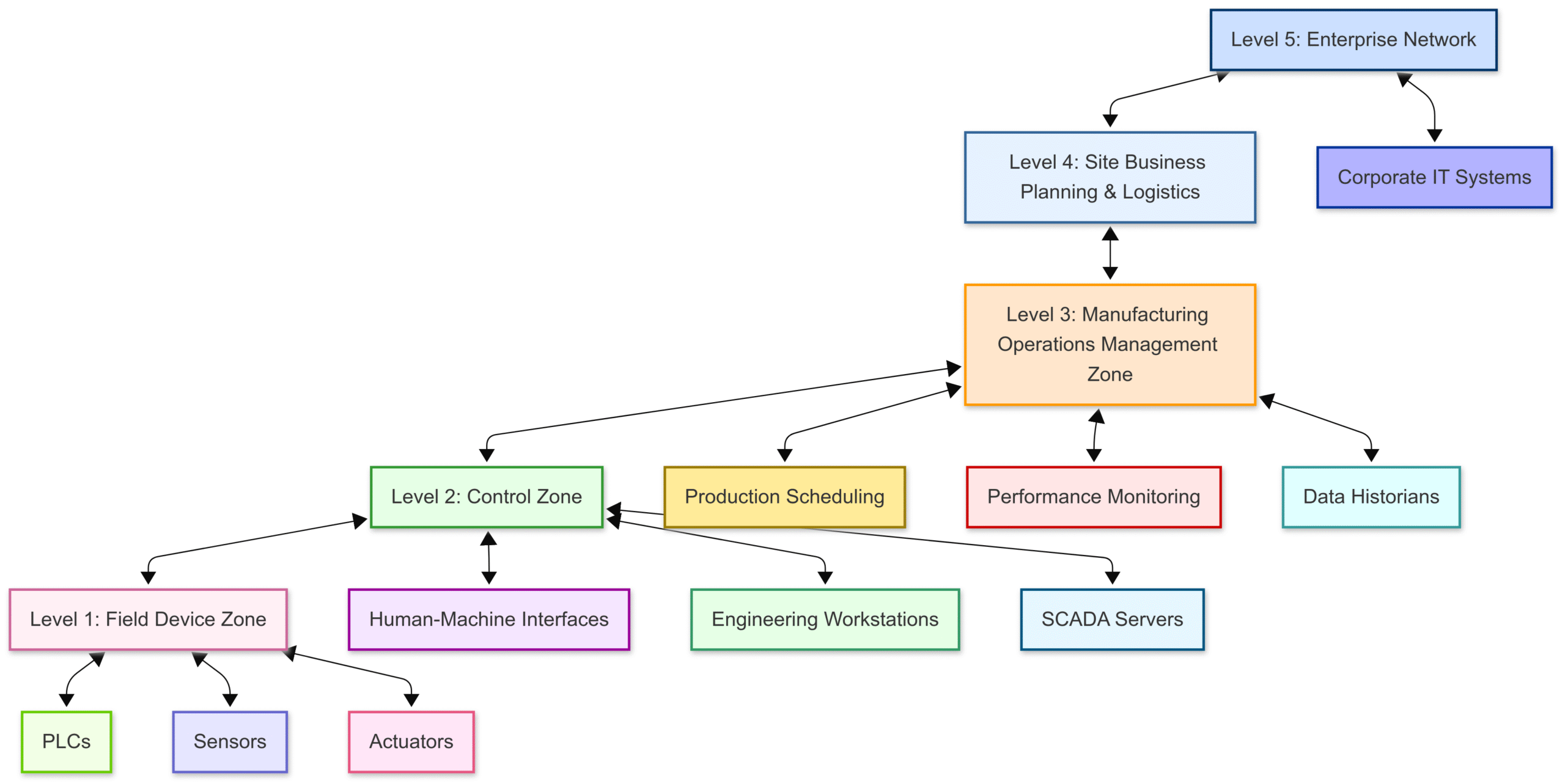
Enterprise Zone (Level 4/5): This would house the corporate IT systems, such as email servers and enterprise resource planning (ERP) systems.
Manufacturing Operations Management (MOM) Zone (Level 3): This zone contains systems for production scheduling, performance monitoring, and data historians.
Control Zone (Level 2): This critical zone includes the Human-Machine Interfaces (HMIs), engineering workstations, and SCADA servers that directly manage the industrial process.
Field Device Zone (Level 1/0): This is where the PLCs, sensors, and actuators that physically interact with the process reside.
Each of these zones would have a clearly defined boundary.
Conduits: The Controlled Pathways
A conduit is a communication channel that connects two or more zones. The key principle is that all communication between zones must pass through a conduit, which is secured and monitored. This prevents unrestricted data flow and allows for the enforcement of security policies at the zone boundaries. Firewalls, data diodes, and other security gateways are typically used to create and secure conduits.
In our block diagram, conduits would be represented as lines connecting the different zones. For instance, a firewall would act as a conduit between the Enterprise Zone and the MOM Zone, with specific rules dictating what traffic is allowed to pass. Another secured conduit would exist between the MOM Zone and the Control Zone. The goal is to minimize and control inter-zone communication, restricting it only to what is absolutely necessary for the process to function.
Security Levels (SLs): A Measure of Security Robustness
IEC 62443 defines four Security Levels (SLs) to specify the required security robustness for a zone or conduit. These levels are determined through a risk assessment and reflect the potential consequences of a security breach and the sophistication of the anticipated threats.
SL 1: Protection against casual or coincidental violation.
SL 2: Protection against intentional violation by individuals with simple means, low resources, generic skills, and low motivation.
SL 3: Protection against intentional violation by individuals with sophisticated means, moderate resources, ICS-specific skills, and moderate motivation.
SL 4: Protection against intentional violation by individuals with sophisticated means, extensive resources, ICS-specific skills, and high motivation.
By assigning a target SL to each zone, organizations can systematically implement the appropriate security controls to achieve the desired level of protection.
The IEC 62443 Risk Assessment: A Proactive Approach to Security
A cornerstone of the IEC 62443 framework is the risk assessment. This process helps organizations identify, analyze, and evaluate the cybersecurity risks to their IACS, enabling them to make informed decisions about where to focus their security efforts and resources. The risk assessment process typically involves the following steps:

System Identification and Scoping: Clearly defining the IACS to be assessed and its boundaries.
Asset Identification and Valuation: Identifying all the assets within the IACS (e.g., PLCs, HMIs, networks) and determining their value to the organization.
Threat Identification: Identifying potential threats to the IACS, both internal and external, malicious and accidental.
Vulnerability Identification: Identifying weaknesses in the IACS that could be exploited by threats.
Likelihood and Impact Analysis: Assessing the likelihood of each threat occurring and the potential impact it would have on the organization.
Risk Determination: Combining the likelihood and impact assessments to determine the overall level of risk.
Risk Treatment: Implementing security controls to mitigate the identified risks to an acceptable level.
Block Diagram: The IEC 62443 Risk Assessment Process
A block diagram illustrating this process would show a cyclical flow:
Input: System under consideration, asset inventory, threat intelligence.
Process Steps (in sequence):
High-Level Risk Assessment: An initial pass to identify the most critical assets and potential high-risk scenarios.
Partition into Zones & Conduits: Applying the architectural principles to segment the system.
Detailed Risk Assessment: A granular analysis of threats, vulnerabilities, likelihood, and impact for each zone and conduit.
Determine Target Security Levels: Assigning the appropriate SL to each zone based on the detailed risk assessment.
Output: A list of prioritized risks and a set of security requirements to be implemented.
Feedback Loop: The process is iterative, with the results of the risk assessment feeding back to inform and refine the security controls.
Defense-in-Depth: A Multi-Layered Security Philosophy
The concept of defense-in-depth is central to the IEC 62443 philosophy. It involves implementing multiple layers of security controls throughout the IACS architecture, so that if one layer is breached, subsequent layers are in place to detect and prevent the attack from progressing further.
Block Diagram: Defense-in-Depth in an ICS Environment
A defense-in-depth diagram would depict a series of concentric circles or layers, with the most critical assets at the core:
Outer Layer: Physical Security: Fences, locks, and access control systems to protect the physical environment.
Network Security: Firewalls, intrusion detection systems (IDS), and network segmentation to control access to the IACS network.
Host Security: Hardening of individual devices (e.g., disabling unused ports and services), application whitelisting, and anti-malware solutions.
Application Security: Secure coding practices, access controls within applications, and regular security testing.
Innermost Layer: Policies, Procedures, and Awareness: Security policies, incident response plans, and ongoing security awareness training for all personnel.
Each layer provides an additional barrier to an attacker, significantly reducing the likelihood of a successful compromise.
The Secure Development Lifecycle (SDL): Building Security In, Not Bolting It On
IEC 62443-4-1 specifically addresses the importance of a Secure Development Lifecycle (SDL) for IACS components. This means that security is considered at every stage of the product development process, from initial design and coding to testing and deployment. By adhering to an SDL, manufacturers can produce more resilient and secure products, reducing the number of vulnerabilities that could be exploited in the field. For asset owners, procuring products from vendors who follow a certified SDL provides a higher level of assurance about the security of their supply chain.
Benefits and Challenges of Implementing IEC 62443
Adopting the IEC 62443 standard offers numerous benefits:
Improved Security Posture: A systematic and comprehensive approach to managing cybersecurity risks.
Enhanced Reliability and Availability: Reduced risk of downtime and operational disruptions due to cyber incidents.
Regulatory Compliance: A clear framework for meeting regulatory requirements for critical infrastructure protection.
Increased Stakeholder Confidence: Demonstrates a commitment to cybersecurity to customers, partners, and insurers.
Common Language: Provides a common language and framework for all stakeholders, from asset owners and system integrators to product vendors.
However, implementing IEC 62443 is not without its challenges:
Complexity: The standard is comprehensive and can be complex to understand and implement.
Resource Intensive: Requires significant investment in terms of time, money, and skilled personnel.
Legacy Systems: Applying the standard to older, legacy systems can be difficult and costly.
Cultural Change: Requires a shift in mindset from a purely operational focus to one that embraces cybersecurity as an integral part of operations.
The Journey to a Secure Future
The journey to securing industrial control systems is a continuous process, not a one-time project. The threat landscape is constantly evolving, and so too must our defenses. The IEC 62443 standard provides a robust and adaptable roadmap for this journey. By embracing its principles of risk management, defense-in-depth, and a lifecycle approach to security, organizations can build a resilient and secure foundation for their industrial operations, ensuring the safety, reliability, and integrity of our critical infrastructure for years to come. The initial investment in time and resources will be far outweighed by the long-term benefits of a secure and resilient industrial enterprise.
