The digital and physical worlds are no longer distant neighbors; they are rapidly merging into a single, interconnected ecosystem. This convergence of Information Technology (IT) and Operational Technology (OT) is revolutionizing industries, unlocking unprecedented efficiencies, and fueling innovation. However, this powerful union also exposes critical infrastructure to a new and evolving landscape of cyber threats. In this era of heightened risk, the IEC 62443 series of standards emerges as the definitive roadmap for securing industrial automation and control systems (IACS). This comprehensive guide delves into the transformative role of IEC 62443 in navigating the complexities of OT/IT convergence, ensuring a secure and resilient future for our most vital industries.
The chasm that once separated the corporate network from the factory floor is rapidly closing. Driven by the promise of data-driven decision-making, predictive maintenance, and enhanced productivity, organizations are increasingly integrating their IT and OT systems. This convergence, however, creates a fertile ground for cyber adversaries who can now potentially move laterally from a compromised email account to the very heart of an industrial process. The consequences of such a breach can be catastrophic, ranging from production downtime and financial losses to environmental damage and even loss of life.
This is where the IEC 62443 standard comes into play. It is not merely a set of technical controls but a holistic framework designed to address the unique security challenges of the converged OT/IT landscape. By providing a common language and a structured approach, IEC 62443 empowers organizations to build a robust and defensible security posture for their critical operations.
The Great Divide No More: Understanding OT/IT Convergence
Traditionally, IT and OT have operated in separate spheres, each with its own distinct priorities, protocols, and risk perceptions.
Information Technology (IT) has long been the domain of data confidentiality, integrity, and availability. The primary focus is on protecting information from unauthorized access, modification, or deletion. Think of corporate networks, email servers, and enterprise resource planning (ERP) systems.
Operational Technology (OT), on the other hand, has been the bedrock of industrial processes, prioritizing safety, reliability, and availability. The core mission is to ensure the continuous and safe operation of physical equipment like programmable logic controllers (PLCs), distributed control systems (DCS), and supervisory control and data acquisition (SCADA) systems.
The convergence of these two worlds means that the air-gapped, isolated nature of OT systems is becoming a relic of the past. The same network infrastructure may now carry both corporate emails and critical commands to industrial machinery. This integration, while offering significant business benefits, introduces a host of new security vulnerabilities.
The Perils of Unsecured Convergence:
Expanded Attack Surface: Every new connection point between IT and OT networks becomes a potential entry point for attackers.
Differing Security Priorities: The IT focus on confidentiality can sometimes conflict with the OT requirement for uninterrupted availability, leading to security gaps.
Legacy Systems: Many OT systems were designed for long operational lifecycles and may lack modern security features, making them easy targets.
Lack of Skilled Personnel: There is a significant skills gap in the industry, with a shortage of professionals who understand the nuances of both IT and OT security.
IEC 62443: The Rosetta Stone for Industrial Cybersecurity
In this complex and challenging environment, the IEC 62443 series of standards provides a much-needed framework for establishing a comprehensive cybersecurity management system (CSMS) for IACS. Developed by a global team of experts from various industries, it offers a risk-based approach to security that is adaptable to different organizational needs and threat landscapes.
A Holistic Framework for a Converged World:
IEC 62443 is not a single document but a collection of standards and technical reports organized into four main categories:
General: This section provides the foundational concepts, models, and terminology used throughout the series.
Policies and Procedures: These documents outline the requirements for creating and maintaining a robust security program, including patch management and the security of IACS service providers.
System: This category focuses on the technical security requirements for IACS systems, including security levels and the implementation of zones and conduits.
Component: These standards specify the security requirements for the individual components that make up an IACS, such as embedded devices and software applications.
Core Principles of IEC 62443: Building a Defensible Architecture
At its core, IEC 62443 is built upon several fundamental principles that guide the implementation of a robust security posture.
Defense in Depth: A Multi-Layered Security Approach
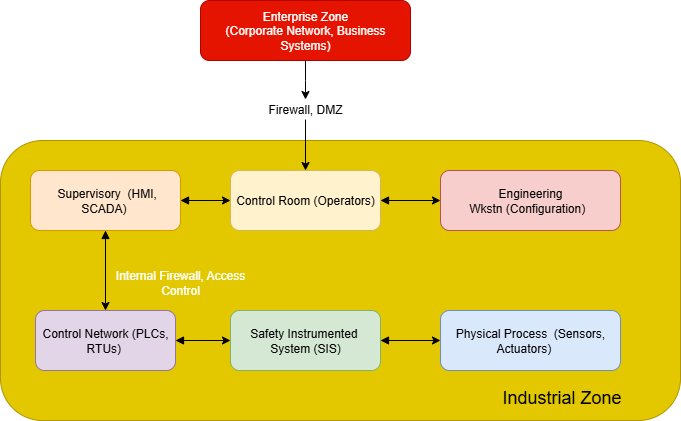
The concept of “defense in depth” is central to the IEC 62443 philosophy. It advocates for a layered security architecture where multiple, independent security controls are implemented to protect critical assets. If one layer is breached, the subsequent layers provide additional barriers, slowing down or even preventing an attacker from reaching their ultimate target. This is in stark contrast to the outdated “perimeter-only” security model, which is no longer effective in today’s interconnected world.
Block Diagram: Defense in Depth in a Converged OT/IT Environment
Zones and Conduits: Segmenting for Security
To effectively implement defense in depth, IEC 62443 introduces the concepts of zones and conduits.
Zones are logical groupings of assets that share common security requirements. For example, a group of PLCs controlling a specific manufacturing process could be placed in a single zone. By segmenting the network into zones, organizations can isolate critical assets and apply targeted security controls.
Conduits are the communication pathways between zones. All traffic flowing between zones must pass through a conduit, which allows for the implementation of security controls to monitor and restrict communication. This prevents unauthorized access and limits the lateral movement of attackers.
The implementation of zones and conduits is a fundamental step in building a secure IACS architecture. It allows for a granular approach to security, where the level of protection is tailored to the criticality of the assets within each zone.
The Security Lifecycle: A Continuous Process of Improvement
IEC 62443 emphasizes that cybersecurity is not a one-time project but a continuous lifecycle that requires ongoing management and improvement. The standard defines a comprehensive security lifecycle that encompasses all phases of an IACS, from initial design and implementation to operation, maintenance, and decommissioning.
The Key Phases of the IEC 62443 Security Lifecycle:
Assess: This phase involves identifying and assessing the risks to the IACS. This includes conducting a thorough inventory of all assets, identifying potential threats and vulnerabilities, and evaluating the potential impact of a security breach.
Implement: Based on the risk assessment, appropriate security controls are implemented to mitigate the identified risks. This can include a combination of technical controls, such as firewalls and intrusion detection systems, and procedural controls, such as access control policies and security awareness training.
Maintain: This is a critical and ongoing phase that involves monitoring the effectiveness of the implemented security controls, managing patches and updates, and responding to security incidents. Regular security audits and assessments are also essential to ensure that the security posture remains effective over time.
This cyclical approach ensures that security is an integral part of the IACS lifecycle and that the organization’s defenses are continuously adapted to the evolving threat landscape.
Shared Responsibility: A Collaborative Approach to Security
A key tenet of IEC 62443 is the principle of shared responsibility. In the complex ecosystem of a modern industrial enterprise, no single entity can be solely responsible for cybersecurity. Instead, it is a collaborative effort that requires the active participation of all stakeholders, including:
Asset Owners: The organizations that own and operate the IACS are ultimately responsible for the security of their systems. They must define the security policies, conduct risk assessments, and ensure that appropriate security controls are in place.
System Integrators: These are the companies that design, build, and install the IACS. They have a responsibility to ensure that the systems are designed and implemented in a secure manner, following the principles of IEC 62443.
Product Suppliers: The vendors who develop the hardware and software components used in the IACS have a critical role to play in building security into their products from the ground up. This includes following a secure development lifecycle and providing timely security patches and updates.
By fostering a culture of shared responsibility, IEC 62443 helps to ensure that security is considered at every stage of the IACS lifecycle, from the initial design of a single component to the ongoing operation of a complex industrial facility.
The Four Pillars of IEC 62443 Implementation: A Practical Guide
Implementing the IEC 62443 standard can seem like a daunting task, but it can be broken down into a series of manageable steps. The following four pillars provide a practical guide for organizations embarking on their IEC 62443 journey.
Security Program and Risk Management (IEC 62443-2-1): The foundation of any successful cybersecurity program is a well-defined security program and a robust risk management framework. This involves establishing clear security policies and procedures, defining roles and responsibilities, and conducting regular risk assessments to identify and prioritize security risks.
Secure Architecture and Segmentation (IEC 62443-3-2 & 3-3): As discussed earlier, the implementation of zones and conduits is a critical step in building a secure IACS architecture. This involves segmenting the network into logical zones based on criticality and implementing security controls at the boundaries between zones to control the flow of traffic.
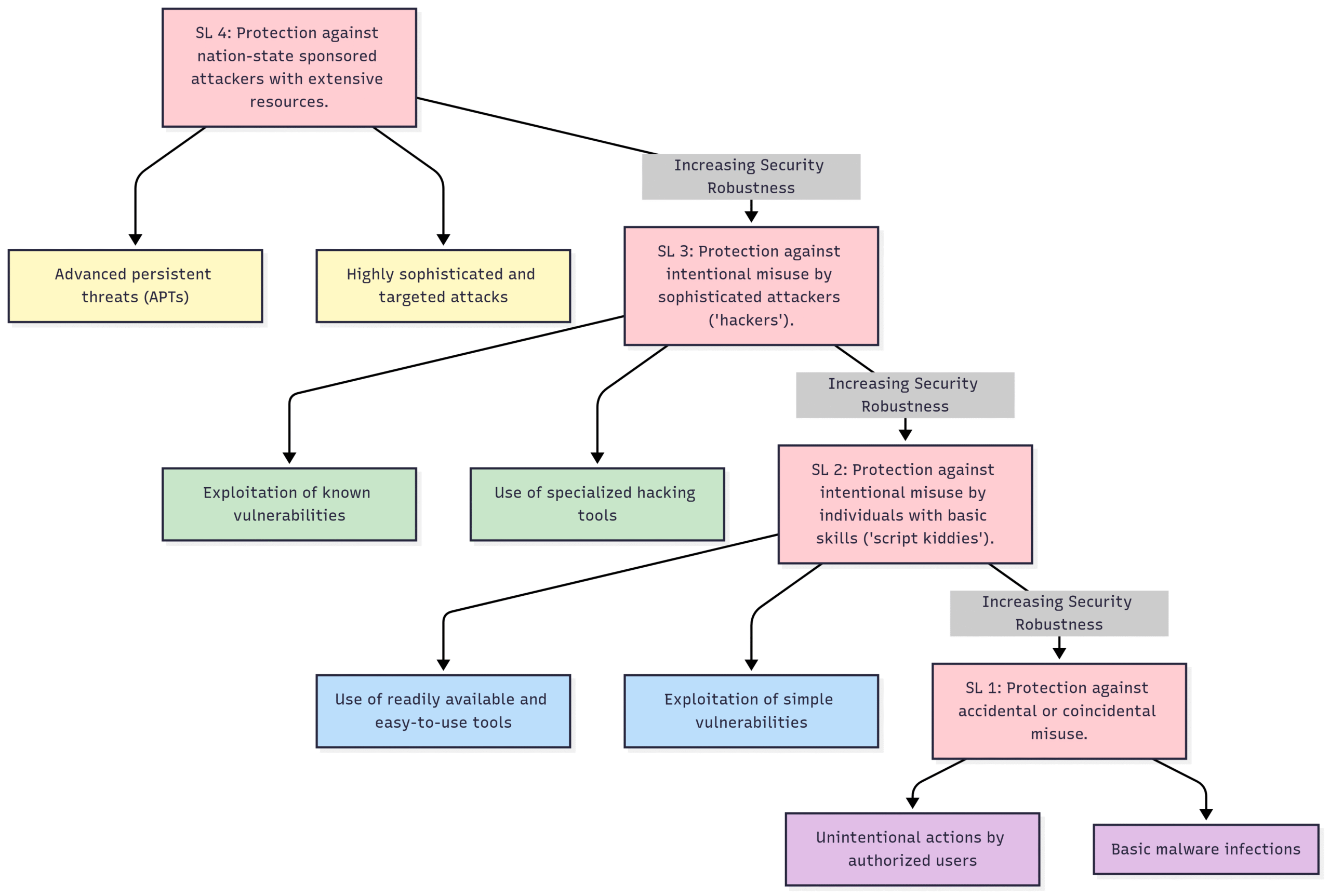
Security Levels and Foundational Requirements (IEC 62443-3-3 & 4-2): IEC 62443 defines four security levels (SL 1-4) that provide a target for the level of security required for a particular zone or system. These security levels are based on the potential impact of a security breach and the sophistication of the expected threat actor. The standard also defines a set of foundational requirements that must be met to achieve each security level.
Block Diagram: IEC 62443 Security Levels
Secure Product Development Lifecycle (IEC 62443-4-1): For product suppliers, adhering to a secure product development lifecycle is paramount. This involves integrating security into every phase of the product development process, from initial design and coding to testing and deployment. This helps to ensure that products are free from vulnerabilities and are resilient to cyberattacks.
By focusing on these four pillars, organizations can systematically implement the IEC 62443 standard and build a strong and sustainable cybersecurity posture for their converged OT/IT environments.
The Future of OT/IT Convergence and the Evolving Role of IEC 62443
The convergence of OT and IT is not a fleeting trend but a fundamental shift in the way industries operate. As this convergence deepens, driven by technologies like the Industrial Internet of Things (IIoT), artificial intelligence (AI), and cloud computing, the importance of a robust cybersecurity framework like IEC 62443 will only continue to grow.
The standard itself is a living document, continuously evolving to address the emerging threats and challenges of the digital age. Future revisions of IEC 62443 are likely to place an even greater emphasis on areas such as:
Cloud Security for OT: As more OT data and applications move to the cloud, there will be a need for specific guidance on securing these cloud-based environments.
The Security of IIoT Devices: The proliferation of IIoT devices creates a massive new attack surface. IEC 62443 will need to provide clear guidelines for securing these devices throughout their lifecycle.
Supply Chain Security: The interconnected nature of modern supply chains means that a vulnerability in a single supplier can have a ripple effect across an entire industry. IEC 62443 will play a crucial role in establishing a framework for managing supply chain risk.
Integration with Other Standards: As the cybersecurity landscape becomes more complex, there will be a growing need for alignment and integration between different standards and frameworks. IEC 62443 will need to continue to work in harmony with other relevant standards, such as the NIST Cybersecurity Framework.
Conclusion: A Secure Foundation for the Fourth Industrial Revolution
The convergence of OT and IT represents a pivotal moment in the history of industrial automation. It holds the promise of a future where industries are more efficient, more agile, and more innovative than ever before. However, this future can only be realized if we build it on a secure foundation.
The IEC 62443 series of standards provides that foundation. It is a comprehensive, risk-based framework that empowers organizations to navigate the complexities of OT/IT convergence and build a resilient and defensible security posture for their critical infrastructure. By embracing the principles of defense in depth, zones and conduits, and the security lifecycle, and by fostering a culture of shared responsibility, organizations can unlock the full potential of OT/IT convergence while safeguarding their operations from the ever-present threat of cyberattacks. In the dawning age of the Fourth Industrial Revolution, IEC 62443 is not just a standard; it is an essential enabler of a secure and prosperous industrial future.